NSE6_FML-6.2 Exam Details
-
Exam Code
:NSE6_FML-6.2 -
Exam Name
:Fortinet NSE 6 - FortiMail 6.2 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:30 Q&As -
Last Updated
:Jan 13, 2026
Fortinet NSE6_FML-6.2 Online Questions & Answers
-
Question 1:
Refer to the exhibit.
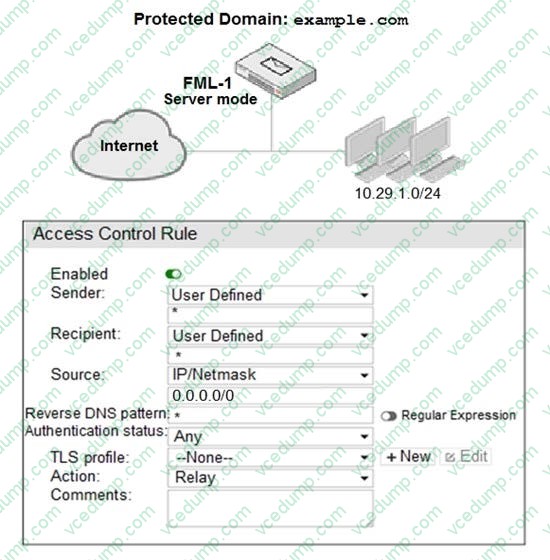
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain. Which two settings should be used to configure the access receive rule? (Choose two.)
A. The Recipient pattern should be set to *@example.com
B. The Authentication status should be set to Authenticated
C. The Sender IP/netmask should be set to 10.29.1.0/24
D. The Action should be set to Reject -
Question 2:
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?
A. Resource profiles
B. Domain-level service settings
C. Access profiles
D. Address book management options -
Question 3:
Refer to the exhibit.
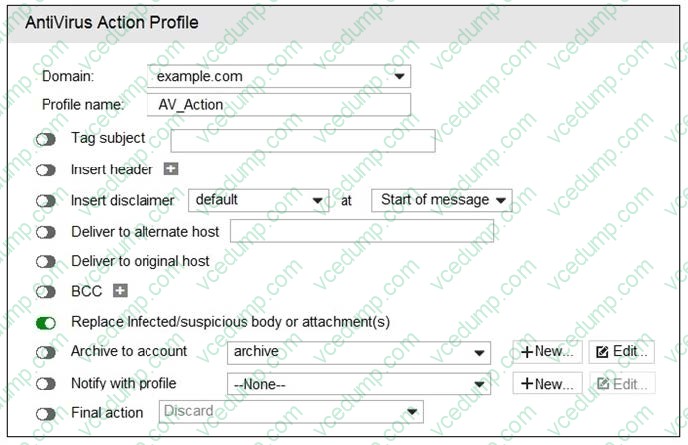
What are two expected outcomes if FortiMail applies this antivirus action profile to an email? (Choose two.)
A. Virus content will be removed from the email
B. A replacement message will be added to the email
C. The sanitized email will be sent to the recipient's personal quarantine
D. The administrator will be notified of the virus detection -
Question 4:
While testing outbound MTA functionality, an administrator discovers that all outbound email is being processed using policy IDs 1:2:0. Which two reasons explain why the last policy ID value is 0? (Choose two.)
A. Outbound email is being rejected
B. IP policy ID 2 has the exclusive flag set
C. There are no outgoing recipient policies configured
D. There are no access delivery rules configured for outbound email -
Question 5:
Which FortiMail option removes embedded code components in Microsoft Word, while maintaining the original file format?
A. Behavior analysis
B. Impersonation analysis
C. Content disarm and reconstruction
D. Header analysis -
Question 6:
Which two CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
A. execute formatmaildisk
B. execute formatmaildisk_backup
C. execute formatlogdisk
D. execute partitionlogdisk 40 -
Question 7:
Refer to the exhibit.
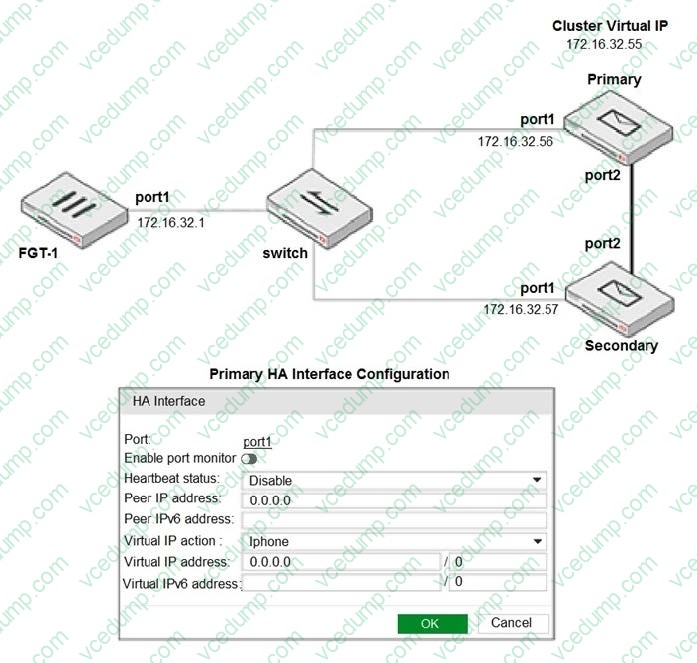
The exhibit shows a FortiMail active-passive setup.
Which three actions are recommended when configuring the primary FortiMail HA interface? (Choose three.)
A. Disable Enable port monitor
B. In the Heartbeat status drop-down list, select Primary
C. In the Peer IP address field, type 172.16.32.57
D. In the Virtual IP action drop-down list, select Use
E. In the Virtual IP address field, type 172.16.32.55/24 -
Question 8:
Refer to the exhibit.
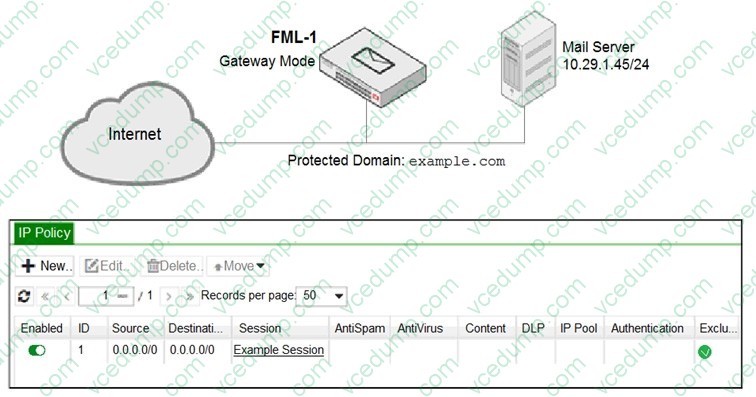
An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the mail server starts filling up with undeliverable email. What two changes must the administrator make to fix this issue? (Choose two.)
A. Apply a session profile with sender reputation disabled on a separate IP policy for outbound sessions
B. Clear the sender reputation database using the CLI
C. Create an outbound recipient policy to bypass outbound email from session profile inspections
D. Disable the exclusive flag in IP policy ID 1 -
Question 9:
Refer to the exhibit.
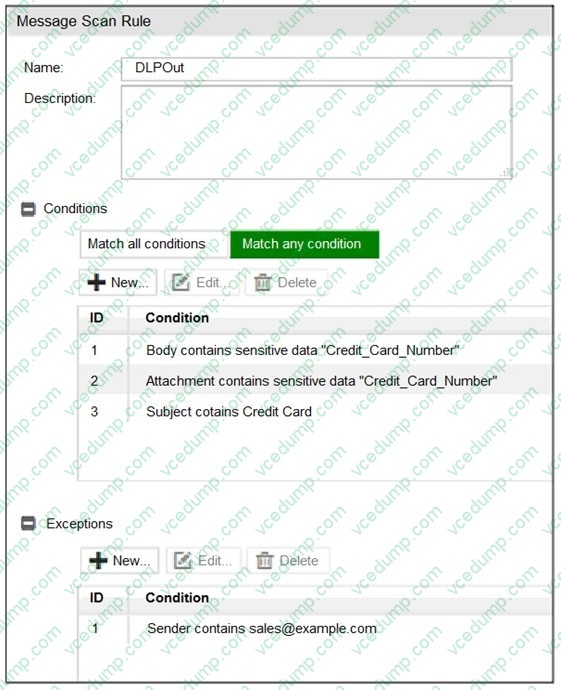
Which two message types will trigger this DLP scan rule? (Choose two.)
A. An email message with a subject that contains the term "credit card" will trigger this scan rule
B. An email that contains credit card numbers in the body, attachment, and subject will trigger this scan rule
C. An email message that contains credit card numbers in the body will trigger this scan rule
D. An email sent from sales@internal.lab will trigger this scan rule, even without matching any conditions -
Question 10:
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9. Which two scenarios will generate this policy ID? (Choose two.)
A. Email was processed using IP policy ID 4
B. Incoming recipient policy ID 9 has the exclusive flag set
C. FortiMail applies the default behavior for relaying inbound email
D. FortiMail configuration is missing an access delivery rule
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE6_FML-6.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.