Exam Details
Exam Code
:NSE5Exam Name
:Fortinet Network Security Expert 5 Written Exam (500)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:320 Q&AsLast Updated
:Jul 12, 2025
Fortinet Fortinet Certifications NSE5 Questions & Answers
-
Question 291:
Which of the following describes the difference between the ban and quarantine actions?
A. A ban action prevents future transactions using the same protocol which triggered the ban. A qarantine action blocks all future transactions, regardless of the protocol.
B. A ban action blocks the transaction. A quarantine action archives the data.
C. A ban action has a finite duration. A quarantine action must be removed by an administrator.
D. A ban action is used for known users. A quarantine action is used for unknown users.
-
Question 292:
Examine the following log message for IPS and identify the valid responses below. (Select all that apply.)
2012-07-01 09:54:28 oid=2 log_id=18433 type=ips subtype=anomaly pri=alert vd=root severity="critical" src="192.168.3.168" dst="192.168.3.170" src_int="port2" serial=0 status="detected" proto=1 service="icmp" count=1 attack_name="icmp_flood" icmp_id="0xa8a4" icmp_type="0x08" icmp_code="0x00" attack_id=16777316 sensor="1" ref="http://www.fortinet.com/ids/VID16777316" msg="anomaly: icmp_flood, 51 > threshold 50"
A. The target is 192.168.3.168.
B. The target is 192.168.3.170.
C. The attack was detected and blocked.
D. The attack was detected only.
E. The attack was TCP based.
-
Question 293:
The command structure of the CLI on a FortiGate unit consists of commands, objects, branches, tables and parameters.
Which of the following items describes port1?
A. A command.
B. An object.
C. A table.
D. A parameter.
-
Question 294:
Which of the following methods is best suited to changing device level settings on existing and future managed FortiGate devices?
A. Configure each managed FortiGate device and install.
B. Configure using provisioning templates and install.
C. Configure using CLI-only objects and install.
D. Configure a script for these settings and install.
-
Question 295:
FortiGate units are preconfigured with four default protection profiles. These protection profiles are used to control the type of content inspection to be performed.
What action must be taken for one of these profiles to become active?
A. The protection profile must be assigned to a firewall policy.
B. The "Use Protection Profile" option must be selected in the Web Config tool under the sections for AntiVirus, IPS, WebFilter, and AntiSpam.
C. The protection profile must be set as the Active Protection Profile.
D. All of the above.
-
Question 296:
Examine the exhibit shown below; then answer the question following it.
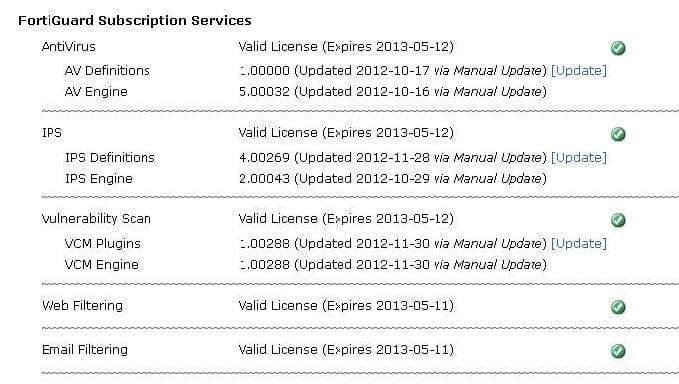
Which of the following statements best describes the green status indicators that appear next to the different FortiGuard Distribution Network services as illustrated in the exhibit?
A. They indicate that the FortiGate unit is able to connect to the FortiGuard Distribution Network.
B. They indicate that the FortiGate unit has the latest updates that are available from the FortiGuard Distribution Network.
C. They indicate that updates are available and should be downloaded from the FortiGuard Distribution Network to the FortiGate unit.
D. They indicate that the FortiGate unit is in the process of downloading updates from the FortiGuard Distribution Network.
-
Question 297:
The ordering of firewall policies is very important. Policies can be re-ordered within the FortiGate unit's GUI
and also using the CLI. The command used in the CLI to perform this function is __________ .
A. set order
B. edit policy
C. reorder
D. move
-
Question 298:
Which two statements describe a "modified" device settings' status in the Configuration and Installation Status widget of a managed FortiGate device? (Choose two.)
A. Configuration changes were made directly on the managed device.
B. Configuration changes were made from Device Manager for a managed FortiGate device.
C. Configuration changes were installed to a managed FortiGate device.
D. Configuration changes in Device Manager no longer match the latest revision in the device's revision history.
-
Question 299:
What output profiles can you configure for report event notifications? (Choose two.)
A. SMS
B. Forward to another FortiAnalyzer device
C. Upload to a server
D. Email
-
Question 300:
Which statements are true of Administrative Domains (ADOMs) in FortiAnalyzer? (Choose two.)
A. ADOMs are enabled by default.
B. ADOMs constrain other administrator's access privileges to a subset of devices in the device list.
C. Once enabled, the Device Manager, FortiView, Event Management, and Reports tab display per ADOM.
D. All administrators can create ADOMs--not just the admin administrator.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.