Exam Details
Exam Code
:NSE5Exam Name
:Fortinet Network Security Expert 5 Written Exam (500)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:320 Q&AsLast Updated
:Jul 12, 2025
Fortinet Fortinet Certifications NSE5 Questions & Answers
-
Question 261:
Which two statements are correct regarding header and footer policies? (Choose two.)
A. Header and footer policies can only be created in the root ADOM.
B. Header and footer policies can only be created in the global ADOM.
C. Header and footer policies are created in policy packages and assigned to ADOM policy packages.
D. Header and footer policies can be modified in the assigned ADOM policy package.
-
Question 262:
The following ban list entry is displayed through the CLI. get user ban list id cause src-ip-addr dst-ip-addr expires created 531 protect_client 10.177.0.21 207.1.17.1 indefinite Wed Dec 24 :21:33 2008 Based on this command output, which of the following statements is correct?
A. The administrator has specified the Attack and Victim Address method for the quarantine.
B. This diagnostic entry results from the administrator running the diag ips log test command. This command has no effect on traffic.
C. A DLP rule has been matched.
D. An attack has been repeated more than once during the holddown period; the expiry time has been reset to indefinite.
-
Question 263:
How is traffic routed onto an SSL VPN tunnel from the FortiGate unit side?
A. A static route must be configured by the administrator using the ssl.root interface as the outgoing interface.
B. Assignment of an IP address to the client causes a host route to be added to the FortiGate unit's kernel routing table.
C. A route back to the SSLVPN IP pool is automatically created on the FortiGate unit.
D. The FortiGate unit adds a route based upon the destination address in the SSL VPN firewall policy.
-
Question 264:
Which statements are true regarding content archiving, also known as Data Leak Prevention (DLP) archiving? (Choose two.)
A. Allows full and summary archiving.
B. It is configured globally for all policies.
C. The default behavior is to do full archiving.
D. The DLP engine examines email, FTP, NNTP, and web traffic.
-
Question 265:
Review the output of the command get router info routing-table all shown in the Exhibit below; then answer the question following it.
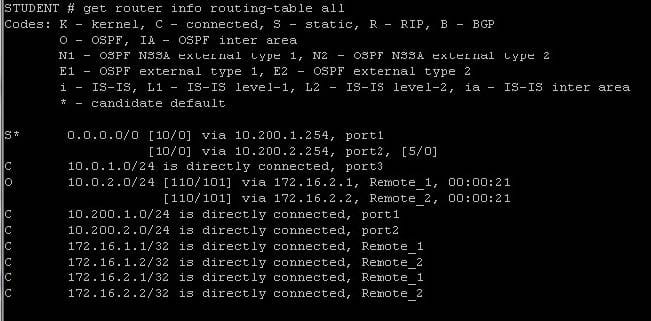
Which one of the following statements correctly describes this output?
A. The two routes to the 10.0.2.0/24 subnet are ECMP routes and traffic will be load balanced based on the configured ECMP settings.
B. The route to the 10.0.2.0/24 subnet via interface Remote_1 is the active and the route via Remote_2 is the backup.
C. OSPF does not support ECMP therefore only the first route to subnet 10.0.1.0/24 is used.
D. 172.16.2.1 is the preferred gateway for subnet 10.0.2.0/24.
-
Question 266:
A network administrator needs to implement dynamic route redundancy between a FortiGate unit located in a remote office and a FortiGate unit located in the central office.
The remote office accesses central resources using IPSec VPN tunnels through two different Internet providers.
What is the best method for allowing the remote office access to the resources through the FortiGate unit used at the central office?
A. Use two or more route-based IPSec VPN tunnels and enable OSPF on the IPSec virtual interfaces.
B. Use two or more policy-based IPSec VPN tunnels and enable OSPF on the IPSec virtual interfaces.
C. Use route-based VPNs on the central office FortiGate unit to advertise routes with a dynamic routing protocol and use a policy-based VPN on the remote office with two or more static default routes.
D. Dynamic routing protocols cannot be used over IPSec VPN tunnels.
-
Question 267:
Examine the two static routes to the same destination subnet 172.20.168.0/24 as shown below; then answer the question following it. config router static edit 1 set dst 172.20.168.0 255.255.255.0 set distance 20 set priority 10 set device port1 next edit 2
set dst 172.20.168.0 255.255.255.0 set distance 20 set priority 20
set device port2 next end Which of the following statements correctly describes the static routing configuration provided above?
A. The FortiGate unit will evenly share the traffic to 172.20.168.0/24 through both routes.
B. The FortiGate unit will share the traffic to 172.20.168.0/24 through both routes, but the port2 route will carry approximately twice as much of the traffic.
C. The FortiGate unit will send all the traffic to 172.20.168.0/24 through port1.
D. Only the route that is using port1 will show up in the routing table.
-
Question 268:
What are the main management wizards used in Device Manager?
A. Add Device, Provisioning Templates, and View Installation
B. Add Device, Install Wizard, and Import Policy
C. Script, Configuring CLI-Objects, and Re-install Policy
D. View Installation, Import Policy, and Script
-
Question 269:
The transfer of encrypted files or the use of encrypted protocols between users and servers on the internet can frustrate the efforts of administrators attempting to monitor traffic passing through the FortiGate unit and ensuring user compliance to corporate rules.
Which of the following items will allow the administrator to control the transfer of encrypted data through the FortiGate unit? (Select all that apply.)
A. Encrypted protocols can be scanned through the use of the SSL proxy.
B. DLP rules can be used to block the transmission of encrypted files.
C. Firewall authentication can be enabled in the firewall policy, preventing the use of encrypted communications channels.
D. Application control can be used to monitor the use of encrypted protocols; alerts can be sent to the administrator through email when the use of encrypted protocols is attempted.
-
Question 270:
Review the CLI configuration below for an IPS sensor and identify the correct statements regarding this
configuration from the choices below. (Select all that apply.)
config ips sensor
edit "LINUX_SERVER"
set comment ''
set replacemsg-group ''
set log enable
config entries
edit 1
set action default
set application all
set location server
set log enable
set log-packet enable
set os Linux
set protocol all set quarantine none set severity all
set status default
next
end
next
end
A. The sensor will log all server attacks for all operating systems.
B. The sensor will include a PCAP file with a trace of the matching packets in the log message of any matched signature.
C. The sensor will match all traffic from the address object "LINUX_SERVER".
D. The sensor will reset all connections that match these signatures.
E. The sensor only filters which IPS signatures to apply to the selected firewall policy.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.