Exam Details
Exam Code
:NSE5Exam Name
:Fortinet Network Security Expert 5 Written Exam (500)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:320 Q&AsLast Updated
:Jul 12, 2025
Fortinet Fortinet Certifications NSE5 Questions & Answers
-
Question 11:
Which of the following components are contained in all FortiGate units from the FG50 models and up? (Select all that apply.)
A. FortiASIC content processor.
B. Hard Drive.
C. Gigabit network interfaces.
D. Serial console port.
-
Question 12:
Which two statements are correct regarding the FortiManager HA cluster? (Choose two.)
A. HA synchronization is done over TCP port 5199.
B. HA synchronization is done over TCP port TCP 703.
C. Changes to the configuration database are possible from the HA secondary FortiManager, which will synchronize the changes to other cluster devices.
D. Changes to the configuration database are possible only from the HA primary FortiManager, which will synchronize the changes to other cluster devices.
-
Question 13:
By default, what happens when a log file reaches its maximum file size?
A. FortiAnalyzer overwrites the log files.
B. FortiAnalyzer stops logging.
C. FortiAnalyzer rolls the active log by renaming the file.
D. FortiAnalyzer forwards logs to syslog.
-
Question 14:
The FortiGate unit can be configured to allow authentication to a RADIUS server. The RADIUS server can use several different authentication protocols during the authentication process.
Which of the following are valid authentication protocols that can be used when a user authenticates to the RADIUS server? (Select all that apply.)
A. MS-CHAP-V2 (Microsoft Challenge-Handshake Authentication Protocol v2)
B. PAP (Password Authentication Protocol)
C. CHAP (Challenge-Handshake Authentication Protocol)
D. MS-CHAP (Microsoft Challenge-Handshake Authentication Protocol v1)
E. FAP (FortiGate Authentication Protocol)
-
Question 15:
In addition to AntiVirus services, the FortiGuard Subscription Services provide IPS, Web Filtering, and ___________ services.
A. antispam
-
Question 16:
In an IPSec gateway-to-gateway configuration, two FortiGate units create a VPN tunnel between two separate private networks.
Which of the following configuration steps must be performed on both FortiGate units to support this configuration? (Select all that apply.)
A. Create firewall policies to control traffic between the IP source and destination address.
B. Configure the appropriate user groups on the FortiGate units to allow users access to the IPSec VPN connection.
C. Set the operating mode of the FortiGate unit to IPSec VPN mode.
D. Define the Phase 2 parameters that the FortiGate unit needs to create a VPN tunnel with the remote peer.
E. Define the Phase 1 parameters that the FortiGate unit needs to authenticate the remote peers.
-
Question 17:
What statements are true regarding FortiAnalyzer's treatment of high availability (HA) clusters? (Choose two.)
A. FortiAnalyzer distinguishes different devices by their serial number.
B. FortiAnalyzer receives logs from all devices in a cluster.
C. FortiAnalyzer receives logs only from the primary device in the cluster.
D. FortiAnalyzer only needs to know the serial number of the primary device in the cluster--it automatically discovers the other devices.
-
Question 18:
In the Tunnel Mode widget of the web portal, the administrator has configured an IP Pool and enabled split tunneling.
Which of the following statements is true about the IP address used by the SSL VPN client?
A. The IP pool specified in the SSL-VPN Tunnel Mode Widget Options will override the IP address range defined in the SSL-VPN Settings.
B. Because split tunneling is enabled, no IP address needs to be assigned for the SSL VPN tunnel to be established.
C. The IP address range specified in SSL-VPN Settings will override the IP address range in the SSL-VPN Tunnel Mode Widget Options.
-
Question 19:
An issue could potentially occur when clicking Connect to start tunnel mode SSL VPN. The tunnel will start up for a few seconds, then shut down.
Which of the following statements best describes how to resolve this issue?
A. This user does not have permission to enable tunnel mode. Make sure that the tunnel mode widget has been added to that user's web portal.
B. This FortiGate unit may have multiple Internet connections. To avoid this problem, use the appropriate CLI command to bind the SSL VPN connection to the original incoming interface.
C. Check the SSL adaptor on the host machine. If necessary, uninstall and reinstall the adaptor from the tunnel mode portal.
D. Make sure that only Internet Explorer is used. All other browsers are unsupported.
-
Question 20:
Examine the Exhibit shown below; then answer the question following it.
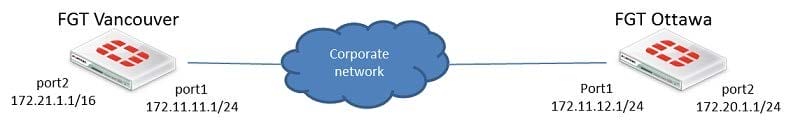
The Vancouver FortiGate unit initially had the following information in its routing table: S 172.20.0.0/16 [10/0] via 172.21.1.2, port2 C 172.21.0.0/16 is directly connected, port2 C 172.11.11.0/24 is directly connected, port1 Afterwards, the following static route was added: config router static edit 6 set dst 172.20.1.0 255.255.255.0 set priority 0 set device port1 set gateway 172.11.12.1 next end Since this change, the new static route is NOT showing up in the routing table. Given the information
provided, which of the following describes the cause of this problem?
A. The subnet 172.20.1.0/24 is overlapped with the subnet of one static route that is already in the routing table (172.20.0.0/16), so, we need to enable allow-subnet-overlap first.
B. The 'gateway' IP address is NOT in the same subnet as the IP address of port1.
C. The priority is 0, which means that the route will remain inactive.
D. The static route configuration is missing the distance setting.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.