Exam Details
Exam Code
:NSE4Exam Name
:Fortinet Network Security Expert 4 Written Exam (400)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:301 Q&AsLast Updated
:Apr 21, 2024
Fortinet Fortinet Certifications NSE4 Questions & Answers
-
Question 141:
What determines whether a log message is generated or not?
A. Firewall policy setting
B. Log Settings in the GUI
C. 'config log' command in the CLI
D. Syslog
E. Webtrends
-
Question 142:
Which statement best describes what the FortiGate hardware acceleration processors main task is?
A. Offload traffic processing tasks from the main CPU.
B. Offload management tasks from the main CPU.
C. Compress and optimize the network traffic.
D. Increase maximum bandwidth available in a FortiGate interface.
-
Question 143:
Which of the following statements describes the objectives of the gratuitous ARP packets sent by an HA cluster?
A. To synchronize the ARp tables in all the FortiGate Unis that are part of the HA cluster.
B. To notify the network switches that a new HA master unit has been elected.
C. To notify the master unit that the slave devices are still up and alive.
D. To notify the master unit about the physical MAC addresses of the slave units.
-
Question 144:
What methods can be used to access the FortiGate CLI? (Choose two.)
A. Using SNMP.
B. A direct connection to the serial console port.
C. Using the CLI console widget in the GUI.
D. Using RCP.
-
Question 145:
A firewall policy has been configured for the internal email server to receive email from external parties through SMTP. Exhibits A and B show the antivirus and email filter profiles applied to this policy.
Exhibit A

Exhibit B: What is the correct behavior when the email attachment is detected as a virus by the FortiGate antivirus engine?
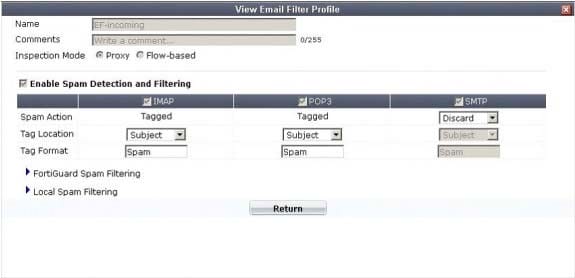
A. The FortiGate unit will remove the infected file and deliver the email with a replacement message to alert the recipient that the original attachment was infected.
B. The FortiGate unit will reject the infected email and the sender will receive a failed delivery message.
C. The FortiGate unit will remove the infected file and add a replacement message. Both sender and recipient are notified that the infected file has been removed.
D. The FortiGate unit will reject the infected email and notify the sender.
-
Question 146:
The FortiGate port1 is connected to the Internet. The FortiGate port2 is connected to the internal network. Examine the firewall configuration shown in the exhibit; then answer the question below.
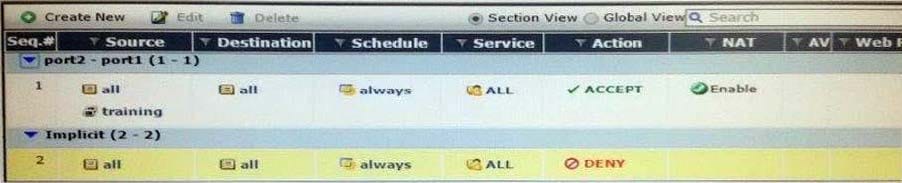
Based on the firewall configuration illustrated in the exhibit, which statement is correct?
A. A user that has not authenticated can access the Internet using any protocol that does not trigger an authentication challenge.
B. A user that has not authenticated can access the Internet using any protocol except HTTP, HTTPS, Telnet, and FTP.
C. A user must authenticate using the HTTP, HTTPS, SSH, FTP, or Telnet protocol before they can access all Internet services.
D. DNS Internet access is always allowed, even for users that have not authenticated.
-
Question 147:
Examine this log entry.
What does the log indicate? (Choose three.)
date=2013-12-04 time=09:30:18 logid=0100032001 type=event subtype=system level=information vd="root" user="admin" ui=http(192.168.1.112) action=login status=success reason=none profile="super_admin" msg="Administrator admin logged in successfully from http(192.168.1.112)"
A. In the GUI, the log entry was located under "Log and Report > Event Log > User".
B. In the GUI, the log entry was located under "Log and Report > Event Log > System".
C. In the GUI, the log entry was located under "Log and Report > Traffic Log > Local Traffic".
D. The connection was encrypted.
E. The connection was unencrypted.
F. The IP of the FortiGate interface that "admin" connected to was 192.168.1.112.
G. The IP of the computer that "admin" connected from was 192.168.1.112.
-
Question 148:
Caching improves performance by reducing FortiGate unit requests to the FortiGuard server. Which of the following statements are correct regarding the caching of FortiGuard responses?
A. Caching is available for web filtering, antispam, and IPS requests.
B. The cache uses a small portion of the FortiGate system memory.
C. When the cache is full, the least recently used IP address or URL is deleted from the cache.
D. An administrator can configure the number of seconds to store information in the cache before the FortiGate unit contacts the FortiGuard server again.
E. The size of the cache will increase to accommodate any number of cached queries.
-
Question 149:
What are examples of correct syntax for the session table diagnostics command? (Choose two.)
A. diagnose sys session filter clear
B. diagnose sys session src 10.0.1.254
C. diagnose sys session filter
D. diagnose sys session filter list dst.
-
Question 150:
What is the default criteria for selecting the HA master unit in a HA cluster?
A. port monitor, priority, uptime, serial number
B. Port monitor, uptime, priority, serial number
C. Priority, uptime, port monitor, serial number
D. uptime, priority, port monitor, serial number
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.