Exam Details
Exam Code
:MS-500Exam Name
:Microsoft 365 Security AdministrationCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:367 Q&AsLast Updated
:Sep 11, 2023
Microsoft Microsoft Certifications MS-500 Questions & Answers
-
Question 81:
Your network contains an on-premises Active Directory domain named contoso.local that has a forest functional level of Windows Server 2008 R2.
You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to install Azure AD Connect and enable single sign-on (SSO).
You need to prepare the domain to support SSO. The solution must minimize administrative effort.
What should you do?
A. Raise the forest functional level to Windows Server 2016.
B. Modify the UPN suffix of all domain users.
C. Populate the mail attribute of all domain users.
D. Rename the domain.
-
Question 82:
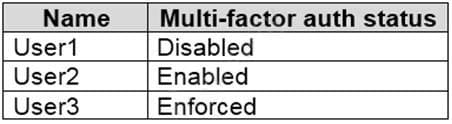
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
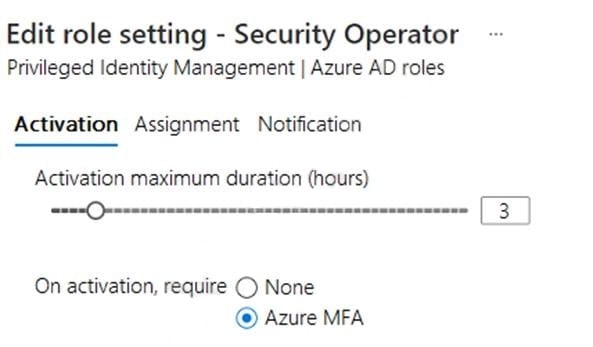
You configure the Security Operator role in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.
You add assignments to the Security Operator role as shown in the following table.
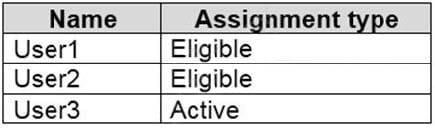
Which users can activate the Security Operator role?
A. User2 only
B. User3 only
C. User1 and User2 only
D. User2 and User3 only
E. User1, User2, and User3
-
Question 83:
You create an Azure Sentinel workspace.
You configure Azure Sentinel to ingest data from Azure Active Directory (Azure AD).
In the Azure Active Directory admin center, you discover Azure AD Identity Protection alerts. The Azure Sentinel workspace shows the status as shown in the following exhibit.
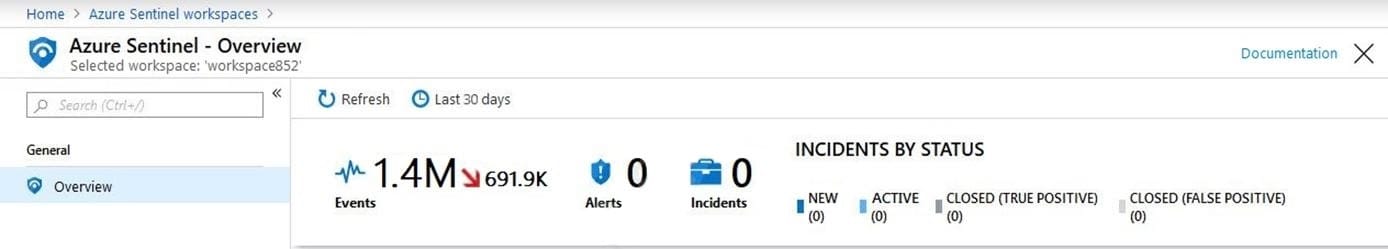
In Azure Log Analytics, you can see Azure AD data in the Azure Sentinel workspace.
What should you configure in Azure Sentinel to ensure that incidents are created for detected threats?
A. data connectors
B. rules
C. workbooks
D. hunting queries
-
Question 84:
You have a Microsoft 365 E5 subscription that has Microsoft 365 Defender enabled.
You plan to deploy a third-party app named App1 that will receive alert data from Microsoft 365 Defender.
Which format will Microsoft 365 Defender use to send the alert data to App1?
A. JSON
B. ZIP
C. XML
D. CSV
-
Question 85:
You have a Microsoft 365 E5 subscription and an Sentinel workspace named Sentinel1. You need to launch the Guided investigation Process Alerts notebooks = in Sentinel. What should you create first?
A. a Log Analytic workspace
B. a Kusto query
C. an Azure Machine learning workspace
D. an Azure logic app
-
Question 86:
You have a Microsoft 365 E5 subscription that has Microsoft Defender for Cloud Apps enabled. You need to create an alert in Defender for Cloud Apps when source code is shared externally.
Which type of policy should you create?
A. Cloud Discovery anomaly detection
B. file
C. access
D. activity
-
Question 87:
You have several Conditional Access policies that block noncompliant devices from connecting to services.
You need to identify which devices are blocked by which policies.
What should you use?
A. the Device compliance report in the Microsoft Endpoint Manager admin center
B. the Device compliance trends report in the Microsoft Endpoint Manager admin center
C. Activity log in the Cloud App Security admin center
D. the Conditional Access Insights and Reporting workbook in the Azure Active Directory admin center
-
Question 88:
You have a Microsoft 365 subscription named contoso.com.
You need to configure Microsoft OneDrive for Business external sharing to meet the following requirements:
1.
Enable file sharing for users that have a Microsoft account.
2.
Block file sharing for anonymous users. What should you do?
A. From Advanced settings for external sharing, select Allow or block sharing with people on specific domains and add contoso.com.
B. From the External sharing settings for OneDrive, select Only people in your organization.
C. From the External sharing settings for OneDrive, select Existing external users.
D. From the External sharing settings for OneDrive, select New and existing external users.
-
Question 89:
You have a hybrid Azure Active Directory (Azure AD) tenant that has pass- through authentication enabled.
You plan to implement Azure AD identity Protection and enable the user risk policy.
You need to configure the environment to support the user risk policy.
What should you do first?
A. Enable password hash synchronization.
B. Configure a conditional access policy.
C. Enforce the multi-factor authentication (MFA) registration policy.
D. Enable the sign-in risk policy.
-
Question 90:
You need to create an Azure Information Protection label to meet the following requirements:
1.
Content must expire after 21 days.
2.
Offline access must be allowed for 21 days only.
3.
Documents must be protected by using a cloud key.
4.
Authenticated users must be able to view content only.
To complete this task, sign in to the Microsoft 365 admin center.
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-500 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.