Exam Details
Exam Code
:MS-500Exam Name
:Microsoft 365 Security AdministrationCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:367 Q&AsLast Updated
:Sep 11, 2023
Microsoft Microsoft Certifications MS-500 Questions & Answers
-
Question 71:
You have a Microsoft 365 E5 subscription that contains 500 Windows 10 devices The subscription uses Microsoft Defender for Endpoint and is integrated with Microsoft Endpoint Manager. AJI the devices have Defender for Endpoint deployed.
You create a Conditional Access policy as shown in the following table.
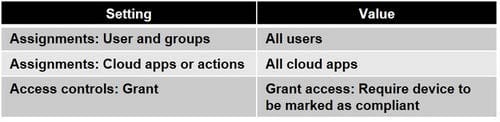
You need to ensure that devices that have a machine risk score of high are blocked. What should you do in Microsoft Endpoint Manager?
A. Apply a security baseline to all the devices.
B. Apply an endpoint detection and response policy to the subscription.
C. Configure the Compliance policy settings.
D. Apply a compliance policy to all the devices.
-
Question 72:
You have an Azure Active Directory (Azure AD) tenant that has a Microsoft 365 subscription
You recently configured the tenant to require multi factor authentication (MFA) for risky sign ins
You need to review the users who required MFA.
What should you do?
A. From the Microsoft 365 admin center, review a Security and Compliance report.
B. From the Azure Active Directory admin center, download the sign-ms to a CSV file
C. From the Microsoft 365 Compliance admin center, run an audit log search and download the results to a CSV file
D. From the Azure Active Directory admin center, review the Authentication methods activities.
-
Question 73:
You have a Microsoft 365 Enterprise E5 subscription.
You use Microsoft Defender for Endpoint.
You need to integrate Microsoft Defender for Office 365 and Microsoft Defender for Endpoint
Where should you configure the integration?
A. From the Microsoft 365 admin center, select Settings, and then select Services fit add-ins
B. From the Microsoft 365 Defender portal, select Settings and then select Security center.
C. From the Microsoft 365 admin center, select Reports and then select Security and Compliance
D. From the Microsoft 365 Defender portal, select Explorer and then select MDE Settings
-
Question 74:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that contains a user named User1.
The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1.
For User1, you select Confirm user compromised.
User1 can still sign in.
You need to prevent User1 from signing in. The solution must minimize the impact on users at a tower risk level.
Solution: From the Access settings, you select Block access for User1.
Does this meet the goal?
A. Yes
B. No
-
Question 75:
You have a Microsoft 365 subscription that contains several Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager.
You need to enable Microsoft Defender Exploit Guard (Microsoft Defender EG) on the devices.
Which type of device configuration profile should you use?
A. Endpoint protection
B. Device restrictions
C. Microsoft Defender for Endpoint
D. identity protection
-
Question 76:
You have multiple Microsoft 365 subscriptions.
You need to build an application that will retrieve the Microsoft Secure Score data of each subscription.
What should you use?
A. the Microsoft Defender for Endpoint API
B. the Microsoft Graph Security API
C. the Microsoft Office 365 Management API
D. the Azure Monitor REST API
-
Question 77:
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2. On January 1. you create the sensitivity label shown in the following table.
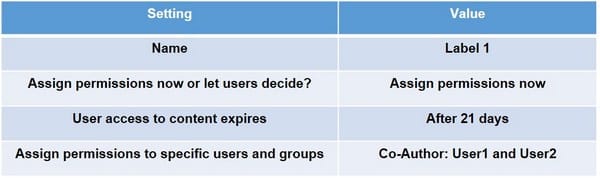
1.
On January 2, you publish label to User1.
2.
On January 3. User 1 creates a Microsoft Word document named Doc1 and applies Label to the document.
3.
On January 4. User2 edits Doc1.
4.
On January 15, you increase the content expiry period for Label to 28 days. When will access to Doc1 expire for User2?
A. January 23
B. January 24
C. January 25
D. January 31
-
Question 78:
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
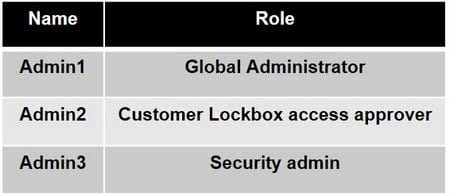
You enable Customer Lockbox.
Which users will be notified when a Microsoft support engineer requests access to the organization?
A. Admin1, Admin2. and Admin3
B. Admin2only
C. Admin2 and Admin3 only
D. Admin1 and Admin2 only
-
Question 79:
You have a Microsoft 365 E5 subscription.
You create a sensitivity label named Label 1 and publish Label1 to all users and groups.
You have the following files on a computer:
1.
File1.doc
2.
File2.docx
3.
File3.xlsx
4.
File4.txt
You need to identify which files can have Label1 applied. Which files should you identify?
A. File2.docx only
B. File1.doc. File2.docx. File3.xlsx. a
C. File1 .doc. File2.docx, and File3.xlsx only
D. File2.docx and File3.xlsx only
-
Question 80:
You have a Microsoft 365 tenant that has modern authentication enabled.
You have Windows 10, MacOS. Android, and iOS devices that are managed by using Microsoft Endpoint Manager. Some users have older email client applications that use Basic authentication to connect to Microsoft Exchange Online. You need to implement a solution to meet the following security requirements:
1.
Allow users to connect to Exchange Online only by using email client applications that support modern authentication protocols based on OAuth 2.0.
2.
Block connections to Exchange Online by any email client applications that do NOT support modern authentication.
What should you implement?
A. a conditional access policy in Azure Active Directory (Azure AD)
B. an OAuth app policy m Microsoft Defender for Cloud Apps
C. a compliance policy in Microsoft Endpoint Manager
D. an application control profile in Microsoft Endpoint Manager
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-500 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.