Exam Details
Exam Code
:MS-500Exam Name
:Microsoft 365 Security AdministrationCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:367 Q&AsLast Updated
:Sep 11, 2023
Microsoft Microsoft Certifications MS-500 Questions & Answers
-
Question 101:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that contains a user named User1.
The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1.
For User1, you select Confirm user compromised.
User1 can still sign in.
You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the sign-in risk policy to block access when the sign-in risk level is high.
Does this meet the goal?
A. Yes
B. No
-
Question 102:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that contains a user named User1.
The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1.
For User1, you select Confirm user compromised.
User1 can still sign in.
You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the user risk policy to block access when the user risk level is high.
Does this meet the goal?
A. Yes
B. No
-
Question 103:
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and an Office 365 connector.
From the workspace, you plan to create a scheduled query rule that will use a custom query. The rule will be used to generate alerts when inbound access to Office 365 from specific user accounts is detected.
You need to ensure that when multiple alerts are generated by the rule, the alerts are consolidated as a single incident per user account.
What should you do?
A. From Set rule logic, map the entities.
B. From Analytic rule details, configure Severity.
C. From Set rule logic, set Suppression to Off.
D. From Analytic rule details, configure Tactics.
-
Question 104:
You have a Microsoft 365 E5 subscription that uses Microsoft Teams and contains a user named User1.
You configure information barriers.
You need to identify which information barrier policies apply to User1.
Which cmdlet should you use?
A. Get-InformationBarrierRecipientStatus
B. Get-InformationBarrierPoliciesApplicationStatus
C. Get-InformationBarrierPolicy
D. Get-OrganizationSegment
-
Question 105:
You have a Microsoft 365 subscription.
You receive a General Data Protection Regulation (GDPR) request for the custom dictionary of a user.
From the Compliance admin center, you need to create a content search.
How should you configure the content search?
A. Condition: Type Operator. Equals any of Value: Office Roaming Service
B. Condition: Title Operator: Equals any of Value: Normal.dot
C. Condition: Type Operator: Equals any of Value: Documents
D. Condition: File type Operator: Equals any of Value: dic
-
Question 106:
You have a Microsoft 365 subscription linked to an Azure Active Directory (Azure AD) tenant that contains a user named User1. You need to grant User1 permission to search Microsoft 365 audit logs. The solution must use the principle of least privilege. Which role should you assign to User1?
A. the View-Only Audit Logs role in the Security and Compliance admin center
B. the View-Only Audit Logs role in the Exchange admin center
C. the Compliance Management role in the Exchange admin center
D. the Security reader role in the Azure Active Directory admin center
-
Question 107:
You have a Microsoft 365 subscription that contains 100 users and a Microsoft 365 group named Group1.
All users have Windows 10 devices and use Microsoft SharePoint Online and Exchange Online.
A sensitivity label named Label1 is published as the default label for Group1.
You add two sublabels named Sublabel1 and Sublabel2 to Label1.
You need to ensure that the settings in Sublabel1 are applied by default to Group1.
What should you do?
A. Change the order of Sublabel1.
B. Modify the policy of Label1.
C. Duplicate all the settings from Sublabel1 to Label1.
D. Delete the policy of Label1 and publish Sublabel1.
-
Question 108:
You have a Microsoft 365 alert named Alert2 as shown in the following exhibit.
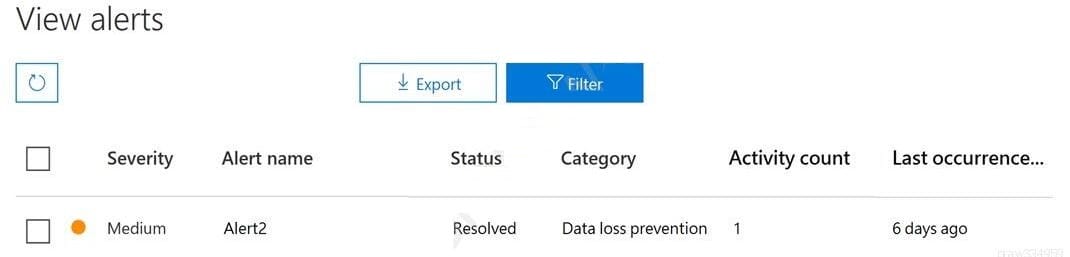
You need to manage the status of Alert2.
To which status can you change Alert2?
A. Active or Investigating only
B. Dismissed only
C. The status cannot be changed.
D. Investigating only
E. Investigating, Active, or Dismissed
-
Question 109:
You have a Microsoft 365 E5 subscription that contains 1,000 Windows 10 devices. The devices are onboarded to Microsoft Defender for Endpoint.
You need to view a consolidated list of the common vulnerabilities and exposures (CVE) that affect the devices. The solution must minimize administrative effort.
Which Threat and Vulnerability Management page should you use?
A. Software inventory
B. Event timeline
C. Weaknesses
D. Security recommendations
-
Question 110:
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
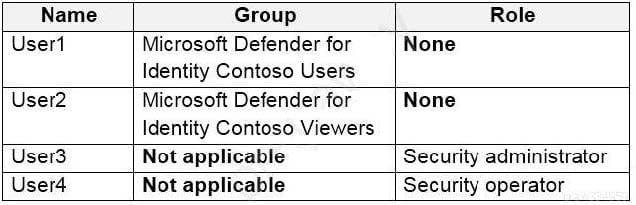
You discover that several security alerts are visible from the Microsoft Defender for Identity portal.
You need to identify which users in contoso.com can close the security alerts.
Which users should you identify?
A. User3 only
B. User1 and User2 only
C. User3 and User4 only
D. User1 and User3 only
E. User1 only
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-500 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.