MCD-LEVEL2 Exam Details
-
Exam Code
:MCD-LEVEL2 -
Exam Name
:MuleSoft Certified Developer - Level 2 (Mule 4) -
Certification
:Mulesoft Certifications -
Vendor
:Mulesoft -
Total Questions
:60 Q&As -
Last Updated
:Jan 12, 2026
Mulesoft MCD-LEVEL2 Online Questions & Answers
-
Question 1:
Which statement is true when using XML SDK for creating custom message processors?
A. Properties are fields defined by an end user of the XML SDK component and serve as a global configuration for the entire Mule project in which they are used
B. An XML SDK provides both inbound and outbound operations
C. Operations can be reused in recursive calls
D. All operations are public -
Question 2:
A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications.
Which XML element must be used to intercept outbound HTTP requests?
A. It is not possible to intercept outgoing HTTP requests, only inbound requests
B. http-policy:source
C. htt-policy:operation
D. http-policy:processor -
Question 3:
A system API that communicates to an underlying MySQL database is deploying to CloudHub. The DevOps team requires a readiness endpoint to monitor all system APIs.
Which strategy should be used to implement this endpoint?
A. Create a dedicated endpoint that responds with the API status and reachability of the underlying systems
B. Create a dedicated endpoint that responds with the API status and health of the server
C. Use an existing resource endpoint of the API
D. Create a dedicated endpoint that responds with the API status only -
Question 4:
Refer to the exhibit.
A Mute Object Store is configured with an entry TTL of one second and an expiration interval of 30 seconds.
What is the result of the flow if processing between os'store and os:retrieve takes 10 seconds?
A. nullPayload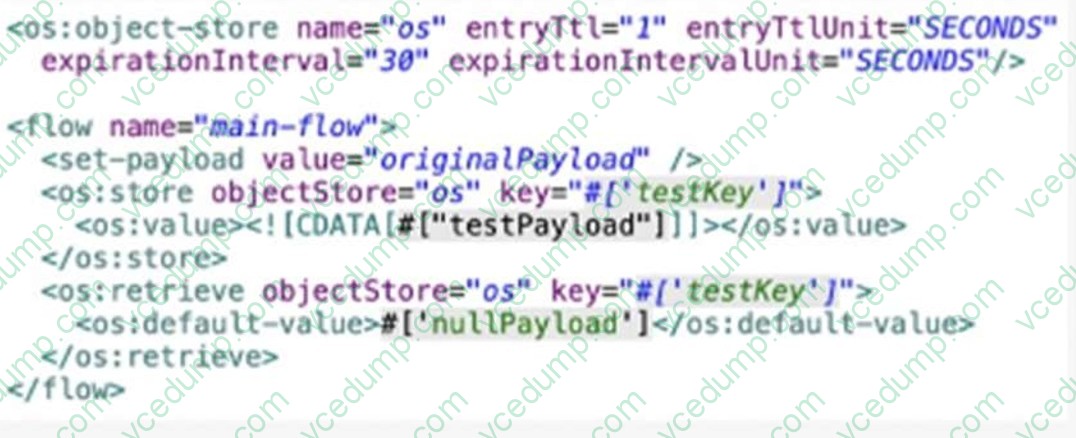
B. originalPayload
C. OS:KEY_NOT_FOUND
D. testPayload -
Question 5:
Two APIs are deployed to a two-node on-prem cluster. Due to a requirements change, the two APIs must communicate to exchange data asynchronously.
A. If the two APIs use the same domain, the VM Connector can be leveraged
B. The VM Connector is used to inter-application communication, so it is not possible to use the VM Connector
C. Instead of using the VM Connector use directly
D. It is not possible to use the VM Connector since the APIs are running in a cluster mode and each mode has it own set of VM Queues -
Question 6:
A Mule application includes a subflow containing a Scatter.Gather scope. Within each log of the Scatter.Gatter. an HTTP connector calls a PUT endpoint to modify records in different upstream system. The subflow is called inside an Unit successful scope to retry if a transitory exception is raised.
A technical spike is being performed to increase reliability of the Mule application.
Which steps should be performed within the Mule flow above the ensure idempontent behavior?
A. Change the PUT requests inside the Scatter-Gather to POST requests
B. Ensure an error-handling flow performs corrective actions to roll back all changes if any leg of the Scatter-Gather fails
C. Remove the Put requests from the Scatter-Getter and perform them sequentially
D. None, the flow already exhibits idempotent behavior -
Question 7:
Refer to the exhibit.

A developer generates the base scaffolding for an API in Anypoint Studio. Which HTTP status code is returned while testing using the API Kit console if no values are entered in client-secret?
A. HTTP status code:200
B. HTTP status code:403
C. HTTP status code:400
D. HTTP status code:500 -
Question 8:
What is the MuleSoft recommended method to encrypt sensitive property data?
A. The encryption key and sensitive data should be different for each environment
B. The encryption key should be identical for all environments
C. The encryption key should be identical for all environments and the sensitive data should be different for each environment
D. The encryption key should be different for each environment and the sensitive data should be the same for all environments -
Question 9:
A Mule application defines as SSL/TLS keystore properly `tis,keystore.keyPassword'' as secure.
How canthis property be referenced to access its value within the application?
A. #{secure::tiskeystore,keyPassowrd}
B. ${secure::tiskeystore,keyPassowrd}
C. ${secure::tiskeystore,keyPassowrd}
D. p{secure::tiskeystore,keyPassowrd} -
Question 10:
A scatter-gather router is configured with four routes:Route A, B, C and
D.
Route C false.
A. Error,errorMesage.payload.results [`2']
B. Payload failures[`2']
C. Error,errorMessage,payload.failures[`2']
D. Payload [`2']
Related Exams:
-
MCD-ASSOC
MuleSoft Certified Developer - Integration and API Associate (Mule 3) -
MCD-LEVEL1
MuleSoft Certified Developer - Level 1 (Mule 4) -
MCD-LEVEL1-DELTA
MuleSoft Certified Developer - Level 1 (Mule 4) DELTA -
MCD-LEVEL2
MuleSoft Certified Developer - Level 2 (Mule 4) -
MCIA-LEVEL1
MuleSoft Certified Integration Architect - Level 1 -
MCIA-LEVEL1-MAINTENANCE
MuleSoft Certified Integration Architect - Level 1 MAINTENANCE -
MCPA-LEVEL1
MuleSoft Certified Platform Architect - Level 1 -
MCPA-LEVEL1-MAINTENANCE
MuleSoft Certified Platform Architect - Level 1 MAINTENANCE
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Mulesoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MCD-LEVEL2 exam preparations and Mulesoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.