JN0-335 Exam Details
-
Exam Code
:JN0-335 -
Exam Name
:Security, Specialist (JNCIS-SEC) -
Certification
:Juniper Certifications -
Vendor
:Juniper -
Total Questions
:98 Q&As -
Last Updated
:Jan 25, 2026
Juniper JN0-335 Online Questions & Answers
-
Question 1:
You are asked to ensure that if the session table on your SRX Series device gets close to exhausting its resources, that you enforce a more aggress.ve age-out of existing flows.
In this scenario, which two statements are correct? (Choose two.)
A. The early-ageout configuration specifies the timeout value, in seconds, that will be applied once the low-watermark value is met.
B. The early-ageout configuration specifies the timeout value, in seconds, that will be applied once the high-watermark value is met.
C. The high-watermark configuration specifies the percentage of how much of the session table is left before disabling a more aggressive age- out timer.
D. The high-watermark configuration specifies the percentage of how much of the session table can be allocated before applying a more aggressive age-out timer -
Question 2:
Which two functions does Juniper ATP Cloud perform to reduce delays in the inspection of files? (Choose two.)
A. Juniper ATP Cloud allows the creation of allowlists.
B. Juniper ATP Cloud uses a single antivirus software package to analyze files.
C. Juniper ATP Cloud allows end users to bypass the inspection of files.
D. Juniper ATP Cloud performs a cache lookup on files. -
Question 3:
Click the Exhibit button.

You are validating the configuration template for device access. The commands in the exhibit have been entered to secure IP access to an SRX Series device.
Referring to the exhibit, which two statements are true? (Choose two.)
A. The device manager can access the device from 192.168.11.248.
B. The loopback interface blocks invalid traffic on its entry into the device.
C. The loopback interface blocks invalid traffic on its exit from the device.
D. The device manager can access the device from 10.253.1.2. -
Question 4:
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
A. URL filtering
B. micro application detection
C. content filtering
D. APPID -
Question 5:
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
A. AppTrack
B. AppQoS
C. AppFW
D. APPID -
Question 6:
Which two statements are correct about the cSRX? (Choose two.)
A. The cSRX supports firewall, NAT, IPS, and UTM services.
B. The cSRX only supports Layer 2 "bump-in-the-wire" deployments.
C. The cSRX supports BGP, OSPF. and IS-IS routing services.
D. The cSRX has three default zones: trust, untrust, and management -
Question 7:
Your company is using the Juniper ATP Cloud free model. The current inspection profile is set at 10 MB You are asked to configure ATP Cloud so that executable files up to 30 MB can be scanned while at the same time minimizing the change in scan time for other file types.
Which configuration should you use in this scenario?
A. Use the CLI to create a custom profile and increase the scan limit.
B. Use the ATP Cloud Ul to change the default profile to increase the scan limit for all files to 30 MB.
C. Use the CLI to change the default profile to increase the scan limit for all files to 30 MB.
D. Use the ATP Cloud Ul to update a custom profile and increase the scan limit for executable files to 30 MB. -
Question 8:
Exhibit
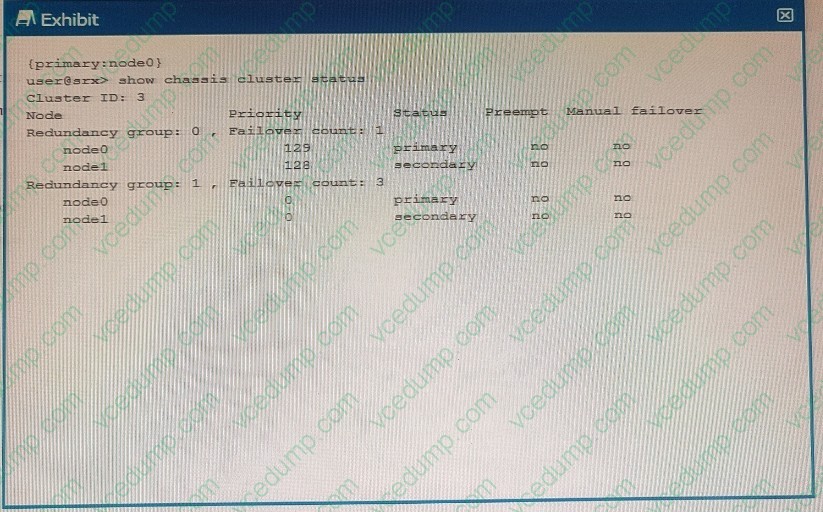
Using the information from the exhibit, which statement is correct?
A. Redundancy group 1 is in an ineligible state.
B. Node1 is the active node for the control plane
C. There are no issues with the cluster.
D. Redundancy group 0 is in an ineligible state. -
Question 9:
Which two statements are correct about JSA data collection? (Choose two.)
A. The Event Collector collects information using BGP FlowSpec.
B. The Flow Collector can use statistical sampling
C. The Flow Collector parses logs.
D. The Event Collector parses logs -
Question 10:
On an SRX Series firewall, what are two ways that Encrypted Traffic Insights assess the threat of the traffic? (Choose two.)
A. It decrypts the file in a sandbox.
B. It validates the certificates used.
C. It decrypts the data to validate the hash.
D. It reviews the timing and frequency of the connections.
Related Exams:
-
JN0-102
Internet Associate, Junos(JNCIA-Junos) -
JN0-104
Junos, Associate (JNCIA-Junos) -
JN0-105
Junos, Associate (JNCIA-Junos) -
JN0-1101
Juniper Networks Certified Design Associate (JNCDA) -
JN0-1103
Design, Associate (JNCIA-Design) -
JN0-130
Juniper networks Certified internet specialist.e(jncis-e) -
JN0-1301
Data Center Design, Specialist (JNCDS-DC) -
JN0-1302
Data Center Design Specialist (JNCDS-DC) -
JN0-1331
Security Design, Specialist (JNCDS-SEC) -
JN0-1332
Security Design, Specialist (JNCDS-SEC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-335 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.