ISO-IEC-27001-LEAD-AUDITOR Exam Details
-
Exam Code
:ISO-IEC-27001-LEAD-AUDITOR -
Exam Name
:PECB Certified ISO/IEC 27001 Lead Auditor exam -
Certification
:PECB Certifications -
Vendor
:PECB -
Total Questions
:289 Q&As -
Last Updated
:Jan 11, 2026
PECB ISO-IEC-27001-LEAD-AUDITOR Online Questions & Answers
-
Question 1:
Which six of the following actions are the individual(s) managing the audit programme responsible for?
A. Selecting the audit team
B. Retaining documented information of the audit results
C. Defining the objectives, scope and criteria for an individual audit
D. Defining the plan of an individual audit
E. Establishing the extent of the audit programme
F. Establishing the audit programme
G. Determining the resources necessary for the audit programme
H. Communicating with the auditee during the audit -
Question 2:
The data center at which you work is currently seeking ISO/IEC27001:2022 certification. In preparation for your initial certification visit a number of internal audits have been carried out by a colleague working at another data centre within your Group. They secured their ISO/IEC 27001:2022 certificate earlier in the year.
You have just qualified as an Internal ISMS auditor and your manager has asked you to review the audit process and audit findings as a final check before the external Certrfication Body arrives.
Which six of the following would cause you concern in respect of conformity to ISO/IEC 27001:2022 requirements?
A. The audit programme shows management reviews taking place at irregular intervals during the year
B. Audit reports are not held in hardcopy (i.e. on paper). They are only stored as ".POF documents on the organisation's intranet
C. The audit programme does not take into account the relative importance of information security processes
D. The audit programme mandates auditors must be independent of the areas they audit in order to satisfy the requirements of ISO/IEC 27001:2022
E. Although the scope for each internal audit has been defined, there are no audit criteria defined for the audits carried out to date
F. Audit reports to date have used key performance indicator information to focus solely on the efficiency of ISMS processes
G. The audit programme does not reference audit methods or audit responsibilities
H. The audit programme does not take into account the results of previous audits
I. Top management commitment to the ISMS will not be audited before the certification visit, according to the audit programme
J. The audit process states the results of audits will be made available to 'relevant' managers, not top management -
Question 3:
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including mis- addressed labels and, in 15% of company cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SH: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity. Referencing the scenario, which six of the following Appendix A controls would you expect the auditee to have implemented when you conduct the follow- up audit?
A. 5.11 Return of assets
B. 8.12 Data leakage protection
C. 5.3 Segregation of duties
D. 6.3 Information security awareness, education, and training
E. 7.10 Storage media
F. 8.3 Information access restriction
G. 5.6 Contact with special interest groups
H. 6.4 Disciplinary process
I. 7.4 Physical security monitoring
J. 5.13 Labelling of information -
Question 4:
OrgXY is an ISO/IEC 27001-certified software development company. A year after being certified, OrgXY's top management informed the certification body that the company was not ready for conducting the surveillance audit. What happens in this case?
A. The certification is suspended
B. The current certification is used until the next surveillance audit
C. OrgXY transfers its registration to another certification body -
Question 5:
Phishing is what type of Information Security Incident?
A. Private Incidents
B. Cracker/Hacker Attacks
C. Technical Vulnerabilities
D. Legal Incidents -
Question 6:
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including misaddressed labels and, in 15% of cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SM: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity against ISO 27001:2022 based on the lack of control of the labelling process. At the closing meeting, the Shipping Manager issues an apology to you that his comments may have been misunderstood.
He says that he did not realise that there is a background IT process that automatically checks that the right label goes onto the right parcel otherwise the parcel is ejected at labelling. He asks that you withdraw your nonconformity.
Select three options of the correct responses that you as the audit team leader would make to the request of the Shipping Manager.
A. Advise the Shipping Manager that his request will be included in the audit report
B. Advise management that the new information provided will be discussed when the auditors have more time
C. Inform the Shipping Manager that the nonconformity is minor and should be quickly corrected
D. Ask the audit team members to state what they think should happen
E. Inform him of your understanding and withdraw the nonconformity
F. Thank the Shipping Manager for his honesty but advise that withdrawing the nonconformity is not the right way to proceed
G. Advise the Shipping Manager that the nonconformity must stand since the evidence obtained for it was dear
H. Indicate that the nonconformity is evidence of a deeper system failure that needs to be rectified -
Question 7:
Auditors should have certain knowledge and skills; while audit team leaders should have some additional knowledge and skills. From the following list, select two that only apply to audit team leaders.
A. Plan the audit
B. Understand and apply the risk-based approach to auditing
C. Apply appropriate sampling techniques
D. Make effective use of resources provided to the audit
E. Be aware of cultural and social aspects of the auditee
F. Verify the relevance and accuracy of collected information -
Question 8:
You are an experienced audit team leader guiding an auditor in training.
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the ORGANISATIONAL controls listed in the Statement of
Applicability (SoA) and implemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
A. Access to and from the loading bay
B. Confidentiality and nondisclosure agreements
C. How information security has been addressed within supplier agreements
D. How power and data cables enter the building
E. Rules for transferring information within the organisation and to other organisations
F. The development and maintenance of an information asset inventory
G. The operation of the site CCTV and door control systems
H. The organisation's business continuity arrangements -
Question 9:
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services.
The next step in your audit plan is to verify the information security on ABC's healthcare mobile app development, support, and lifecycle process. During the audit, you learned the organization outsourced the mobile app development to a professional software development company with CMMI Level 5, ITSM (ISO /IEC 20000-1), BCMS (ISO 22301) and ISMS (ISO/IEC 27001) certified. The IT Manager presented the software security management procedure and summarised the process as follows:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a minimum. The following security functions for personal data protection shall be available: Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report - details as follows:
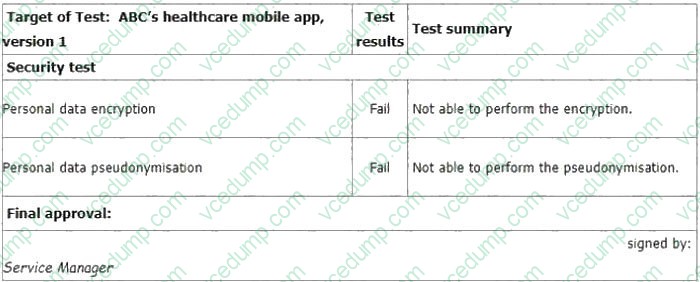
You ask the IT Manager why the organisation still uses the mobile app while personal data encryption and pseudonymization tests failed. Also, whether the Service Manager is authorized to approve the test.
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymization functions failed is that these functions heavily slowed
down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That's why the Service Manager signed the approval.
You sample one of the medical staff's mobile and found that ABC's healthcare mobile app, version 1.01 is installed. You found that version 1.01 has no test record.
The IT Manager explains that because of frequent ransomware attacks, the outsourced mobile app development company gave a free minor update on the tested software, performed an emergency release of the updated software, and gave
a verbal guarantee that there will be no impact on any security functions. Based on his 20 years of information security experience, there is no need to re-test.
You are preparing the audit findings Select two options that are correct.
A. There is a nonconformity (NC). The IT. Manager does not comply with the software security management procedure. (Relevant to clause 8.1, control A.8.30)
B. There is a nonconformity (NC). The organisation does not control planned changes and review the consequences of unintended changes. (Relevant to clause 8.1)
C. There is an opportunity for improvement (OI). The IT Manager should make the decision to continue the service based on appropriate testing. (Relevant to clause 8.1, control A.8.30)
D. There is an opportunity for improvement (OI). The organisation selects an external service provider based on the extent of free services it will provide. (Relevant to clause 8.1, control A.5.21)
E. There is NO nonconformity (NC). The IT Manager demonstrates good leadership. (Relevant to clause 5.1, control 5.4)
F. There is NO nonconformity (NC). The IT Manager demonstrates he is fully competent. (Relevant to clause 7.2) -
Question 10:
Which two of the following are examples of audit methods that 'do not' involve human interaction?
A. Conducting an interview using a teleconferencing platform
B. Performing a review of auditees procedures in preparation for an audit
C. Reviewing the auditee's response to an audit finding
D. Analysing data by remotely accessing the auditee's server
E. Observing work performed by remote surveillance
F. Confirming the date and time of the audit
Related Exams:
-
ISO-20000-FND
ISO/IEC 20000 Foundation -
ISO-22301-BCMS-CLA
ISO 22301 BCMS - Certified Lead Auditor -
ISO-22301-LA
ISO 22301 Lead Auditor -
ISO-22301-LEAD-AUDITOR
PECB Certified ISO 22301 Lead Auditor Exam -
ISO-22301-LI
ISO 22301 Lead Implementer -
ISO-27001-ISMS-FND
ISO 27001:2013 ISMS - Foundation -
ISO-27001-LA
ISO/IEC 27001:2022 Lead Auditor -
ISO-27001-LI
ISO/IEC 27001:2022 Lead Implementer -
ISO-27002-LI
ISO/IEC 27002 - Lead Implementer -
ISO-27005-RM
ISO/IEC 27005 Risk Manager
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only PECB exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ISO-IEC-27001-LEAD-AUDITOR exam preparations and PECB certification application, do not hesitate to visit our Vcedump.com to find your solutions here.