ECSAV10 Exam Details
-
Exam Code
:ECSAV10 -
Exam Name
:EC-Council Certified Security Analyst (ECSA) v10 -
Certification
:EC-COUNCIL Certifications -
Vendor
:EC-COUNCIL -
Total Questions
:354 Q&As -
Last Updated
:Jan 21, 2026
EC-COUNCIL ECSAV10 Online Questions & Answers
-
Question 1:
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machine?
A. Inference-based Assessment
B. Service-based Assessment Solutions
C. Product-based Assessment Solutions
D. Tree-based Assessment -
Question 2:
Which one of the following 802.11 types has WLAN as a network support?
A. 802.11b
B. 802.11-Legacy
C. 802.11n
D. 802.11g -
Question 3:
Hackers today have an ever-increasing list of weaknesses in the web application structure at their disposal, which they can exploit to accomplish a wide variety of malicious tasks.
New flaws in web application security measures are constantly being researched, both by hackers and by security professionals. Most of these flaws affect all dynamic web applications whilst others are dependent on specific application
technologies.
In both cases, one may observe how the evolution and refinement of web technologies also brings about new exploits which compromise sensitive databases, provide access to theoretically secure networks, and pose a threat to the daily
operation of online businesses.
What is the biggest threat to Web 2.0 technologies?
A. SQL Injection Attacks
B. Service Level Configuration Attacks
C. Inside Attacks
D. URL Tampering Attacks -
Question 4:
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing. Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
A. Total number of employees in the client organization
B. Type of testers involved
C. The budget required
D. Expected time required to finish the project -
Question 5:
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
A. Vulnerabilities checklists
B. Configuration checklists
C. Action Plan
D. Testing Plan -
Question 6:
Which of the following has an offset field that specifies the length of the header and data?
A. IP Header
B. UDP Header
C. ICMP Header
D. TCP Header -
Question 7:
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by using %xx notation, where 'xx' is the
A. ASCII value of the character
B. Binary value of the character
C. Decimal value of the character
D. Hex value of the character -
Question 8:
George is a senior security analyst working for a state agency in Florida; His state's congress just passed a bill mandating every state agency to undergo a security audit annually. After learning what will be required, George needs to
implement an IDS as soon as possible before the first audit occurs.
The state bill requires that an IDS with a "time-based induction machine" be used. What IDS feature must George implement to meet this requirement?
A. Pattern matching
B. Statistical-based anomaly detection
C. Real-time anomaly detection
D. Signature-based anomaly detection -
Question 9:
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools.
The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected. Conventionally it is achieved by comparing the MAC address of the participating
wireless devices.
Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?
A. Social engineering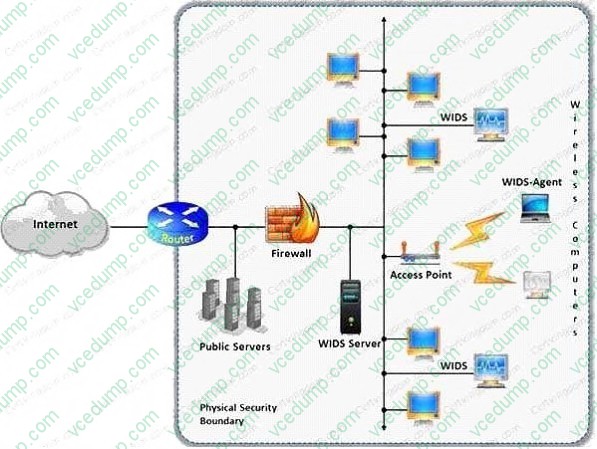
B. SQL injection
C. Parameter tampering
D. Man-in-the-middle attack -
Question 10:
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated valuation of the risk will be performed so that the vulnerabilities can be reported as High/Medium/Low risk issues.

What are the two types of `white-box' penetration testing?
A. Announced testing and blind testing
B. Blind testing and double blind testing
C. Blind testing and unannounced testing
D. Announced testing and unannounced testing
Related Exams:
-
112-51
EC-Council Certified Network Defense Essentials (NDE) -
212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0 -
212-77
EC-Council Certified Linux Security -
212-81
EC-Council Certified Encryption Specialist (ECES) -
212-82
EC-Council Certified Cybersecurity Technician (C|CT) -
212-89
EC Council Certified Incident Handler (ECIH v3) -
312-38
EC-Council Certified Network Defender (CND) -
312-39
EC-Council Certified SOC Analyst (CSA) -
312-40
EC-Council Certified Cloud Security Engineer (CCSE) -
312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.