Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Aug 23, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 61:
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for help on a firewall. He wants to use Linux as his firewall and use the latest freely available version that is offered. What do you recommend?
Select the best answer.
A. Ipchains
B. Iptables
C. Checkpoint FW for Linux
D. Ipfwadm
-
Question 62:
Exhibit
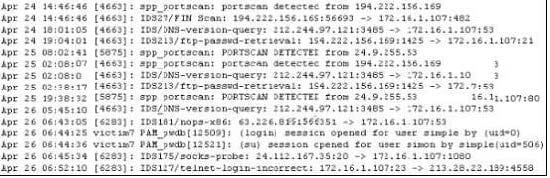
Study the log given in the exhibit,
Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
A. Disallow UDP 53 in from outside to DNS server
B. Allow UDP 53 in from DNS server to outside
C. Disallow TCP 53 in form secondaries or ISP server to DNS server
D. Block all UDP traffic
-
Question 63:
On a backdoored Linux box there is a possibility that legitimate programs are modified or trojaned. How is it possible to list processes and uids associated with them in a more reliable manner?
A. Use "Is"
B. Use "lsof"
C. Use "echo"
D. Use "netstat"
-
Question 64:
Clive is conducting a pen-test and has just port scanned a system on the network. He has identified the operating system as Linux and been able to elicit responses from ports 23, 25 and 53. He infers port 23 as running Telnet service, port 25 as running SMTP service and port 53 as running DNS service. The client confirms these findings and attests to the current availability of the services. When he tries to telnet to port 23 or 25, he gets a blank screen in response. On typing other commands, he sees only blank spaces or underscores symbols on the screen. What are you most likely to infer from this?
A. The services are protected by TCP wrappers
B. There is a honeypot running on the scanned machine
C. An attacker has replaced the services with trojaned ones
D. This indicates that the telnet and SMTP server have crashed
-
Question 65:
After studying the following log entries, what is the attacker ultimately trying to achieve as inferred from the log sequence?
1.
mkdir -p /etc/X11/applnk/Internet/.etc
2.
mkdir -p /etc/X11/applnk/Internet/.etcpasswd
3.
touch -acmr /etc/passwd /etc/X11/applnk/Internet/.etcpasswd
4.
touch -acmr /etc /etc/X11/applnk/Internet/.etc
5.
passwd nobody -d
6.
/usr/sbin/adduser dns -d/bin -u 0 -g 0 -s/bin/bash
7.
passwd dns -d
8.
touch -acmr /etc/X11/applnk/Internet/.etcpasswd /etc/passwd
9.
touch -acmr /etc/X11/applnk/Internet/.etc /etc
A. Change password of user nobody
B. Extract information from a local directory
C. Change the files Modification Access Creation times
D. Download rootkits and passwords into a new directory
-
Question 66:
Ron has configured his network to provide strong perimeter security. As part of his network architecture, he has included a host that is fully exposed to attack. The system is on the public side of the demilitarized zone, unprotected by a firewall or filtering router. What would you call such a host?
A. Honeypot
B. DMZ host
C. DWZ host
D. Bastion Host
-
Question 67:
What is Cygwin?
A. Cygwin is a free C++ compiler that runs on Windows
B. Cygwin is a free Unix subsystem that runs on top of Windows
C. Cygwin is a free Windows subsystem that runs on top of Linux
D. Cygwin is a X Windows GUI subsytem that runs on top of Linux GNOME environment
-
Question 68:
Rebecca is a security analyst and knows of a local root exploit that has the ability to enable local users to use available exploits to gain root privileges. This vulnerability exploits a condition in the Linux kernel within the execve() system call. There is no known workaround that exists for this vulnerability. What is the correct action to be taken by Rebecca in this situation as a recommendation to management?
A. Rebecca should make a recommendation to disable the () system call
B. Rebecca should make a recommendation to upgrade the Linux kernel promptly
C. Rebecca should make a recommendation to set all child-process to sleep within the execve()
D. Rebecca should make a recommendation to hire more system administrators to monitor all child processes to ensure that each child process can't elevate privilege
-
Question 69:
Rebecca has noted multiple entries in her logs about users attempting to connect on ports that are either not opened or ports that are not for public usage. How can she restrict this type of abuse by limiting access to only specific IP addresses that are trusted by using one of the built-in Linux Operating System tools?
A. Ensure all files have at least a 755 or more restrictive permissions.
B. Configure rules using ipchains.
C. Configure and enable portsentry on his server.
D. Install an intrusion detection system on her computer such as Snort.
-
Question 70:
John is discussing security with Jane. Jane had mentioned to John earlier that she suspects an LKM has been installed on her server. She believes this is the reason that the server has been acting erratically lately. LKM stands for Loadable Kernel Module.
What does this mean in the context of Linux Security?
A. Loadable Kernel Modules are a mechanism for adding functionality to a file system without requiring a kernel recompilation.
B. Loadable Kernel Modules are a mechanism for adding functionality to an operating- system kernel after it has been recompiled and the system rebooted.
C. Loadable Kernel Modules are a mechanism for adding auditing to an operating-system kernel without requiring a kernel recompilation.
D. Loadable Kernel Modules are a mechanism for adding functionality to an operating- system kernel without requiring a kernel recompilation.
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.