Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Jun 29, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 721:
Frederickson Security Consultants is currently conducting a security audit on the networks of Hawthorn Enterprises, a contractor for the Department of Defense. Since Hawthorn Enterprises conducts business daily with the federal government, they must abide by very stringent security policies. Frederickson is testing all of Hawthorn's physical and logical security measures including biometrics, passwords, and permissions. The federal government requires that all users must utilize random, non-dictionary passwords that must take at least 30 days to crack. Frederickson has confirmed that all Hawthorn employees use a random password generator for their network passwords. The Frederickson consultants have saved off numerous SAM files from Hawthorn's servers using Pwdump6 and are going to try and crack the network passwords. What method of attack is best suited to crack these passwords in the shortest amount of time?
A. Brute force attack
B. Birthday attack
C. Dictionary attack
D. Brute service attack
-
Question 722:
Gerald, the Systems Administrator for Hyped Enterprises, has just discovered that his network has been breached by an outside attacker. After performing routine maintenance on his servers, he discovers numerous remote tools were installed that no one claims to have knowledge of in his department. Gerald logs onto the management console for his IDS and discovers an unknown IP address that scanned his network constantly for a week and was able to access his network through a high-level port that was not closed. Gerald traces the IP address he found in the IDS log to a proxy server in Brazil. Gerald calls the company that owns the proxy server and after searching through their logs, they trace the source to another proxy server in Switzerland. Gerald calls the company in Switzerland that owns the proxy server and after scanning through the logs again, they trace the source back to a proxy server in China. What proxy tool has Gerald's attacker used to cover their tracks?
A. ISA proxy
B. IAS proxy
C. TOR proxy
D. Cheops proxy
-
Question 723:
What is the default Password Hash Algorithm used by NTLMv2?
A. MD4
B. DES
C. SHA-1
D. MD5
-
Question 724:
What type of session hijacking attack is shown in the exhibit?
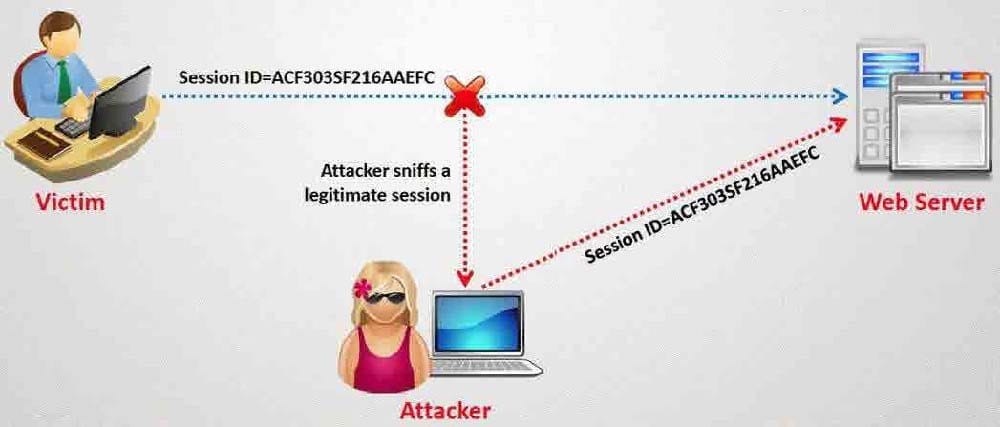
A. Session Sniffing Attack
B. Cross-site scripting Attack
C. SQL Injection Attack
D. Token sniffing Attack
-
Question 725:
Which port, when configured on a switch receives a copy of every packet that passes through it?
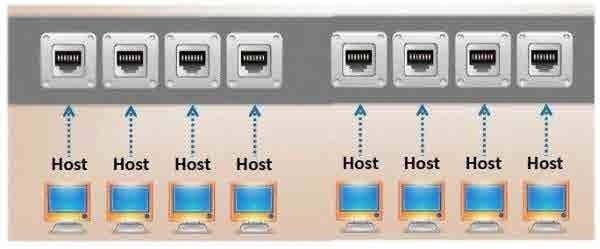
A. R-DUPE Port
B. MIRROR port
C. SPAN port
D. PORTMON
-
Question 726:
What is the IV key size used in WPA2?
A. 32
B. 24
C. 16
D. 48
E. 128
-
Question 727:
Attackers send an ACK probe packet with random sequence number, no response means port is filtered (Stateful firewall is present) and RST response means the port is not filtered. What type of Port Scanning is this?
A. RST flag scanning
B. FIN flag scanning
C. SYN flag scanning
D. ACK flag scanning
-
Question 728:
What is the command used to create a binary log file using tcpdump?
A. tcpdump -w ./log
B. tcpdump -r log
C. tcpdump -vde logtcpdump -vde ? log
D. tcpdump -l /var/log/
-
Question 729:
What type of encryption does WPA2 use?
A. DES 64 bit
B. AES-CCMP 128 bit
C. MD5 48 bit
D. SHA 160 bit
-
Question 730:
Charlie is the network administrator for his company. Charlie just received a new Cisco router and wants to test its capabilities out and to see if it might be susceptible to a DoS attack resulting in its locking up. The IP address of the Cisco switch is 172.16.0.45. What command can Charlie use to attempt this task?
A. Charlie can use the commanD. ping -l 56550 172.16.0.45 -t.
B. Charlie can try using the commanD. ping 56550 172.16.0.45.
C. By using the command ping 172.16.0.45 Charlie would be able to lockup the router
D. He could use the commanD. ping -4 56550 172.16.0.45.
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.