Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Jun 29, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 341:
The following excerpt is taken from a honeyput log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. Study the log given below and answer the following question:
(Note: The objective of this questions is to test whether the student has learnt about passive OS fingerprinting (which should tell them the OS from log captures):
can they tell a SQL injection attack signature; can they infer if a user ID has been created by an attacker and whether they can read plain source ?destination entries from log entries.)

What can you infer from the above log?
A. The system is a windows system which is being scanned unsuccessfully.
B. The system is a web application server compromised through SQL injection.
C. The system has been compromised and backdoored by the attacker.
D. The actual IP of the successful attacker is 24.9.255.53.
-
Question 342:
Exhibit
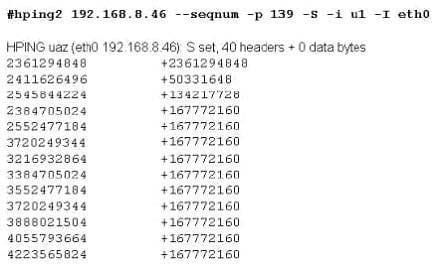
Joe Hacker runs the hping2 hacking tool to predict the target host's sequence numbers in one of the hacking session. What does the first and second column mean? Select two.
A. The first column reports the sequence number
B. The second column reports the difference between the current and last sequence number
C. The second column reports the next sequence number
D. The first column reports the difference between current and last sequence number
-
Question 343:
While footprinting a network, what port/service should you look for to attempt a zone transfer?
A. 53 UDP
B. 53 TCP
C. 25 UDP
D. 25 TCP
E. 161 UDP
F. 22 TCP
G. 60 TCP
-
Question 344:
Your lab partner is trying to find out more information about a competitors web site. The site has a .com extension. She has decided to use some online whois tools and look in one of the regional Internet registrys. Which one would you suggest she looks in first?
A. LACNIC
B. ARIN
C. APNIC
D. RIPE
E. AfriNIC
-
Question 345:
Network Administrator Patricia is doing an audit of the network. Below are some of her findings concerning DNS. Which of these would be a cause for alarm? Select the best answer.
A. There are two external DNS Servers for Internet domains. Both are AD integrated.
B. All external DNS is done by an ISP.
C. Internal AD Integrated DNS servers are using private DNS names that are
D. unregistered.
E. Private IP addresses are used on the internal network and are registered with the internal AD integrated DNS server.
-
Question 346:
Doug is conducting a port scan of a target network. He knows that his client target network has a web server and that there is a mail server also which is up and running. Doug has been sweeping the network but has not been able to elicit any response from the remote target. Which of the following could be the most likely cause behind this lack of response? Select 4.
A. UDP is filtered by a gateway
B. The packet TTL value is too low and cannot reach the target
C. The host might be down
D. The destination network might be down
E. The TCP windows size does not match
F. ICMP is filtered by a gateway
-
Question 347:
NSLookup is a good tool to use to gain additional information about a target network. What does the following command accomplish? nslookup
> server
> set type =any
> ls -d
A. Enables DNS spoofing
B. Loads bogus entries into the DNS table
C. Verifies zone security
D. Performs a zone transfer
E. Resets the DNS cache
-
Question 348:
Which of the following tools are used for footprinting? (Choose four)
A. Sam Spade
B. NSLookup
C. Traceroute
D. Neotrace
E. Cheops
-
Question 349:
According to the CEH methodology, what is the next step to be performed after footprinting?
A. Enumeration
B. Scanning
C. System Hacking
D. Social Engineering
E. Expanding Influence
-
Question 350:
You receive an email with the following message:
Hello Steve,
We are having technical difficulty in restoring user database record after the recent blackout. Your account data is corrupted. Please logon to the SuperEmailServices.com and change your password.
http://[email protected]/support/logon.htm
If you do not reset your password within 7 days, your account will be permanently disabled locking you out from our e-mail services.
Sincerely,
Technical Support
SuperEmailServices
From this e-mail you suspect that this message was sent by some hacker since you have been using their e-mail services for the last 2 years and they have never sent out an e-mail such as this. You also observe the URL in the message and
confirm your suspicion about 0xde.0xad.0xbde.0xef which looks like hexadecimal numbers. You immediately enter the following at Windows 2000 command prompt:
Ping 0xde.0xad.0xbe.0xef
You get a response with a valid IP address.
What is the obstructed IP address in the e-mail URL?
A. 222.173.190.239
B. 233.34.45.64
C. 54.23.56.55
D. 199.223.23.45
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.