Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 211:
While the code is still in the development environment, a security architect is testing the code stored in the code repository to ensure the top ten OWASP secure coding practices are being followed. Which of the following code analyzers will produce the desired results?
A. Static
B. Dynamic
C. Fuzzer
D. Peer review
-
Question 212:
The Chief Information Security Officer (CISO) is preparing a requirements matrix scorecard for a new security tool the company plans to purchase Feedback from which of the following documents will provide input for the requirements matrix scorecard during the vendor selection process?
A. MSA
B. RFQ
C. RFI
D. RFP
-
Question 213:
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created:
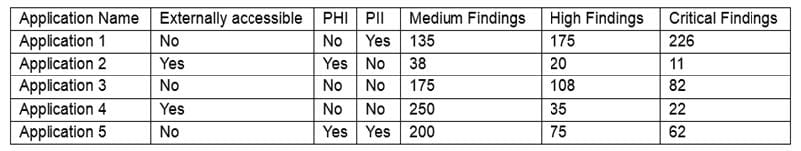
The findings are then categorized according to the following chart:
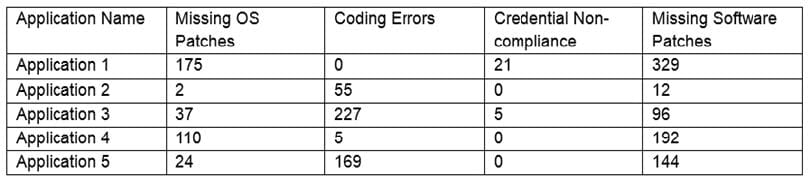
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Choose two.)
A. Place a WAF in line with Application 2
B. Move Application 3 to a secure VLAN and require employees to use a jump server for access.
C. Apply the missing OS and software patches to the server hosting Application 4
D. Use network segmentation and ACLs to control access to Application 5.
E. Implement an IDS/IPS on the same network segment as Application 3
F. Install a FIM on the server hosting Application 4
-
Question 214:
A manufacturing company employs SCADA systems to drive assembly lines across geographically dispersed sites. Therefore, the company must use the Internet to transport control messages and responses. Which of the following architectural changes when integrated will BEST reduce the manufacturing control system's attack surface? (Select TWO)
A. Design a patch management capability for control systems.
B. Implement supply chain security.
C. Integrate message authentication
D. Add sensors and collectors at the Internet boundary.
E. Isolate control systems from enterprise systems.
F. Implement a site-to-site VPN across sites
-
Question 215:
A company is trying to resolve the following issues related to its web servers and Internet presence:
1.
The company's security rating declined on multiple occasions when it failed to renew a TLS certificate on one or more infrequently used web servers
2.
The company is running out of public IPs assigned by its ISP
3.
The company is implementing a WAF. and the WAF vendor charges by back-end hosts to which the WAF routes
Which of the following solutions will help the company mitigate these issues? (Select TWO).
A. Use a DMZ architecture
B. Implement reverse proxy servers
C. Use an automated CA service API for certificate renewal
D. Work with the company's ISP to configure BGP
E. Deploy IPv6 for external-facing servers
F. Implement self-signed certificates and disable trust verification.
-
Question 216:
The Chief Financial Officer (CFO) of an organization wants the IT department to add the CFO's account to the domain administrator group The IT department thinks this is nsky and wants support from the security manager before proceeding. Which of the following BEST supports the argument against providing the CFO with domain administrator access?
A. Discretionary access control
B. Separation of duties
C. Data classification
D. Mandatory access control
-
Question 217:
A security administrator wants to stand up a NIPS that is multilayered and can incorporate many security technologies into a single platform The product should have diverse capabilities, such as antivirus, VPN, and firewall services, and be able to be updated in a timely manner to meet evolving threats. Which of the following network prevention system types can be used to satisfy the requirements?
A. Application firewall
B. Unified threat management
C. Enterprise firewall
D. Content-based IPS
-
Question 218:
An organization is implementing a virtualized thin-client solution for normal user computing and access. During a review of the architecture, concerns were raised that an attacker could gain access to multiple user environments by simply gaining a foothold on a single one with malware. Which of the following reasons BEST explains this?
A. Malware on one virtual environment could enable pivoting to others by leveraging vulnerabilities in the hypervisor.
B. A worm on one virtual environment could spread to others by taking advantage of guest OS networking services vulnerabilities.
C. One virtual environment may have one or more application-layer vulnerabilities, which could allow an attacker to escape that environment.
D. Malware on one virtual user environment could be copied to all others by the attached network storage controller.
-
Question 219:
A SaaS provider decides to offer data storage as a service. For simplicity, the company wants to make the service available over industry standard APIs, routable over the public Internet. Which of the following controls offers the MOST protection to the company and its customers' information?
A. Detailed application logging
B. Use of non-standard ports
C. Web application firewall
D. Multifactor authentication
-
Question 220:
A government entity is developing requirements for an RFP to acquire a biometric authentication system When developing these requirements, which of the following considerations is MOST critical to the verification and validation of the SRTM?
A. Local and national laws and regulations
B. Secure software development requirements
C. Environmental constraint requirements
D. Testability of requirements
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.