Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 201:
A secure facility has a server room that currently is controlled by a simple lock and key. and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators' smartphones, is purchased and installed. The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are:
1.
It cannot be invasive to the end user
2.
It must be utilized as a second factor.
3.
Information sharing must be avoided
4.
It must have a low false acceptance rate
Which of the following BEST meets the criteria?
A. Facial recognition
B. Swipe pattern
C. Fingerprint scanning
D. Complex passcode
E. Token card
-
Question 202:
Confidential information related to Application A. Application B and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:
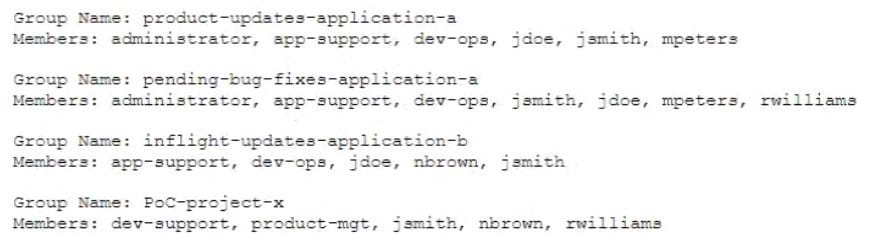
Which of the following actions should the IR team take FIRST?
A. Remove all members from the distribution groups immediately
B. Place the mailbox for jsmith on legal hold
C. Implement a proxy server on the network to inspect all outbound SMTP traffic for the DevOps group
D. Install DLP software on all developer laptops to prevent data from leaving the network.
-
Question 203:
A red team is able to connect a laptop with penetration testing tools directly into an open network port The team then is able to take advantage of a vulnerability on the domain controller to create and promote a new enterprise administrator. Which of the following technologies would MOST likely eliminate this attack vector m the future?
A. Monitor for anomalous creations of privileged domain accounts
B. Install a NIPS with rules appropriate to drop most exploit traffic
C. Ensure the domain controller has the latest security patches
D. Implement 802.1X with certificate-based authentication
-
Question 204:
A PaaS provider deployed a new product using a DevOps methodology Because DevOps is used to support both development and production assets inherent separation of duties is limited To ensure compliance with security frameworks that require a specific set of controls relating to separation of duties the organization must design and implement an appropriate compensating control Which of the following would be MOST suitable in this scenario?
A. Configuration of increased levels of logging, monitoring and alerting on production access
B. Configuration of MFA and context-based login restrictions for all DevOps personnel
C. Development of standard code libraries and usage of the WS-security module on all web servers
D. Implementation of peer review, static code analysis and web application penetration testing against the staging environment
-
Question 205:
A company uses AD and RADIUS to authenticate VPN and WiFi connections The Chief Information Security Officer (CISO) initiates a project to extend a third-party MFA solution to VPN. During the pilot phase, VPN users successfully get an MFA challenge, however they also get the challenge when connecting to WiFi. which is not desirable Which of the following BEST explains why users are getting the MFA challenge when using WiFi?
A. In the RADIUS server, the proxy rule has not specified the NAS-Port-Type attribute that should be matched
B. In the firewall, in the AAA configuration the IP address of the third-party MFA solution needs to be set as a secondary RADIUS server
C. In the third-party MFA solution authentication properties need to be configured to recognize WiFi authentication requests
D. In the WiFi configuration authentication needs to be changed to WPA2 Enterprise using EAP-TLS to support the configuration
-
Question 206:
A legal services company wants to ensure emails to clients maintain integrity in transit Which of the following would BEST meet this requirement? (Select TWO)
A. Signing emails to clients with the organization's public key
B. Using the organization's private key to encrypt all communication
C. Implementing a public key infrastructure
D. Signing emails to clients with the organization's private key
E. Using shared secret keys
F. Hashing all outgoing emails
-
Question 207:
A security engineer reviews the table below: The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring the future?
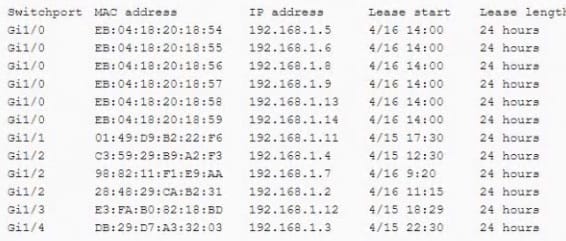
A. Upgrading device firmware
B. Enabling port security
C. Increasing DHCP pool size
D. Disabling dynamic trucking
E. Reducing DHCP lease length
-
Question 208:
A researcher is working to identify what appears to be a new variant of an existing piece of malware commonly used in ransomware attacks While it is not identical to the malware previously evaluated. it has a number of similarities including language, payload. and algorithms. Which of the following would help the researcher safely compare the code base of the two variants?
A. Virtualized sandbox
B. Vulnerability scanner
C. Software-defined network
D. HTTP interceptor
-
Question 209:
An application has been through a peer review and regression testing and is prepared for release. A security engineer is asked to analyze an application binary to look for potential vulnerabilities prior to wide release. After thoroughly analyzing the application, the engineer informs the developer it should include additional input sanitation in the application to prevent overflows. Which of the following tools did the security engineer MOST likely use to determine this recommendation?
A. Fuzzer
B. HTTP interceptor
C. Vulnerability scanner
D. SCAP scanner
-
Question 210:
An information security officer reviews a report and notices a steady increase in outbound network traffic over the past ten months. There is no clear explanation for the increase The security officer interviews several business units and discovers an unsanctioned cloud storage provider was used to share marketing materials with potential customers. Which of the following services would be BEST for the security officer to recommend to the company?
A. NIDS
B. HIPS
C. CASB
D. SFTP
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.