Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 231:
A company has made it a spending priority to implement security architectures that will be resilient during an attack. Recent incidents have involved attackers leveraging latent vulnerabilities in cryptographic implementations and VPN concentrators to be able to compromise sensitive information. Patches have been slowly released for these emergent vulnerabilities, leaving weeks to months of exposed and vulnerable attack surface. Which of the following approaches would be BEST to increase enterprise resilience during similar future attacks?
A. Implement appliances and software from diverse manufacturers
B. Segment remote VPN users logically from the production LAN
C. Maximize open-source software to benefit from swifter patch releases
D. Upgrade the cryptographic ciphers used on the VPN concentrators
-
Question 232:
An organization is in the process of evaluating service providers for an upcoming migration to cloud-based services for the organization's ERP system. As part of the requirements defined by the project team, regulatory requirements specify segmentation and isolation of the organization's data. Which of the following should the vendor management team identify as a requirement during the procurement process?
A. Public cloud services with single-tenancy IaaS architectures
B. Private cloud services with single-tenancy PaaS services
C. Private cloud services with multitenancy in place for private SaaS environments
D. Public cloud services with private SaaS environments supported by private IaaS backbones
-
Question 233:
An international e-commerce company has identified attack traffic originating from a whitelisted third party's IP address used to mask the third party's internal network. The security team needs to block the attack traffic without impacting the vendor's services. Which of the following is the BEST approach to identify the threat?
A. Ask the third-party vendor to block the attack traffic
B. Configure the third party's proxy to begin sending X-Forwarded-For headers
C. Configure the e-commerce company's IPS to inspect HTTP traffic
D. Perform a vulnerability scan against the network perimeter and remediate any issues identified
-
Question 234:
A security analyst is reviewing the following pseudo-output snippet after running the command less /tmp/file.tmp.
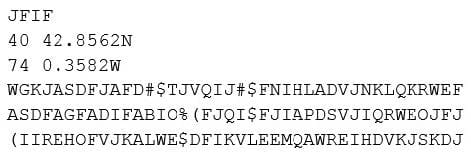
The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
A. Deploy a solution to sanitize geotagging information
B. Install software to wipe data remnants on servers
C. Enforce proper input validation on mission-critical software
D. Implement a digital watermarking solution
-
Question 235:
Ann, a security manager, is reviewing a threat feed that provides information about attacks that allow a malicious user to gain access to private contact lists. Ann receives a notification that the vulnerability can be exploited within her environment. Given this information, Ann can anticipate an increase in:
A. vishing attacks
B. SQL injections attacks
C. web application attacks
D. brute-force attacks
-
Question 236:
A company wants to configure its wireless network to require username and password authentication. Which of the following should the system administrator implement?
A. WPS
B. PEAP
C. TKIP
D. PKI
-
Question 237:
A security administrator adding a NAC requirement for all VPN users to ensure the connecting devices are compliant with company policy. Which of the following items provides the HIGHEST assurance to meet this requirement?
A. Implement a permanent agent.
B. Install antivirus software.
C. Use an agentless implementation.
D. Implement PKI.
-
Question 238:
An organization is concerned that its hosted web servers are not running the most updated version of software. Which of the following would work BEST to help identify potential vulnerabilities?
A. hping3 -S comptia.org -p 80
B. nc -1 -v comptia.org -p 80
C. nmap comptia.org -p 80 -sV
D. nslookup -port=80 comptia.org
-
Question 239:
A security manager needed to protect a high-security data center, so the manager installed a mantrap that can detect an employee's heartbeat, weight, and badge. Which of the following did the security manager implement?
A. A physical control
B. A corrective control
C. A compensating control
D. A managerial control
-
Question 240:
Which of the following are the MOST likely vectors for the unauthorized or unintentional inclusion of vulnerable code in a software company's final software releases? (Choose two.)
A. Unsecure protocols
B. Use of penetration-testing utilities
C. Weak passwords
D. Included third-party libraries
E. Vendors/supply chain
F. Outdated anti-malware software
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.