Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 191:
The SOC has noticed an unusual volume of traffic coming from an open WiFi guest network that appears correlated with a broader network slowdown The network team is unavailable to capture traffic but logs from network services are available
1.
No users have authenticated recently through the guest network's captive portal
2.
DDoS mitigation systems are not alerting
3.
DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
A. Block all outbound traffic from the guest network at the border firewall
B. Verify the passphrase on the guest network has not been changed.
C. Search antivirus logs for evidence of a compromised company device
D. Review access pent fogs to identify potential zombie services
-
Question 192:
An enterprise solution requires a central monitoring platform to address the growing networks of various departments and agencies that connect to the network. The current vendor products are not adequate due to the growing number of
heterogeneous devices.
Which of the following is the primary concern?
A. Scalability
B. Usability
C. Accountability
D. Performance
-
Question 193:
A company is in the process of re-architecting its sensitive system infrastructure to take advantage of on-demand computing through a public cloud provider The system to be migrated is sensitive with respect to latency availability, and integrity The infrastructure team agreed to the following
1.
Application and middleware servers will migrate to the cloud"; Database servers will remain on-site
2.
Data backup wilt be stored in the cloud
Which of the following solutions would ensure system and security requirements are met?
A. Implement a direct connection from the company to the cloud provider
B. Use a cloud orchestration tool and implement appropriate change control processes
C. Implement a standby database on the cloud using a CASB for data-at-rest security
D. Use multizone geographic distribution with satellite relays
-
Question 194:
A company recently experienced a period of rapid growth, and it now needs to move to a more scalable cloud-based solution Historically. salespeople have maintained separate systems for information on competing customers to prevent the inadvertent disclosure of one customer's information to another customer Which of the following would be the BEST method to provide secure data separation?
A. Use a CRM tool to separate data stores
B. Migrate to a single-tenancy cloud infrastructure
C. Employ network segmentation to provide isolation among salespeople
D. Implement an open-source public cloud CRM
-
Question 195:
An application development company implements object reuse to reduce life-cycle costs for the company and its clients Despite the overall cost savings, which of the following BEST describes a security risk to customers inherent within this model?
A. Configurations of applications will affect multiple products.
B. Reverse engineering of applications will lead to intellectual property loss
C. Software patch deployment will occur less often
D. Homogeneous vulnerabilities will occur across multiple products
-
Question 196:
A security analyst is reviewing weekly email reports and finds an average of 1.000 emails received daily from the internal security alert email address. Which of the following should be implemented?
A. Tuning the networking monitoring service
B. Separation of duties for systems administrators
C. Machine learning algorithms
D. DoS attack prevention
-
Question 197:
An internal penetration tester finds a legacy application that takes measurement input made in a text box and outputs a specific string of text related to industry requirements. There is no documentation about how this application works, and the source code has been lost. Which of the following would BEST allow the penetration tester to determine the input and output relationship?
A. Running an automated fuzzer
B. Constructing a known cipher text attack
C. Attempting SQL injection commands
D. Performing a full packet capture
E. Using the application in a malware sandbox
-
Question 198:
A company is purchasing an application that will be used to manage all IT assets as well as provide an incident and problem management solution for IT activity The company narrows the search to two products. Application A and Application B; which meet all of its requirements. Application A is the most cost-effective product, but it is also the riskiest so the company purchases Application B. Which of the following types of strategies did the company use when determining risk appetite?
A. Mitigation
B. Acceptance
C. Avoidance
D. Transfer
-
Question 199:
A company is the victim of a phishing and spear-phishing campaign Users are Clicking on website links that look like common bank sites and entering their credentials accidentally A security engineer decides to use a layered defense to prevent the phishing or lessen its impact Which of the following should the security engineer implement? (Select TWO)
A. Spam filter
B. Host intrusion prevention
C. Client certificates
D. Content filter
E. Log monitoring
F. Data loss prevention
-
Question 200:
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block:
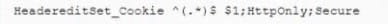
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
A. Ensure session IDs are generated dynamically with each cookie request
B. Prevent cookies from being transmitted to other domain names
C. Create a temporary space on the user's drive root for ephemeral cookie storage
D. Enforce the use of plain text HTTP transmission with secure local cookie storage
E. Add a sequence ID to the cookie session ID while in transit to prevent CSRF.
F. Allow cookie creation or updates only over TLS connections
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.