Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 101:
A security administrator wants to implement an MDM solution to secure access to company email and files in a BYOD environment. The solution must support the following requirements:
1.
Company administrators should not have access to employees' personal information.
2.
A rooted or jailbroken device should not have access to company sensitive information.
Which of the following BEST addresses the associated risks?
A. Code signing
B. VPN
C. FDE
D. Containerization
-
Question 102:
A company suspects a web server may have been infiltrated by a rival corporation. The security engineer reviews the web server logs and finds the following:

ls -l -a /usr/beinz/public; cat ./config/db.yml
The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:
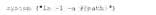
system {"ls -l -a #(patch)"}
Which of the following is an appropriate security control the company should implement?
A. Restrict directory permission to read-only access.
B. Use server-side processing to avoid XSS vulnerabilities in path input.
C. Separate the items in the system call to prevent command injection.
D. Parameterize a query in the path variable to prevent SQL injection.
-
Question 103:
A company's claims processed department has a mobile workforce that receives a large number of email submissions from personal email addresses. An employees recently received an email that approved to be claim form, but it installed malicious software on the employee's laptop when was opened.
A. Impalement application whitelisting and add only the email client to the whitelist for laptop in the claims processing department.
B. Required all laptops to connect to the VPN before accessing email.
C. Implement cloud-based content filtering with sandboxing capabilities.
D. Install a mail gateway to scan incoming messages and strip attachments before they reach the mailbox.
-
Question 104:
During the migration of a company's human resources application to a PaaS provider, the Chief Privacy Officer (CPO) expresses concern the vendor's staff may be able to access data within the migrating applications. The application stack
includes a multitier architecture and uses commercially available, vendor-supported software packages.
Which of the following BEST addresses the CPO's concerns?
A. Execute non-disclosure agreements and background checks on vendor staff.
B. Ensure the platform vendor implement date-at-rest encryption on its storage.
C. Enable MFA to the vendor's tier of the architecture.
D. Impalement a CASB that tokenizes company data in transit to the migrated applications.
-
Question 105:
A corporation with a BYOD policy is very concerned about issues that may arise from data ownership. The corporation is investigating a new MDM solution and has gathered the following requirements as part of the requirements-gathering phase.
1.
Each device must be issued a secure token of trust from the corporate PKI.
2.
All corporate application and local data must be able to deleted from a central console.
3.
Cloud storage and backup applications must be restricted from the device.
4.
Devices must be on the latest OS version within three weeks of an OS release.
Which of the following should be feature in the new MDM solution to meet these requirement? (Select TWO.)
A. Application-based containerization
B. Enforced full-device encryption
C. Mandatory acceptance of SCEP system
D. Side-loaded application prevention
E. Biometric requirement to unlock device
F. Over-the-air restriction
-
Question 106:
A security analyst is reviewing an endpoint that was found to have a rookit installed. The rootkit survived multiple attempts to clean the endpoints, as well as an attempt to reinstall the QS. The security analyst needs to implement a method to prevent other endpoint from having similar issues. Which of the following would BEST accomplish this objective?
A. Utilize measured boot attestation.
B. Enforce the secure boot process.
C. Reset the motherboard's TPM chip.
D. Reinstall the OS with known-good media.
E. Configure custom anti-malware rules.
-
Question 107:
A system engineer is reviewing output from a web application vulnerability scan. The engineer has determined data is entering the application from an untrusted source and is being used to construct a query dynamically. Which of the following code snippets would BEST protect the application against an SQL injection attack?

A. String input = request.getParameter ("SegNo"); String characterPattern = "[0-9a-zA-Z]" If (! Input. Matches (characterPattern)) out.println ("Invalid Input");
B. '/>
C. catch (Exception e) if (log.isDebugEnabled ()) log.debug (context, EVENTS.ADHOC, "CaughtInvalidGSMException Exception --"
+ e.tostring ());
D.
E. Option A
F. Option B
G. Option C
H. Option D
-
Question 108:
A company's IT department currently performs traditional patching, and the servers have a significant longevity that may span over five years. A security architect is moving the company toward an immune server architecture in which servers are replaced rather than patched. Instead of having static servers for development, test, and production, the severs will move from environment to environment dynamically. Which of the following are required to move to this type of architecture? (Select Two.)
A. Network segmentation
B. Forward proxy
C. Netflow
D. Load balancers
E. Automated deployments
-
Question 109:
A cloud architect needs to isolate the most sensitive portion of the network while maintaining hosting in a public cloud Which of the following configurations can be employed to support this effort?
A. Create a single-tenancy security group in the public cloud that hosts only similar types of servers
B. Privatize the cloud by implementing an on-premises instance.
C. Create a hybrid cloud with an on-premises instance for the most sensitive server types.
D. Sandbox the servers with the public cloud by server type
-
Question 110:
A security administrator is opening connectivity on a firewall between Organization A and Organization B Organization B just acquired Organization A. Which of the following risk mitigation strategies should the administrator implement to reduce the risk involved with this change?
A. DLP on internal network nodes
B. A network traffic analyzer for incoming traffic
C. A proxy server to examine outgoing web traffic
D. IPS/IDS monitoring on the new connection
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.