Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 91:
Which of the following is the MOST likely reason an organization would decide to use a BYOD policy?
A. It enables employees to use the devices they are already own, thus reducing costs.
B. It should reduce the number of help desk and tickets significantly.
C. It is most secure, as the company owns and completely controls the devices.
D. It is the least complex method for systems administrator to maintain over time.
-
Question 92:
A security is testing a server finds the following in the output of a vulnerability scan:

Which of the following will the security analyst most likely use NEXT to explore this further?
A. Exploitation framework
B. Reverse engineering tools
C. Vulnerability scanner
D. Visualization tool
-
Question 93:
A company recently deployed an agent-based DLP solution to all laptop in the environment. The DLP solution is configured to restrict the following:
1.
USB ports
2.
FTP connections
3.
Access to cloud-based storage sites
4.
Outgoing email attachments
5.
Saving data on the local C: drive
6.
Despite these restrictions, highly confidential data was from a secure fileshare in the research department.
Which of the following should the security team implement FIRST?
A. Application whitelisting for all company-owned devices
B. A secure VDI environment for research department employees
C. NIDS/NIPS on the network segment used by the research department
D. Bluetooth restriction on all laptops
-
Question 94:
Ann, a user' brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst examines the laptop and obtains the following output.
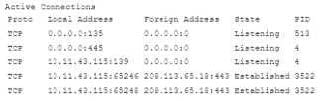
Which of the following will the analyst most likely use NEXT?
A. Process explorer
B. Vulnerability scanner
C. Antivirus
D. Network enumerator
-
Question 95:
A hospital is deploying new imaging softwares that requires a web server for access to image for both local and remote users. The web server allows user authentication via secure LDAP. The information security officer wants to ensure the server does not allow unencrypted access to the imaging server by using Nmap to gather additional information. Given the following:
1.
The imaging server IP is 192.168.101.24
2.
The domain controller IP is 192.168.100.1
3.
The client machine IP is 192.168.200.37
Which of the following should be used to confirm this is the only open post on the web server?
A. nmap "p 80,443 192.168.101.24
B. nmap "p 80,443,389,636 192.168.100.1
C. nmap "p 80,389 192.168.200.37
D. nmap "p" 192.168.101.24
-
Question 96:
A security manager wants to implement a policy that will management with the ability to monitor employees' activities with minimum impact to productivity.
Which of the following policies Is BEST suited for this scenario?
A. Separation of duties
B. Mandatory vacations
C. Least privilege
D. Incident response
-
Question 97:
When of the following is the BEST reason to implement a separation of duties policy?
A. It minimizes the risk of Dos due to continuous monitoring.
B. It eliminates the need to enforce least privilege by logging all actions.
C. It increases the level of difficulty for a single employee to perpetrate fraud.
D. it removes barriers to collusion and collaboration between business units.
-
Question 98:
While traveling to another state, the Chief Financial (CFO) forgot to submit payroll for the company. The CFO quickly gained to the corporate through the high-speed wireless network provided by the hotel and completed the desk. Upon returning from the business trip, the CFO was told no one received their weekly pay due to a malware on attack on the system. Which of the following is the MOST likely of the security breach?
A. The security manager did not enforce automate VPN connection.
B. The company's server did not have endpoint security enabled.
C. The hotel and did require a wireless password to authenticate.
D. The laptop did not have the host-based firewall properly configured.
-
Question 99:
Which of the following is MOST likely to be included in a security services SLA with a third-party vendor?
A. The standard of quality for anti-malware engines
B. Parameters for applying critical patches
C. The validity of program productions
D. Minimum bit strength for encryption-in-transit.
-
Question 100:
A company runs a well ttended, on-premises fitness club for its employees, about 200 of them each day. Employees want to sync center's login and attendance program with their smartphones. Human resources, which manages the contract for the fitness center, has asked the security architecture to help draft security and privacy requirements.
Which of the following would BEST address these privacy concerns?
A. Use biometric authentication.
B. Utilize geolocation/geofencing.
C. Block unauthorized domain bridging.
D. Implement containerization
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.