Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 121:
A creative services firm has a limited security budget and staff. Due to its business model, the company sends and receives a high volume of files every day through the preferred method defined by its customers. These include email, secure file transfers, and various cloud service providers. Which of the following would BEST reduce the risk of malware infection while meeting the company's resource requirements and maintaining its current workflow?
A. Configure a network-based intrusion prevention system
B. Contract a cloud-based sandbox security service.
C. Enable customers to send and receive files via SFTP
D. Implement appropriate DLP systems with strict policies.
-
Question 122:
A software development firm wants to validate the use of standard libraries as part of the software development process Each developer performs unit testing prior to committing changes to the code repository. Which of the following activities would be BEST to perform after a commit but before the creation of a branch?
A. Static analysis
B. Heuristic analysis
C. Dynamic analysis
D. Web application vulnerability scanning
E. Penetration testing
-
Question 123:
An enterprise is configuring an SSL client-based VPN for certificate authentication. The trusted root certificate from the CA is imported into the firewall, and the VPN configuration in the firewall is configured for certificate authentication. Signed certificates from the trusted CA are distributed to user devices. The CA certificate is set as trusted on the end-user devices, and the VPN client is configured on the end-user devices When the end users attempt to connect however, the firewall rejects the connection after a brief period Which of the following is the MOST likely reason the firewall rejects the connection?
A. In the firewall, compatible cipher suites must be enabled
B. In the VPN client, the CA CRL address needs to be specified manually
C. In the router, IPSec traffic needs to be allowed in bridged mode
D. In the CA. the SAN field must be set for the root CA certificate and then reissued
-
Question 124:
An electric car company hires an IT consulting company to improve the cybersecurity of us vehicles. Which of the following should achieve the BEST long-term result for the company?
A. Designing Developing add-on security components for fielded vehicles
B. Reviewing proposed designs and prototypes for cybersecurity vulnerabilities
C. Performing a cyber-risk assessment on production vehicles
D. Reviewing and influencing requirements for an early development vehicle
-
Question 125:
A company's human resources department recently had its own shadow IT department spin up ten VMs that host a mixture of differently labeled data types (confidential and restricted) on the same VMs Which of the following cloud and visualization considerations would BEST address the issue presented in this scenario?
A. Vulnerabilities associated with a single platform hosting multiple data types on VMs should have been considered
B. Vulnerabilities associated with a single server hosting multiple data types should have been considered.
C. Type 1vs Type 2 hypervisor approaches should have been considered
D. Vulnerabilities associated with shared hosting services provided by the IT department should have been considered.
-
Question 126:
A technician uses an old SSL server due to budget constraints and discovers performance degrades dramatically after enabling PFS The technician cannot determine why performance degraded so dramatically A newer version of the SSL server does not suffer the same performance degradation. Performance rather than security is the main priority for the technician.
The system specifications and configuration of each system are listed below:
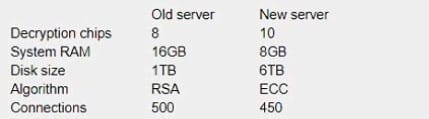
Which of the following is MOST likely the cause of the degradation in performance and should be changed?
A. Using ECC
B. Using RSA
C. Disk size
D. Memory size
E. Decryption chips
F. Connection requests
-
Question 127:
An organization's mobile device inventory recently provided notification that a zero-day vulnerability was identified in the code used to control the baseband of the devices. The device manufacturer is expediting a patch, but the rollout will take several months Additionally several mobile users recently returned from an overseas trip and report their phones now contain unknown applications, slowing device performance Users have been unable to uninstall these applications, which persist after wiping the devices Which of the following MOST likely occurred and provides mitigation until the patches are released?
A. Unauthentic firmware was installed, disable OTA updates and carrier roaming via MDM.
B. Users opened a spear-phishing email: disable third-party application stores and validate all signed code prior to execution.
C. An attacker downloaded monitoring applications; perform a full factory reset of the affected devices.
D. Users received an improperly encoded emergency broadcast message, leading to an integrity loss condition; disable emergency broadcast messages
-
Question 128:
A consultant is planning an assessment of a customer-developed system. The system consists of a custom-engineered board with modified open-source drivers and a one-off management GUI The system relies on two- factor authentication for interactive sessions, employs strong certificate-based data-in-transit encryption, and randomly switches ports for each session. Which of the following would yield the MOST useful information?
A. Password cracker
B. Wireless network analyzer
C. Fuzzing tools D. Reverse engineering principles
-
Question 129:
An organization designs and develops safety-critical embedded firmware (inclusive of embedded OS and services) for the automotive industry. The organization has taken great care to exercise secure software development practices for the firmware Of paramount importance is the ability to defeat attacks aimed at replacing or corrupting running firmware once the vehicle leaves production and is in the field Integrating, which of the following host and OS controls would BEST protect against this threat?
A. Configure the host to require measured boot with attestation using platform configuration registers extended through the OS and into application space.
B. Implement out-of-band monitoring to analyze the state of running memory and persistent storage and, in a failure mode, signal a check-engine light condition for the operator.
C. Perform reverse engineering of the hardware to assess for any implanted logic or other supply chain integrity violations
D. Ensure the firmware includes anti-malware services that will monitor and respond to any introduction of malicious logic.
E. Require software engineers to adhere to a coding standard, leverage static and dynamic analysis within the development environment, and perform exhaustive state space analysis before deployment
-
Question 130:
A security administrator is concerned about employees connecting their personal devices to the company network. Doing so is against company policy. The network does not have a NAC solution. The company uses a GPO that disables the firewall on all company-owned devices while they are connected to the internal network Additionally, all company-owned devices implement a standard naming convention that uses the device's serial number. The security administrator wants to identify active personal devices and write a custom script to disconnect them from the network Which of the following should the script use to BEST accomplish this task?
A. Recursive DNS logs
B. DHCP logs
C. AD authentication logs
D. RADIUS logs
E. Switch and router ARP tables
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.