Exam Details
Exam Code
:ST0-134Exam Name
:Symantec EndPoint Protection 12.1 Technical AssessmentCertification
:Symantec Certified Security programVendor
:SymantecTotal Questions
:282 Q&AsLast Updated
:
Symantec Symantec Certified Security program ST0-134 Questions & Answers
-
Question 71:
An administrator has defined a rule to allow traffic to and from a specific server by its Fully Qualified Domain Name (FQDN), because the server's IP address varies based on the office in which a client is located. The administrator attempts to verify the rule and finds that the traffic is being blocked. The logs list the IP address of the server instead of its FQDN. What does the administrator need to do within the firewall policy to allow the rule to work correctly?
A. Enable DNS lookup
B. Enable reverses DNS lookup.
C. Disable Smart DNS.
D. Disable NetBIOS Protection
-
Question 72:
A system administrator created a firewall policy that allows certain applications and blocks others. However, some applications are being blocked that should be allowed. Which log should be viewed to troubleshoot this issue?
A. Application log
B. System log
C. Traffic log
D. Control log
-
Question 73:
A company is running the Symantec Endpoint Protection 12.1 firewall and wants to ensure that DNS traffic is allowed. Which feature should be enabled in the firewall policy?
A. DNS exception
B. DNS Lookup
C. Reverse DNS Lookup
D. Smart DNS
-
Question 74:
Refer to the exhibit.
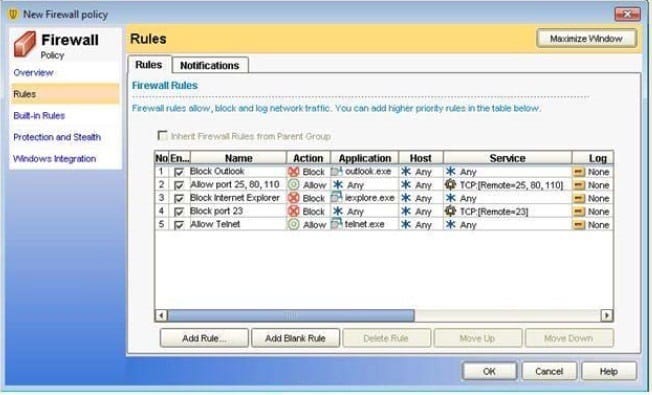
A company has created a specific firewall policy that allows only certain traffic. Which traffic is allowed in the firewall policy displayed in the exhibit?
A. traffic on port 23 from Telnet (telnet.exe)
B. traffic on port 25 from Outlook (outlook.exe)
C. traffic on port 110 from Outlook (outlook.exe)
D. traffic on port 80 from Internet Explorer (iexplore.exe)
E. traffic on port 443 from Internet Explorer (iexplore.exe)
-
Question 75:
A computer is configured in Mixed Control mode. The administrator creates and applies a Firewall policy to the computer that has a rule that allows FTP traffic above the blue line and another rule that blocks LDAP traffic below the blue line. On the computer, local rules are created to allow LDAP traffic and block FTP traffic. Which traffic flow behavior should be expected on the local computer?
A. Both FTP and LDAP traffic are allowed.
B. Both FTP and LDAP traffic are blocked.
C. FTP is blocked and LDAP is allowed.
D. FTP is allowed and LDAP is blocked.
-
Question 76:
A customer reports that users are able to download new files from the internet and execute those files on their own computers. What can be configured to prevent this?
A. Decrease the Download Insight sensitivity.
B. Change the action for unproven files in Download Insight.
C. Change the second action for malicious files in Download Insight.
D. Change the first action for malicious files in Download Insight.
-
Question 77:
An administrator wants to make sure users are warned when they decide to download potentially malicious files. Which option should the administrator configure?
A. the Notifications tab under the admin-defined scan settings
B. the Notifications tab under Auto-Protect settings
C. the Network Protection Security event notification in location-specific settings
D. the Notifications tab under Download Insight settings
-
Question 78:
Refer to the exhibit.
A user runs a full scan on a system and is confused by the "Files trusted" count. Which option will result in the files being left unscanned?
A. Enabling the "Only when files are executed" setting in the Virus and Spyware Protection policy.
B. Enabling the "Do not scan files when trusted processes access the files" setting in the Virus and Spyware Protection policy.
C. Enabling Insight in the Virus and Spyware Protection policy.
D. Enabling the file cache settings in the Virus and Spyware Protection policy.
-
Question 79:
A customer is downloading newly-created company files from an internal website and is being blocked by Download Insight based on reputation. How can the customer prevent this?
A. Change the minimum number of days in the Download Insight settings.
B. Change the minimum number of users in the Download Insight settings.
C. Increase the sensitivity slider in the Download Insight settings.
D. Enable the option to trust files downloaded from an intranet website in the Download Insight settings.
-
Question 80:
What is the likely impact of increasing the Download Insight sensitivity?
A. It would block files that trend towards a poor reputation and decrease false positives.
B. It would allow only files with a good reputation and decrease false positives.
C. It would allow only files that trend toward a good reputation and increases false positives.
D. It would block files that have a poor reputation and decrease false positives.
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ST0-134 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.