Exam Details
Exam Code
:ST0-134Exam Name
:Symantec EndPoint Protection 12.1 Technical AssessmentCertification
:Symantec Certified Security programVendor
:SymantecTotal Questions
:282 Q&AsLast Updated
:May 07, 2025
Symantec Symantec Certified Security program ST0-134 Questions & Answers
-
Question 91:
Acrobat Reader is being targeted by a threat using process injection. Which feature of SONAR is sandboxing Acroread32.exe so that the threat is prevented from dropping its payload?
A. Commercial Application Detection
B. Suspicious Behavior Detection
C. System Change Events
D. Signature Based Detection
-
Question 92:
What could be an adverse effect of activating aggressive mode on the SONAR policy?
A. false negatives
B. false positives
C. performance issues
D. higher rejection rate
-
Question 93:
Which two options are available when configuring high risk detection in SONAR? (Select two.)
A. Block
B. Skip
C. Quarantine
D. Log E. Delete
-
Question 94:
Refer to the exhibit.
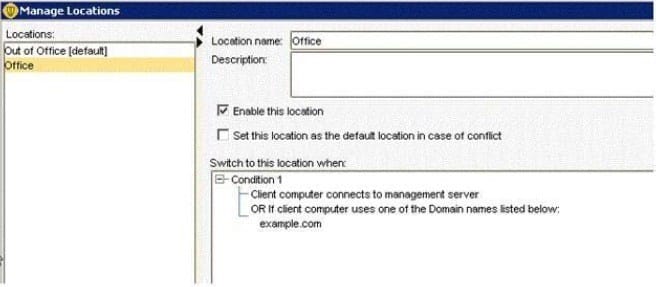
In the use case displayed in the exhibit, why is the administrator unable to save the changes to this file?
A. Application Control is preventing Notepad from accessing the host file.
B. SONAR is set to block host file modifications.
C. Tamper Protection is enabled.
D. The Auto-Protect feature detected a malicious activity.
-
Question 95:
Which technology uses heuristics to scan outbound email?
A. Internet Email Auto-Protect
B. Microsoft Outlook Auto-Protect
C. Lotus Notes Auto-Protect
D. SONAR
-
Question 96:
Which type of email does Internet Email Auto-Protect support?
A. IMAP based email
B. HTTP/s based email
C. SMTP based email
D. Outlook Web Access (OWA)
-
Question 97:
An administrator is modifying a Virus and Spyware Protection policy for a Symantec Endpoint Protection
12.1 (SEP) client because it is demonstrating poor boot performance. Which option should the administrator consider to alleviate this problem?
A. Ensure that Risk Tracer is disabled.
B. Load Auto-Protect during the startup of SEP.
C. Enable File Cache across reboots.
D. Modify the policy to use Insight Cache.
-
Question 98:
A Symantec Endpoint Protection 12.1 administrator has the Virus and Spyware Protection policy configured with Auto-Protect enabled. The administrator is confronted with computer performance issues. Which two options can the administrator use to improve performance? (Select two.)
A. Enable the option to Trust Files on Remote Computers Running Auto-Protect.
B. Enable the Risk Tracer option.
C. Edit the autoprotect.xml and increase the cache value.
D. Enable the option of Network Cache.
E. Enable the Preserve File Times option.
-
Question 99:
A Symantec Endpoint Protection 12.1 client is running a user-defined scan when a scheduled, administrator-defined scan is scheduled to launch. What is the effect on the client?
A. The user-defined scan will be paused in order to launch the administrator-defined scan.
B. The administrator-defined scan will launch after the user-defined scan completes.
C. The user-defined scan will be canceled in order to launch the administrator-defined scan.
D. The administrator-defined scan will be skipped and the user-defined scan will continue.
-
Question 100:
Which protection technology assists in protecting documents in real-time when accessed or modified?
A. SONAR
B. Reputation Scans
C. Auto-Protect
D. Scheduled Scans
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ST0-134 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.