Exam Details
Exam Code
:ST0-134Exam Name
:Symantec EndPoint Protection 12.1 Technical AssessmentCertification
:Symantec Certified Security programVendor
:SymantecTotal Questions
:282 Q&AsLast Updated
:May 15, 2025
Symantec Symantec Certified Security program ST0-134 Questions & Answers
-
Question 61:
Refer to the exhibit.
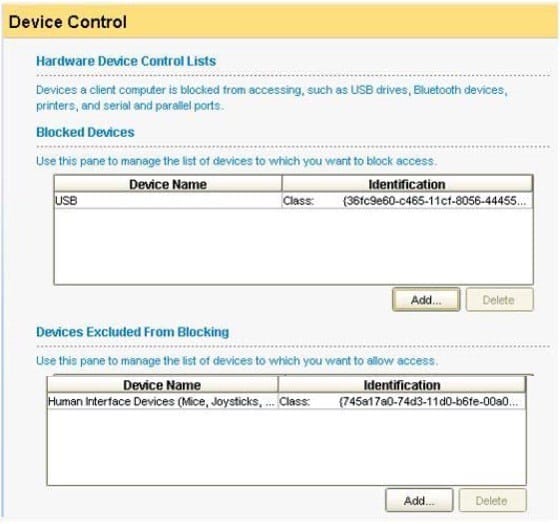
A USB mouse is plugged in to a system that uses the device control displayed in the exhibit. What is the expected behavior?
A. The mouse is blocked until the user adds the device as a local client exception.
B. The mouse is blocked until an administrator adds the device to the exception policy.
C. The mouse will work as normal because the Human Interface Device exclusion takes precedence.
D. The mouse will work as normal because Mouse devices are missing from Blocked Devices.
-
Question 62:
An administrator needs to customize the Application and Device Control policy to exclude all USB devices except for a specific, company-issued USB thumb drive. Which function or program, provided with the Symantec Endpoint Protection 12.1 software, should the administrator use to customize the environment?
A. DevViewer.exe
B. Sep_SupportTool.exe
C. SOIS.exe
D. vietool.exe
-
Question 63:
A company organizes its clients into two groups the Symantec Endpoint Protection Manager (SEPM) group with all the SEPMs and a Desktops group with all other systems. An Application and Device Control policy is used with the "Block modifications to hosts file" rule set enabled. This policy is applied to all groups in the company. How can an administrator modify the hosts file on the SEPM systems, while minimizing risks posed to the company?
A. Withdraw the policy from all clients, modify the hosts files, and reassign the policy.
B. Withdraw the policy from the SEPM group, modify the hosts files, and reassign the policy.
C. Modify the hosts file using an operating system-based system account.
D. Temporarily disable Network Threat Protection on each client when modifying the hosts file.
-
Question 64:
An administrator needs to ensure that a specific network threat can be detected. The attack signatures for this threat may be found across multiple packets. What can the administrator do to ensure the best chance of detecting this threat?
A. Ensure that Symantec IPS signatures are updated.
B. Create custom IPS signatures
C. Enable TCP resequencing
D. Create a Firewall rule for this threat
-
Question 65:
Which Intrusion Prevention feature is updated automatically?
A. Intrusion Prevention custom signatures
B. SNORT syntax
C. Auto-Protect
D. Generic Exploit Blocking
-
Question 66:
An administrator needs to exclude some servers from an Intrusion Prevention System (IPS) policy. When specifying an excluded host in an IPS policy, which two methods can be used? (Select two.)
A. DNS host
B. IP address
C. MAC address
D. DNS domain
E. subnet
-
Question 67:
A company selected Opera 10 as its corporate browser. Drive-by downloads are occurring and SONAR intercepts the resulting scripts. How should the company proceed to minimize the occurrence of drive-by downloads?
A. Upgrade to Opera 11.
B. Use Internet Explorer or Firefox.
C. Enable browser protection.
D. Reboot the Symantec Endpoint Protection client.
-
Question 68:
The Symantec Endpoint Protection 12.1 (SEP) client indicates that the Virus and Spyware Protection (AV) definitions are current, while the Intrusion Prevention System (IPS) signatures are one day older. How can an administrator determine whether this SEP client is up-to-date?
A. The administrator can tell the client is up-to-date because the AV definitions are the latest.
B. The administrator can tell the client is out-of-date because the IPS signatures are old.
C. The administrator needs to review the client Computer Status logs to determine whether the client is up-to-date.
D. The administrator needs to review the Symantec Security Response page to determine whether the client is up-to-date.
-
Question 69:
A company is running the Symantec Endpoint Protection 12.1 firewall with the default policy. At the bottom of the ruleset, there is a rule called "Block all other IP traffic and log" which will block all IP traffic. A financial application is being blocked by this rule. What should be changed to allow the application without sacrificing security?
A. The existing rule should be changed.
B. A new rule should be created.
C. An existing rule should be deleted.
D. An existing rule needs to be reordered.
-
Question 70:
A company has a firewall policy with a rule that allows all applications on all ports. An administrator needs to modify the policy so that it allows Internet Explorer to communicate to any website, but only on port 80 and 443. In addition, the company only wants this modification to affect traffic from Internet Explorer. The administrator created a new rule at the top of the ruleset that allows Internet Explorer on port 80 and 443. Which step should the administrator take next?
A. Move the new rule below the Allow Applications rule.
B. Delete the Allow All Applications rule.
C. Modify the Allow All Applications rule to exclude Internet Explorer.
D. Create a new rule above the Allow All Applications rule to block Internet Explorer.
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ST0-134 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.