Exam Details
Exam Code
:ST0-134Exam Name
:Symantec EndPoint Protection 12.1 Technical AssessmentCertification
:Symantec Certified Security programVendor
:SymantecTotal Questions
:282 Q&AsLast Updated
:Apr 29, 2025
Symantec Symantec Certified Security program ST0-134 Questions & Answers
-
Question 51:
Which two criteria can be used to determine hosts in a host group? (Select two.)
A. MAC address
B. registry key
C. management server connection
D. DNS host network connection type
-
Question 52:
According to Symantec best practices, which two tasks should be completed after creating file fingerprint lists, but prior to enabling System Lockdown? (Select two.)
A. Add any approved applications.
B. Move the Symantec Endpoint Protection Managers to a separate group.
C. Log unapproved applications.
D. Run the checksum.exe command on the clients.
E. Enable application learning.
-
Question 53:
Company A acquires Company B. Company B has 200 employees. Multiple firewall rules, based on collections of client addresses, are required to allow the new employees access to Company A's resources and permissions to use approved network applications. Which feature should be used to minimize the amount of time needed to create rules for these new clients?
A. Application rule sets
B. Host groups
C. Built-in rules
D. Network Services
-
Question 54:
What is a benefit of enabling Browser Intrusion Prevention?
A. It uses a reputation and cloud-based technology to monitor and identify attacks on Internet Explorer and Firefox.
B. It sends traffic results to a dedicated Symantec server to determine whether the traffic is legitimate. C. It monitors traffic on supported browsers by using attack signatures and heuristics.
C. It improves performance by allowing clients to share Intrusion Prevention scan results.
-
Question 55:
A company creates free web access computers for use in public areas, such as airports. The software provided on the computers will be static and the systems must be secure. What should be used to restrict unauthorized applications from running on these computers?
A. client security settings and Tamper Protection
B. blocked devices in an Application and Device Control policy
C. file fingerprint list and System Lockdown
D. custom IPS signatures in an Intrusion Prevention policy
-
Question 56:
An administrator enables the "Learn applications that run on the client computers" setting for a group of clients. Later, when using the Search for Applications function, the administrator is unable to find results. What is the cause of the problem?
A. The administrator is a limited administrator without rights to view reports.
B. Application learning is disabled under communication settings at the site level.
C. Submissions are disabled on the Symantec Endpoint Protection client by the user.
D. Pull mode is enabled and is unsupported by application learning.
-
Question 57:
An administrator enabled the default application control rule "Block writing to USB Drives", but needs to modify it so that clients can write to a specific make and model of company-authorized, encrypted USB drive. How should the administrator proceed?
A. Edit the rule set and add the device ID to the exceptions.
B. Edit the rule set and add a condition after the block condition to allow access to the specific device.
C. Edit the rule set and add a rule after the block rule to allow access to the specific device.
D. Using DevViewer, plug the device into the Symantec Endpoint Protection Manager and select "Add Device to Manager".
-
Question 58:
An administrator is testing a new Application and Device Control policy. One of the rule sets being tested blocks the notepad.exe application from running. After pushing the policy to a test client, the administrator finds that notepad.exe is still able to run. The administrator verifies that the rule set is enabled in the Application and Device Control policy. Which two may be preventing the policy from performing the application blocking? (Select two.)
A. An Application exception has been configured in the Exceptions policy.
B. System Lockdown has been configured for the client.
C. Network Threat Protection needs to be installed on the client.
D. The rule set is in the "Test (log only)" mode.
E. A rule set with conflicting rules exists higher up in the policy.
-
Question 59:
When the Symantec Endpoint Protection 12.1 client firewall defends against a MAC spoof attack, what does it drop?
A. ICMP response
B. IP redirect
C. gratuitous ARP
D. TCP reset
-
Question 60:
Refer to the exhibit.
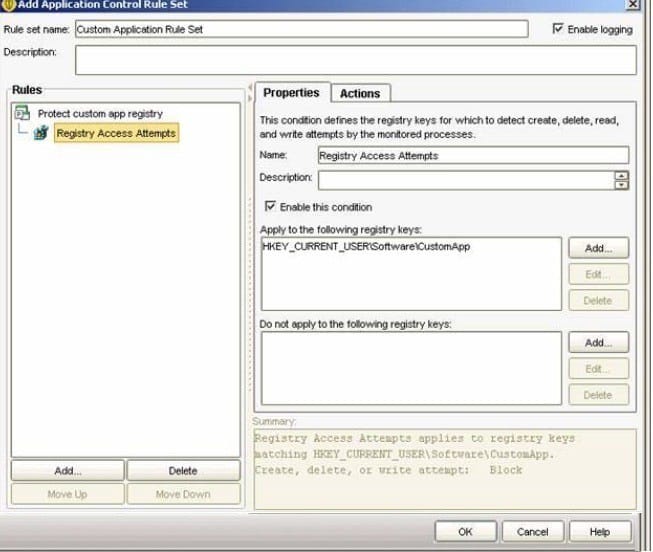
A company is using a custom application that writes its application settings in the registry. An administrator plans to prevent users from modifying these values, while ensuring that the custom application still functions correctly. An Application and Device Control policy is created with an application rule to block access to create, delete, or write attempts, for the registry keys used by the custom application. One way to ensure users are prohibited from the registry keys, but the custom application can still modify them, is to add an Application Control exception for the custom application. What is another way to ensure this functionality?
A. Add an application rule to allow access to create, delete, or write attempts, to the custom application folder.
B. Add an application rule to allow access to read attempts for the registry keys.
C. Add an application rule set that allows access to read attempts for the registry keys.
D. Add an application rule to allow access to create, delete, or write attempts for the custom application.
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ST0-134 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.