Exam Details
Exam Code
:JN0-332Exam Name
:Juniper Networks Certified Internet Specialist, SEC (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:519 Q&AsLast Updated
:Jun 06, 2025
Juniper Juniper Certifications JN0-332 Questions & Answers
-
Question 141:
-- Exhibit
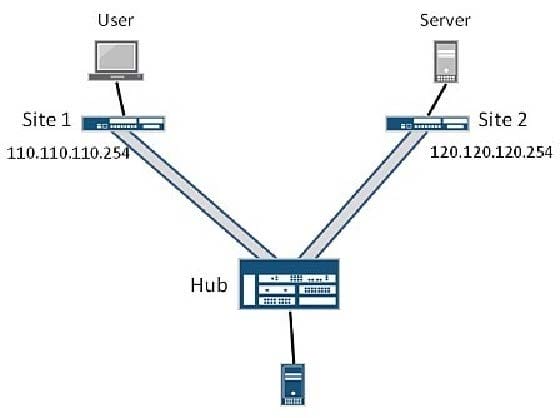
-- Exhibit -
Click the Exhibit button.
You are asked to configure a hub-and-spoke VPN. All the VPN components have been configured, and you are able to ping the remote tunnel interfaces at Site 1 and Site 2 from the Hub site as shown in the exhibit. The Hub site's external interface is in security zone untrust and the st0 interfaces from each site are in security zone DMZ. Users in Site 2 are unable to connect to a Web server in Site 1.
Which additional step is required at the hub site for users to access the Web server?
A. Configure a VPN between Site 1 and Site 2.
B. Configure a policy in the untrust zone that allows traffic between the sites.
C. Configure a policy in the VPN zone that allows traffic between the sites.
D. Configure a policy between the VPN and untrust zones.
-
Question 142:
-- Exhibit -
[edit security policies]
user@host# show
from-zone hr to-zone internet {
policy internet-access {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
policy clean-up {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
-- Exhibit -
Click the Exhibit button.
You want to permit access to the Internet from the hr zone during a specified time.
Which configuration will accomplish this task?
A. Configure a scheduler, apply it to a new policy, and insert it after internet-access to permit Internet access.
B. Configure a scheduler and apply it to the policy internet-access to deny Internet access.
C. Configure a scheduler and apply it to the policy internet-access to permit Internet access.
D. Configure a scheduler, apply it to a new policy, and insert it before internet-access to permit Internet access.
-
Question 143:
-- Exhibit -- Exhibit -
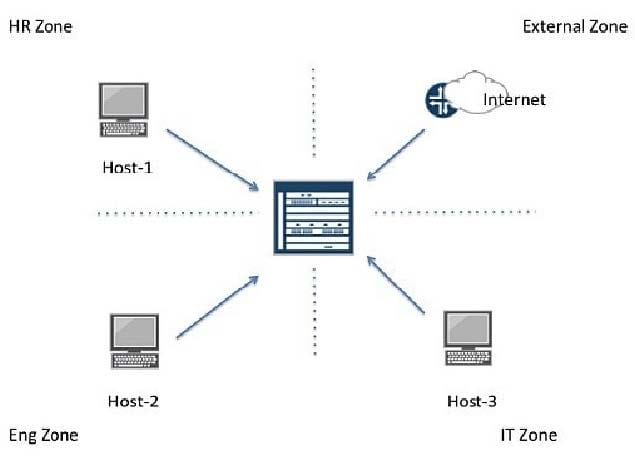
Click the Exhibit button.
Referring to the exhibit, which policy will allow traffic from Host 1, Host 2, and Host 3 to the Internet?
A. [edit security policies] user@host# show global { policy allow-internet { match { source-address [ host-1 host-2 host-3 ]; destination-address any; application any; } then permit;
B. [edit security policies] user@host# show from-zone all to-zone all { policy allow-internet { match { source-address [ host-1 host-2 host-3 ]; destination-address any; application any; } then permit;
C. [edit security policies] user@host# show default { policy allow-internet { match {
source-address [ host-1 host-2 host-3 ];
destination-address any;
application any;
}
then permit;
D. [edit security policies] user@host# show from-zone any to-zone any { policy allow-internet { match { source-address [ host-1 host-2 host-3 ]; destination-address any; application any; } then permit;
-
Question 144:
-- Exhibit -
security {
policies {
from-zone TRUST to-zone UNTRUST {
policy allow-all {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
policy allow-hosts {
match {
source-address hosts;
destination-address any;
application junos-http;
}
then {
permit;
}
scheduler-name block-hosts;
}
policy deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
}
schedulers {
scheduler block-hosts {
daily {
start-time 10:00:00 stop-time 18:00:00;
}
}
}
-- Exhibit -
Click the Exhibit button.
Referring to the exhibit, you have configured a scheduler to allow hosts access to the Internet during
specific times. You notice that hosts are unable to access the Internet.
What is blocking hosts from accessing the Internet?
A. The policy allow-all should have the scheduler applied.
B. The policy allow-hosts should match on source-address any.
C. The policy allow-hosts should have an application of any.
D. The policy allow-all should have a then statement of permit.
-
Question 145:
-- Exhibit -security {
policies {
from-zone TRUST to-zone UNTRUST {
policy hosts-allow {
match {
source-address hosts;
destination-address any;
application any;
}
then {
permit;
}
scheduler-name block-hosts;
}
policy allow {
match {
source-address any;
destination-address any;
application junos-http;
}
then {
permit;
}
}
policy deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
}
schedulers {
scheduler block-hosts {
daily {
start-time 10:00:00 stop-time 18:00:00;
}
}
}
-- Exhibit -
Click the Exhibit button.
Referring to the exhibit, you have configured a scheduler to allow hosts access to the Internet during
specific times. You notice that hosts are still accessing the Internet during times outside of the scheduler's
parameters.
What is allowing hosts to access the Internet?
A. The policy allow is allowing hosts access during unscheduled hours.
B. The policy hosts-allow should have a then statement of deny.
C. The policy hosts-allow should have an application of junos-http.
D. The policy deny should have the scheduler applied.
-
Question 146:
-- Exhibit
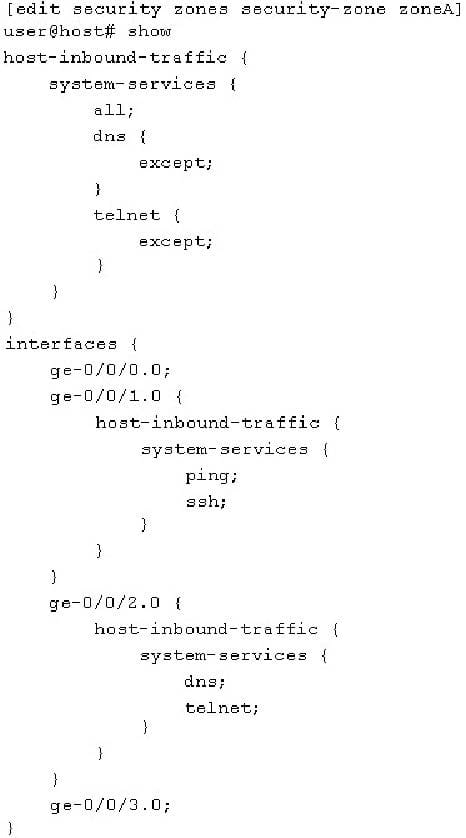
-- Exhibit -Click the Exhibit button.
Referring to the exhibit, which two services are allowed on the ge-0/0/2.0 interface? (Choose two.)
A. Ping
B. DNS
C. Telnet
D. SSH
-
Question 147:
-- Exhibit -
[edit security policies from-zone untrust to-zone junos-host] user@host# show
policy allow-management {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
[edit security zones security-zone untrust]
user@host# show
host-inbound-traffic {
protocols {
ospf;
}
}
interfaces {
ge-0/0/0.0;
}
-- Exhibit -
Click the Exhibit button.
Referring to the exhibit, you want to be able to manage your SRX Series device from the Internet using
SSH. You have created a security policy to allow the traffic to flow into the SRX device.
Which additional configuration step is required?
A. Define the junos-host zone and add the SSH service to it.
B. Add the SSH service to the untrust zone.
C. Define the junos-host zone, add the SSH service and the loopback interface to it.
D. Rewrite the security policy to allow SSH traffic from the untrust zone to the global zone.
-
Question 148:
-- Exhibit -
[edit interfaces]
ge-0/0/1 {
unit 0 {
family ethernet-switching {
vlan {
members vlan-trust;
}
}
}
}
[edit vlans]
vlan-trust {
vlan-id 3;
l3-interface vlan.0;
}
-- Exhibit -
Click the Exhibit button.
Referring to the exhibit, you need to allow ping traffic into interface ge-0/0/1.
Which configuration step will accomplish this task?
A. set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system- services ping
B. set security zones security-zone trust interfaces ge-0/0/1 host-inbound-traffic system-services ping
C. set security zones security-zone trust interfaces vlan-trust host-inbound-traffic system-services ping
D. set security zones security-zone trust interfaces vlan.0 host-inbound-traffic system-services ping
-
Question 149:
You are configuring a blacklist for Web filtering on a branch SRX Series device.
Which two URL patterns are valid? (Choose two.)
A. http://www.company.com/*
B. http://*.company.com
C. www.company.com
D. 1.2.3.4
-
Question 150:
Which two criteria does the enhanced Web filtering solution use to make decisions? (Choose two.)
A. site reputation
B. keyword in the document
C. results of antivirus scan
D. category
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-332 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.