Exam Details
Exam Code
:JN0-332Exam Name
:Juniper Networks Certified Internet Specialist, SEC (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:519 Q&AsLast Updated
:Jun 06, 2025
Juniper Juniper Certifications JN0-332 Questions & Answers
-
Question 131:
-- Exhibit
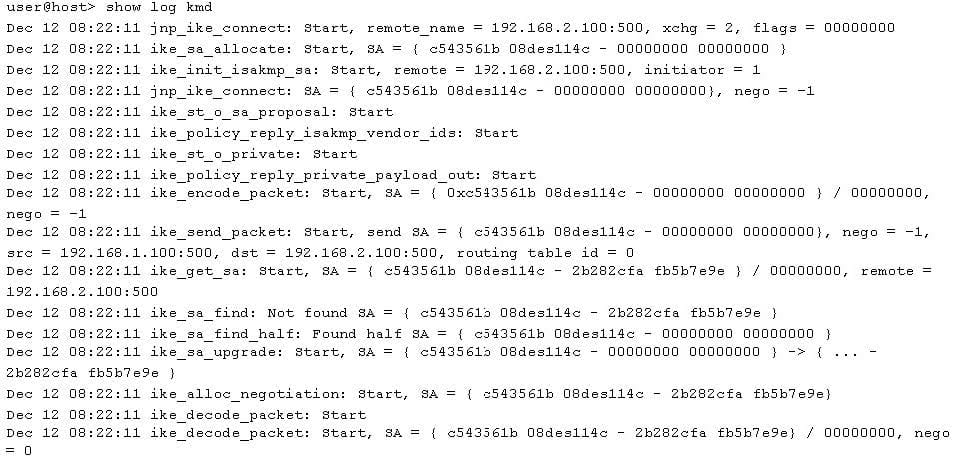
-- Exhibit -
Click the Exhibit button.
You are troubleshooting an IPsec VPN connection between a local SRX Series device using IP address
192.168.1.100 and a remote SRX device using IP address 192.168.2.100. A VPN connection cannot be established. Referring to the exhibit, you examine the kmd log file.
What is the problem?
A. The Phase 2 proposal is invalid.
B. The Phase 1 proposal is invalid.
C. The Phase 1 gateway is invalid.
D. The Phase 2 gateway is invalid.
-
Question 132:
-- Exhibit
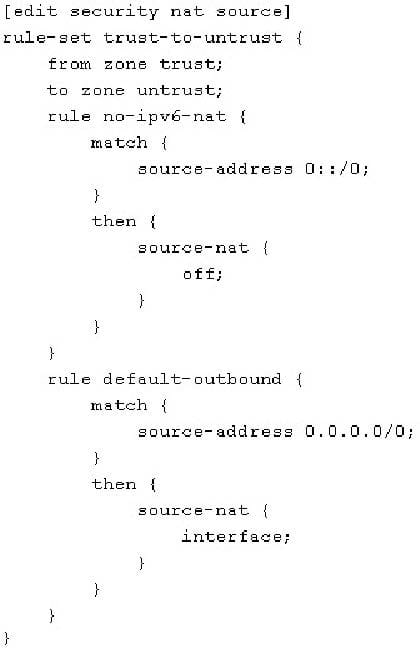
-- Exhibit -Click the Exhibit button.
Referring to the exhibit, which three statements are correct? (Choose three.)
A. Source NAT is configured.
B. Address shifting is configured.
C. Interface-based NAT is configured.
D. Pool-based NAT is configured.
E. IPv6 is configured to bypass NAT.
-
Question 133:
-- Exhibit
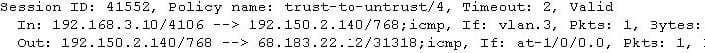
-- Exhibit -
Click the Exhibit button.
A PC in the trust zone is trying to ping a host in the untrust zone.
Referring to the exhibit, which type of NAT is configured?
A. source NAT
B. destination NAT
C. static NAT
D. NAT pool
-
Question 134:
-- Exhibit -
[edit security nat source]
user@host# show
pool snat-pool {
address {
10.10.10.10/32;
10.10.10.11/32;
}
}
pool-utilization-alarm raise-threshold 50 clear-threshold 40; rule-set user-nat {
from zone trust;
to zone untrust;
rule snat {
match {
source-address 0.0.0.0/0;
}
then {
source-nat {
pool {
snat-pool;
}
}
}
}
}
-- Exhibit -
Click the Exhibit button.
Your network management station has generated an alarm regarding NAT utilization based on an SNMP trap received from an SRX Series device.
Referring to the exhibit, which statement is correct about the alarm?
A. The network management station will require manual intervention to clear the alarm.
B. Once utilization is below 40 percent, the Junos OS will send an SNMP trap to the network management station to clear the alarm.
C. Once utilization is below 50 percent, the Junos OS will send an SNMP trap to the network management station to clear the alarm.
D. Once utilization is below 80 percent, the Junos OS will send an SNMP trap to the network management station to clear the alarm.
-
Question 135:
-- Exhibit -
[edit security nat]
user@host# show source
pool pool-one {
address {
68.183.13.0/24;
}
}
rule-set trust-to-untrust {
from zone trust;
to zone untrust;
rule pool-nat {
match {
source-address 10.10.10.1/24;
}
then {
source-nat {
pool {
pool-one;
}
}
}
}
rule no-nat {
match {
destination-address 192.150.2.140/32;
}
then {
source-nat {
off;
}
}
}
}
-- Exhibit -
Click the Exhibit button.
You have implemented source NAT using a source pool for address translation. However, traffic destined
for 192.150.2.140 should not have NAT applied to it. The configuration shown in the exhibit is not working
correctly.
Which change is needed to correct this problem?
A. Insert no-nat before pool-nat.
B. The no-nat rule should be in a separate rule-set.
C. Destination NAT should be used to exclude the traffic destined for 192.150.2.140.
D. Proxy ARP needs to be applied on the 192.150.2.140 address for the rule to function.
-
Question 136:
-- Exhibit -
[edit security nat source]
user@srx# show
pool A {
address {
172.16.52.94/32;
}
}
rule-set 1A {
from zone trust;
to zone untrust;
rule 1 {
match {
source-address 192.168.233.0/24;
}
then {
source-nat {
pool {
A;
} } } } } -- Exhibit -
Click the Exhibit button.
Referring to the exhibit, which two statements are true? (Choose two.)
A. PAT is enabled.
B. PAT is disabled.
C. Address persistence is enabled.
D. Address persistence is disabled.
-
Question 137:
-- Exhibit -
user@srx> show security flow session Session ID. 10702, Policy name: default-permit/4, Timeout: 1794, Valid In: 2.3.4.5/5000 --> 10.1.2.3/22;tcp, IF. fe-0/0/6.0, Pkts: 88444, Bytes: 7009392 Out: 10.1.2.3/22 --> 10.1.1.1/5000;tcp, IF. .local..0, Pkts: 81672, Bytes: 6749337
-- Exhibit -
Click the Exhibit button.
The output of show security flow sessions is shown in the exhibit.
From this output, which type of NAT is configured?
A. interface source NAT
B. static destination NAT
C. static source NAT
D. pool-based source NAT with PAT
-
Question 138:
-- Exhibit -- Exhibit -
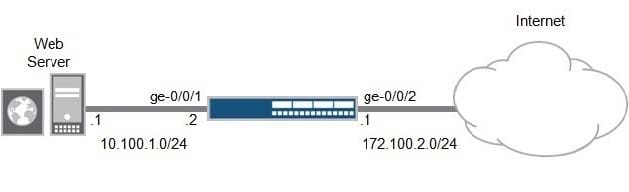
Click the Exhibit button.
Referring to the exhibit, you want to use source NAT to translate the Web server's IP address to the IP address of ge-0/0/2.
Which source NAT type accomplishes this task and always performs PAT?
A. source NAT with address shifting
B. standard pool-based NAT
C. interface-based source NAT
D. reverse source NAT
-
Question 139:
-- Exhibit -- Exhibit -
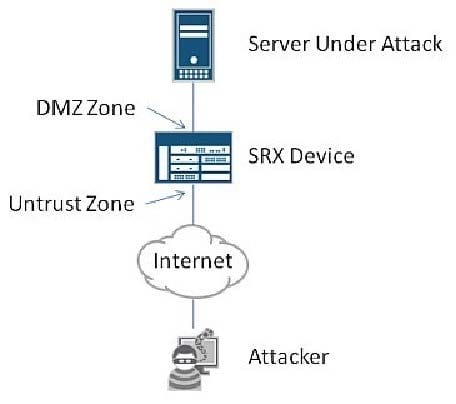
Click the Exhibit button.
A server in the DMZ of your company is under attack. The attacker is opening a large number of TCP connections to your server which causes resource utilization problems on the server. All of the connections from the attacker appear to be coming from a single IP address.
Referring to the exhibit, which Junos Screen option should you enable to limit the effects of the attack while allowing legitimate traffic?
A. Apply the Junos Screen option limit-session source-based-ip to the Untrust security zone.
B. Apply the Junos Screen option limit-session source-based-ip to the DMZ security zone.
C. Apply the Junos Screen option limit-session destination-based-ip to the Untrust security zone.
D. Apply the Junos Screen option limit-session destination-based-ip to the DMZ security zone.
-
Question 140:
-- Exhibit
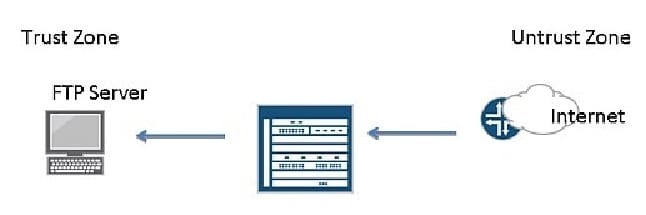
-- Exhibit -Click the Exhibit button.
Referring to the exhibit, you need to allow FTP traffic from the Internet to the FTP server in the Trust zone.
You have built a custom application so that you can modify the timeout value for FTP sessions and have
configured a policy to allow FTP traffic from Untrust to Trust, but the traffic still does not flow. The current
status of the FTP ALG is disabled.
What is the problem?
A. The FTP ALG has not been enabled in the security policy.
B. The FTP ALG has not been enabled in the security zones.
C. The FTP ALG has been disabled on the device.
D. The FTP ALG has not been set in the custom application definition.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-332 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.