Exam Details
Exam Code
:JN0-332Exam Name
:Juniper Networks Certified Internet Specialist, SEC (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:519 Q&AsLast Updated
:Jun 06, 2025
Juniper Juniper Certifications JN0-332 Questions & Answers
-
Question 121:
-- Exhibit -
user@host# show chassis cluster
reth-count 2;
redundancy-group 1 {
node 0 priority 200;
node 1 priority 100;
interface-monitor {
ge-0/0/5 weight 85;
ge-0/0/6 weight 85;
ge-0/0/7 weight 85;
ge-0/0/8 weight 85;
ge-5/0/5 weight 85;
ge-5/0/6 weight 85;
ge-5/0/7 weight 85;
ge-5/0/8 weight 85;
}
}
-- Exhibit -
Click the Exhibit button.
Referring to the exhibit, you have two SRX Series devices in a chassis cluster, and Node 0 is currently the
primary node. You want to ensure that traffic using those interfaces fails over to Node 1 if one interface
goes down.
Which configuration change should be made to ensure failover to Node 1?
A. Decrease the weight of the interfaces to 1.
B. Increase the weight of the interfaces to 255.
C. Increase the weight of the interfaces to between 128 and 254.
D. Decrease the weight of the interfaces to between 1 and 64.
-
Question 122:
-- Exhibit -- Exhibit -

Click the Exhibit button. Referring to the exhibit, failover to Node 0 occurred for Redundancy Group 2 because of an interface failure. The interface has since been restored, but Node 0 is still the primary node for Redundancy Group
2.
Which two actions will restore Node 1 as the primary node for Redundancy Group 2? (Choose two.)
A. Decrease the priority of Node 1 to 100.
B. Increase the priority of Node 1 to 255.
C. Configure preempt under Redundancy Group 2.
D. Manually fail over to Redundancy Group 2.
-
Question 123:
-- Exhibit -
user@host# set interfaces ge-0/0/5 gigether-options redundant-parent reth1 user@host# set interfaces ge5/0/5 gigether-options redundant-parent reth1 user@host# set interfaces reth1.0 family inet address 192.168.1.100/30 user@host# commit [edit interfaces reth1]'unit 0'reth1 needs to be associated with a non-zero redundancy-group error: configuration check-out failed
-- Exhibit -
Click the Exhibit button.
Referring to the exhibit, you have built a chassis cluster, set up a reth, and put interfaces into the reth.
However, when you try to commit the configuration, you receive the error shown in the exhibit.
Which configuration command will correct this error?
A. Set chassis cluster reth-count 2
B. Set chassis cluster redundancy-group 1 interface-monitor reth1
C. Set interfaces reth1 redundant-ether-options redundancy-group 1
D. Set chassis cluster redundancy-group 0 interface-monitor reth1
-
Question 124:
-- Exhibit -- Exhibit -
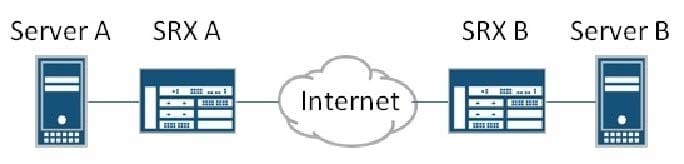
Click the Exhibit button.
Server A is communicating with Server B directly over the Internet. The servers now must begin exchanging additional information through an unencrypted protocol. To protect this new data exchange, you want to establish a VPN tunnel between the two sites that will encrypt just the unencrypted data while leaving the existing communications directly over the Internet.
Which statement would achieve the desired results?
A. Configure a route-based VPN and use filter-based forwarding to direct traffic into the VPN tunnel.
B. Configure a route-based VPN tunnel with traffic engineering to direct traffic into the VPN tunnel.
C. Configure a policy-based VPN with a security policy that matches the unencrypted traffic and directs it into the VPN tunnel.
D. Configure a policy-based VPN tunnel and use filter-based forwarding to direct the unencrypted traffic into interface st0.0.
-
Question 125:
-- Exhibit -
user@host> show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon vsys Port Gateway <131073 ESP:3des/sha1 ac23df79 2532/ unlim - root 4500 1.1.1.1 >131073 ESP:3des/sha1 cbc9281a 2532/ unlim - root 4500 1.1.1.1
user@host> show security ipsec security-associations detail Virtual-system: root Local Gateway: 1.0.0.1, Remote Gateway: 1.1.1.1 Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Version: IKEv1 DF-bit: clear Direction: inbound, SPI: ac23df79, AUX-SPI: 0 , VPN Monitoring: Hard lifetime. Expires in 3186 seconds Lifesize Remaining: Unlimited Soft lifetime. Expires in 2578 seconds Mode. Tunnel, Type. dynamic, State. installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service. counter-based enabled, Replay window size. 64 Direction: outbound, SPI: cbc9281a, AUX-SPI: 0 , VPN Monitoring: Hard lifetime. Expires in 3186 seconds Lifesize Remaining: Unlimited Soft lifetime. Expires in 2578 seconds Mode. Tunnel, Type. dynamic, State. installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service. counter-based enabled, Replay window size. 64 -- Exhibit -
Click the Exhibit button.
The exhibit shows output from two show commands.
What are two conclusions about the VPN tunnel from the output? (Choose two.)
A. VPN monitoring is enabled.
B. There is a device performing NAT between the two VPN endpoints.
C. 3DES is the encryption protocol.
D. Traffic with the DF-bit set that exceeds the MTU will be dropped.
-
Question 126:
-- Exhibit -
user@host> show security ike security-associations 1.1.1.2 Index Remote Address State Initiator cookie Responder cookie Mode 8 1.1.1.2 UP 3a895f8a9f620198 9040753e66d700bb Main user@host> show security ipsec security-associations Total active tunnels: 0
user@host> show route inet.0: 7 destinations, 7 routes (6 active, 0 holddown, 1 hidden) + = Active Route, - = Last Active, * = Both 0.0.0.0/0 *[Static/5] 00:00:25 > to 2.2.2.1 via ge-0/0/0.0 2.2.2.0/24 *[Direct/0] 00:00:25 > via ge-0/0/0.0 2.2.2.2/32 *[Local/0] 00:00:25 Local via ge-0/0/0.0 10.1.1.0/30 *[Direct/0] 00:06:06 > via st0.0 10.1.1.1/32 *[Local/0] 00:06:06 Local via st0.0 10.12.1.0/24 *[Direct/0] 00:06:06 > via ge-0/0/1.0 10.12.1.1/32 *[Local/0] 00:06:06 Local via ge-0/0/1.0 10.128.64.0/24 *[Static/5] 00:00:25 > to 2.2.2.1 via ge-0/0/0.0
user@host> show security policies Default policy: deny-all From zone: trust, To zone: vpn Policy: permit-all, State: enabled, Index: 4, Scope Policy: 0, Sequence number: 1 Source addresses: any Destination addresses: any Applications: any Action: permit -- Exhibit -
Click the Exhibit button.
You have created an IPsec VPN on an SRX Series device. You believe the tunnel is configured correctly, but traffic from a host with the IP address of 10.12.1.10 cannot reach a remote device over the tunnel with an IP address of 10.128.64.132. The ge-0/0/1.0 interface is in the trust zone and the st0.0 interface is in the vpn zone. The output of four show commands is shown in the exhibit.
What is the configuration problem with the tunnel?
A. Only one IKE tunnel exists so there is no path for return IKE traffic. You need to allow IKE inbound on interface ge-0/0/0.0.
B. Because there are no IPsec security associations, the problem is in the IPsec proposal settings.
C. The static route created to reach the remote host is incorrect.
D. The VPN settings are correct, the traffic is being blocked by a security policy.
-
Question 127:
-- Exhibit -
security {
ike {
policy IKE-STANDARD {
mode aggressive;
proposal-set standard;
pre-shared-key ascii-text "XXXXXX";
}
gateway GW-HUB {
ike-policy IKE-STANDARD;
dynamic hostname site1.company.com;
external-interface ge-0/0/0.0;
}
}
ipsec {
policy IPSEC-STANDARD {
proposal-set standard;
}
vpn VPN-HUB {
bind-interface st0.0;
ike {
gateway GW-HUB;
ipsec-policy IPSEC-STANDARD;
}
}
}
zones {
security-zone untrust {
host-inbound-traffic {
system-services {
ping;
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone trust {
system-services {
ping;
}
interfaces {
ge-0/0/1.0;
}
}
}
}
-- Exhibit -
Click the Exhibit button.
You are implementing a new route-based IPsec VPN on an SRX Series device and the tunnel will not establish.
What needs to be modified in the configuration shown in the exhibit?
A. Change the bind-interface from st0.0 to ge-0/0/0.0.
B. Add st0.0 to a security zone.
C. Add esp under host-inbound-traffic on zone untrust.
D. Add ike under host-inbound-traffic on zone trust.
-
Question 128:
-- Exhibit -- Exhibit -Click the Exhibit button. Referring to the exhibit, you are setting up the hub in a hub-and-spoke IPsec VPN. You have verified that all configured parameters are correct at all sites, but your IPsec VPN is not establishing to both sites.
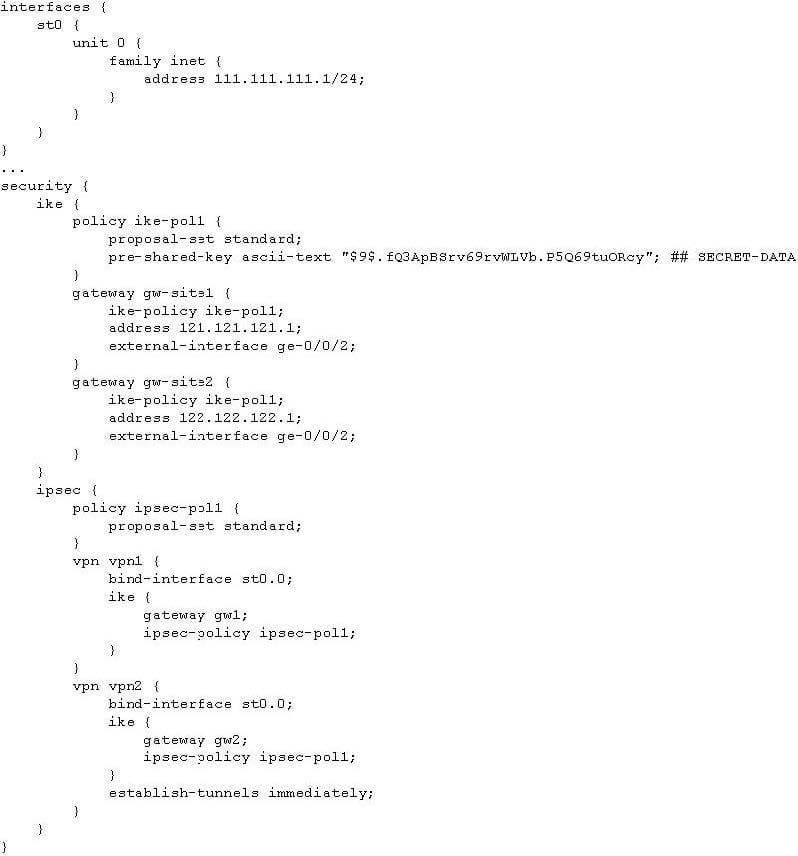
Which configuration parameter is missing at the hub to complete the configuration?
A. A different external-interface is needed for vpn1.
B. A different st0 logical interface is needed for vpn2.
C. Establish-tunnels immediately must be configured for vpn1.
D. Multipoint needs to be configured under the st0.0 interface.
-
Question 129:
-- Exhibit
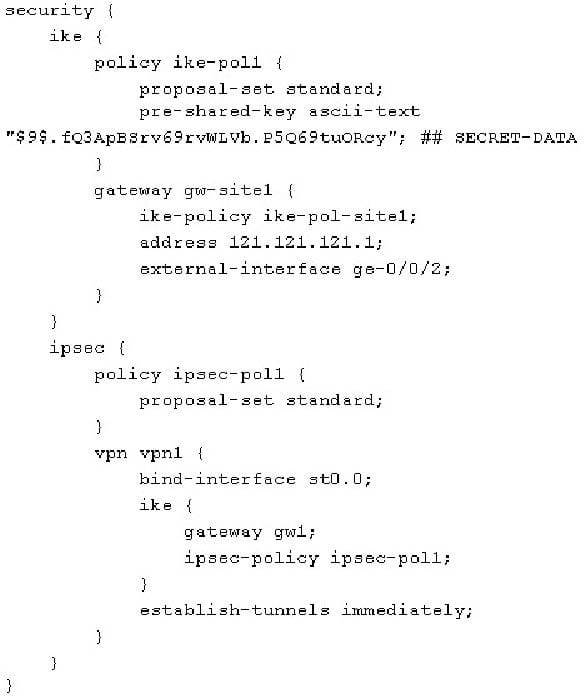
-- Exhibit -Click the Exhibit button.
Referring to the exhibit, which statement is correct about the IPsec configuration?
A. Policy-based implementation is used.
B. Dynamic VPN implementation is used.
C. Route-based implementation is used.
D. Hub-and-spoke implementation is used.
-
Question 130:
-- Exhibit
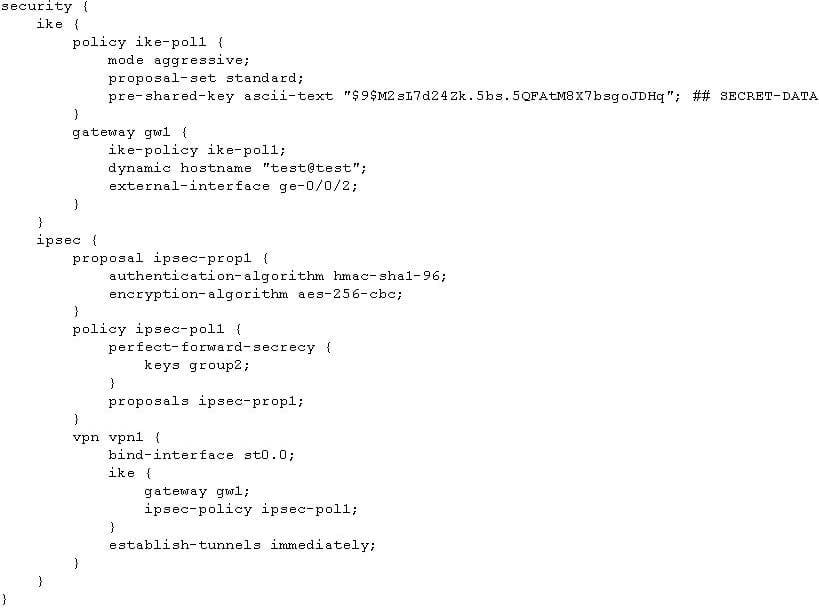
-- Exhibit -Click the Exhibit button.
Referring to the exhibit, which statement is correct about the IPsec configuration?
A. The IPsec tunnel endpoint does not have a static IP address.
B. IKE Phase 2 is established immediately from the hub.
C. Protocol AH is used with IKE Phase 2.
D. IKE Phase 2 uses a standard proposal.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-332 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.