Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jun 29, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 71:
SIMULATION
Part1-AppServ3
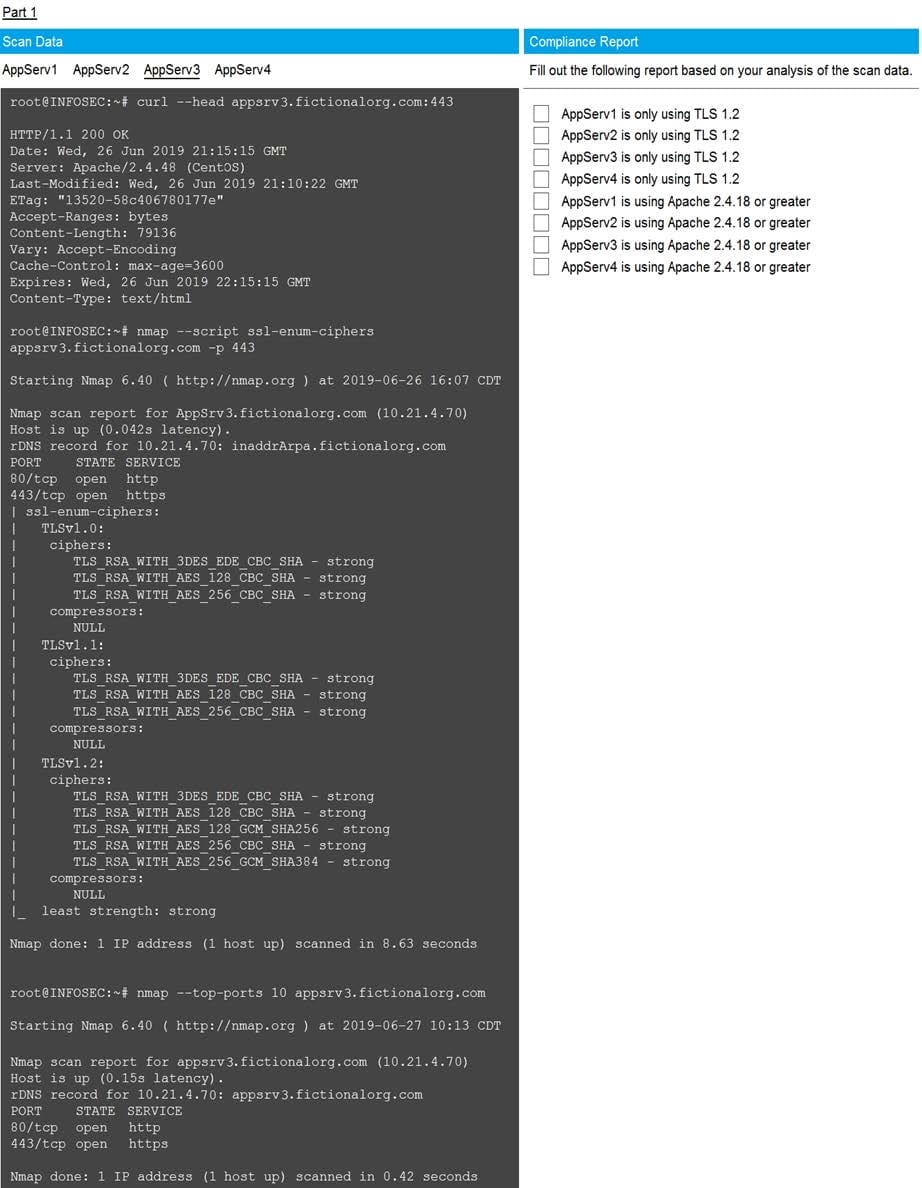
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not. The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
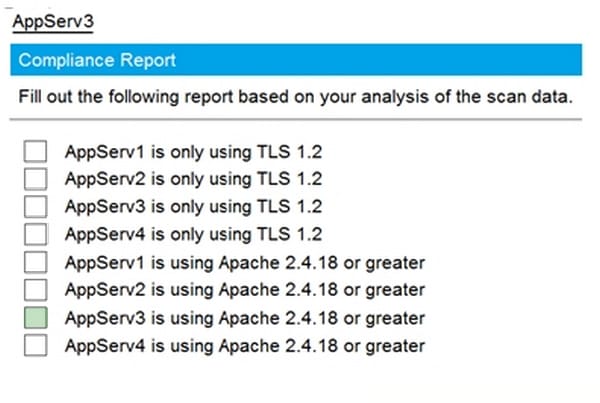
Hot Area:
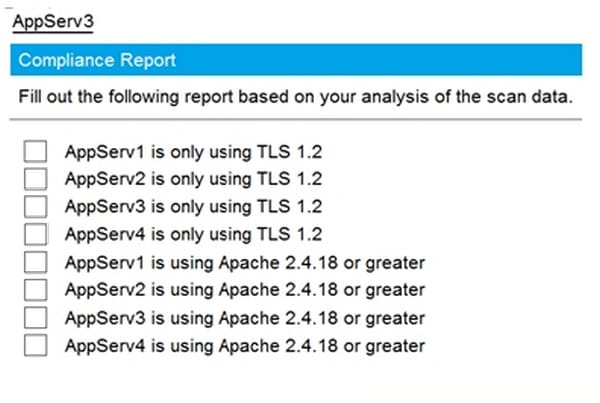
-
Question 72:
SIMULATION
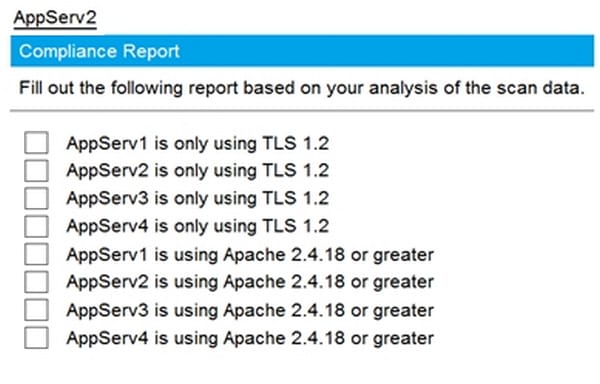
Part1-AppServ2
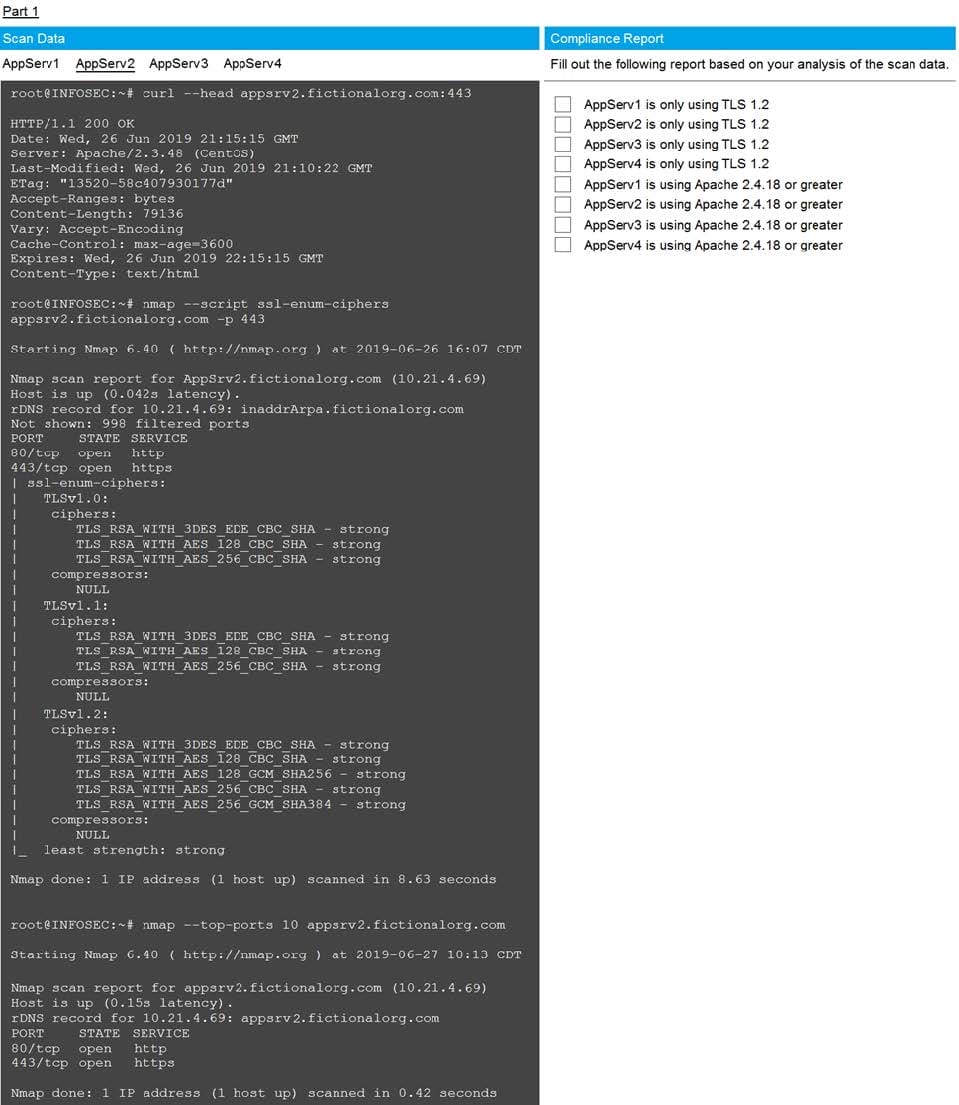
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
2
Hot Area:
-
Question 73:
To prioritize the morning's work, an analyst is reviewing security alerts that have not yet been investigated. Which of the following assets should be investigated FIRST?
A. The workstation of a developer who is installing software on a web server.
B. A new test web server that is in the process of initial installation.
C. An accounting supervisor's laptop that is connected to the VPN
D. The laptop of the vice president that is on the corporate LAN
-
Question 74:
The development team has created a new employee application to allow the 35,000 staff members to communicate via video, chat rooms, and microblogs from anywhere in the world. The application was tested by a small user group, and the code reviews were completed. Which of the following is the best NEXT step the development team should take?
A. Run the application through a web-application vulnerability scanner.
B. Complete an additional round of code reviews to maintain project integrity.
C. Stress test the application to ensure its ability to support the employee population.
D. Isolate the application servers on premises to protect the communication methods.
-
Question 75:
Which of the following BEST explains hardware root of trust?
A. It uses the processor security extensions to protect the OS from malicious software installation.
B. It prevents side-channel attacks that can take advantage of speculative execution vulnerabilities.
C. It ensures the authenticity of firmware and software during the boot process until the OS is loaded.
D. It has been implemented as a mitigation to the Spectre and Meltdown hardware vulnerabilities.
-
Question 76:
A user reports a malware alert to the help desk. A technician verifies the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access. The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes. Which of the following should the security analyst do NEXT?
A. Document the procedures and walk through the incident training guide.
B. Reverse engineer the malware to determine its purpose and risk to the organization.
C. Sanitize the workstation and verify countermeasures are restored.
D. Isolate the workstation and issue a new computer to the user.
-
Question 77:
The Chief Information Officer (CIO) of a large cloud software vendor reports that many employees are falling victim to phishing emails because they appear to come from other employees. Which of the following would BEST prevent this issue?
A. Include digital signatures on messages originating within the company.
B. Require users to authenticate to the SMTP server.
C. Implement DKIM to perform authentication that will prevent this issue.
D. Set up an email analysis solution that looks for known malicious links within the email.
-
Question 78:
A security analyst is concerned that a third-party application may have access to user passwords during authentication. Which of the following protocols should the application use to alleviate the analyst's concern?
A. LDAPS
B. MFA
C. SAML
D. SHA-1
-
Question 79:
A company's Chief Information Security Officer (CISO) published an Internet usage policy that prohibits employees from accessing unauthorized websites. The IT department whitelisted websites used for business needs. The CISO wants the security analyst to recommend a solution that would improve security and support employee morale. Which of the following security recommendations would allow employees to browse non-business-related websites?
A. Implement a virtual machine alternative.
B. Develop a new secured browser.
C. Configure a personal business VLAN.
D. Install kiosks throughout the building.
-
Question 80:
Following a recent security breach, a company decides to investigate account usage to ensure privileged accounts are only being utilized during typical business hours. During the investigation, a security analyst determines an account was consistently utilized in the middle of the night.
Which of the following actions should the analyst take NEXT?
A. Disable the privileged account.
B. Initiate the incident response plan.
C. Report the discrepancy to human resources.
D. Review the activity with the user.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.