Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jun 29, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 61:
In response to a potentially malicious email that was sent to the Chief Financial Officer (CFO), an analyst reviews the logs and identifies a questionable attachment using a hash comparison. The logs also indicate the attachment was already opened. Which of the following should the analyst do NEXT?
A. Create a sinkhole to block the originating server.
B. Utilize the EDR platform to isolate the CFO's machine.
C. Perform malware analysis on the attachment.
D. Reimage the CFO's laptop.
-
Question 62:
A company's security administrator needs to automate several security processes related to testing for the existence of changes within the environment. Conditionally, other processes will need to be created based on input from prior processes. Which of the following is the BEST method for accomplishing this task?
A. Machine learning and process monitoring
B. Continuous integration and configuration management
C. API integration and data enrichment
D. Workflow orchestration and scripting
-
Question 63:
A vulnerability scanner has identified an out-of-support database software version running on a server. The software update will take six to nine months to complete. The management team has agreed to a one-year extended support contract with the software vendor. Which of the following BEST describes the risk treatment in this scenario?
A. The extended support mitigates any risk associated with the software.
B. The extended support contract changes this vulnerability finding to a false positive.
C. The company is transferring the risk for the vulnerability to the software vendor.
D. The company is accepting the inherent risk of the vulnerability.
-
Question 64:
A remote code execution vulnerability was discovered in the RDP. An organization currently uses RDP for remote access to a portion of its VDI environment. The analyst verified network-level authentication is enabled. Which of the following is the BEST remediation for this vulnerability?
A. Verify the threat intelligence feed is updated with the latest solutions.
B. Verify the system logs do not contain indicator of compromise.
C. Verify the latest endpoint-protection signature is in place.
D. Verify the corresponding patch for the vulnerability is installed.
-
Question 65:
A security analyst is handling an incident in which ransomware has encrypted the disks of several company workstations. Which of the following would work BEST to prevent this type of incident in the future?
A. Implement a UTM instead of a stateful firewall and enable gateway antivirus.
B. Back up the workstations to facilitate recovery and create a gold image.
C. Establish a ransomware awareness program and implement secure and verifiable backups.
D. Virtualize all the endpoints with daily snapshots of the virtual machines.
-
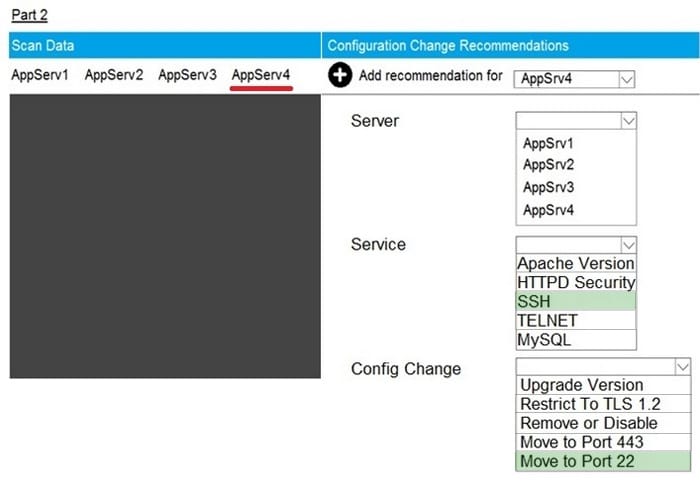
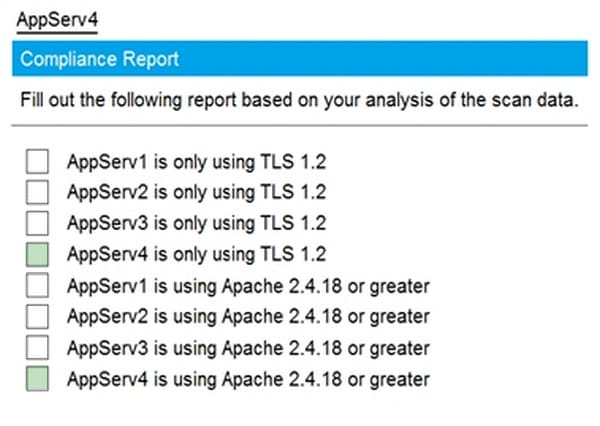
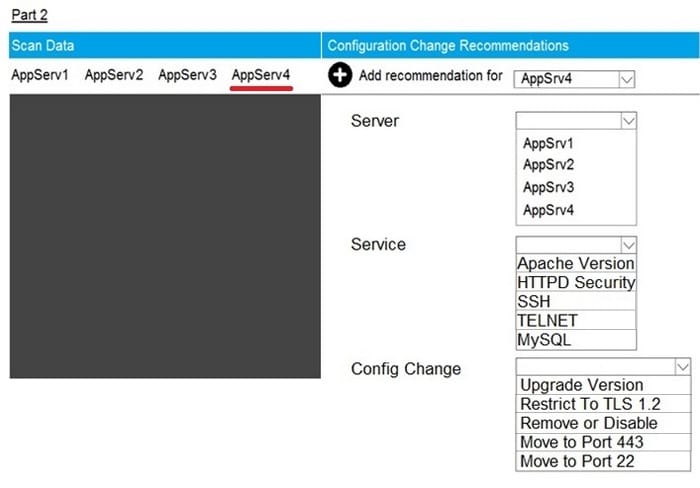
Question 66:
SIMULATION
Part2: AppServ4
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not. The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server. The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
Hot Area:
-
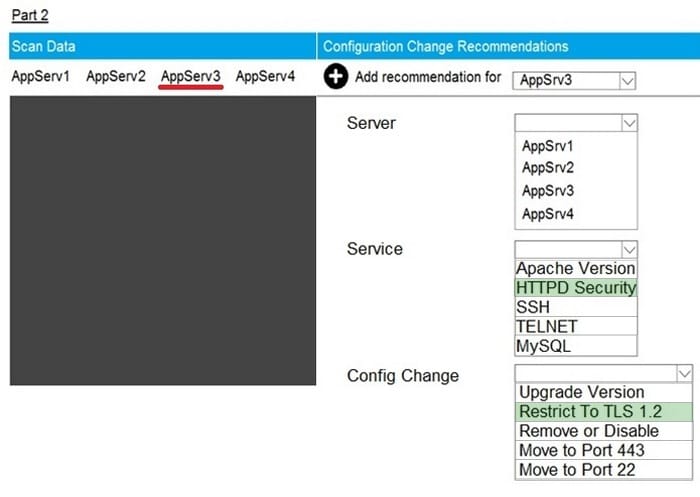
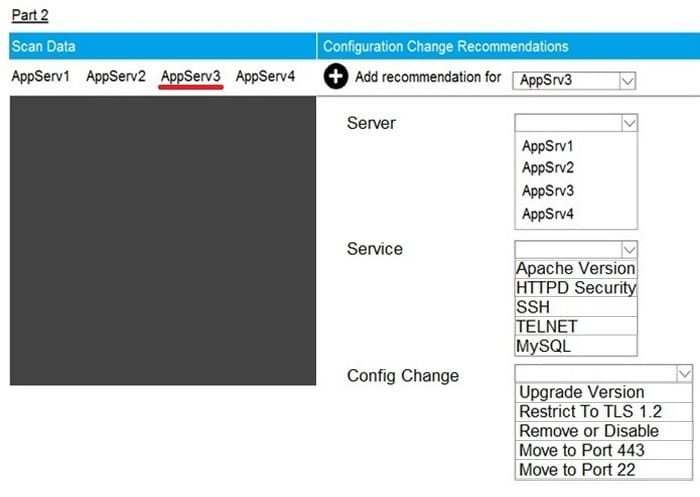
Question 67:
SIMULATION
Part2: AppServ3
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not. The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server. The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
Hot Area:
-
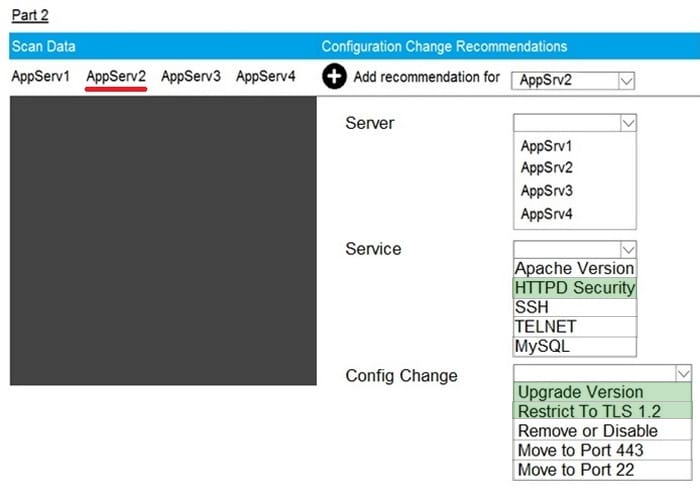
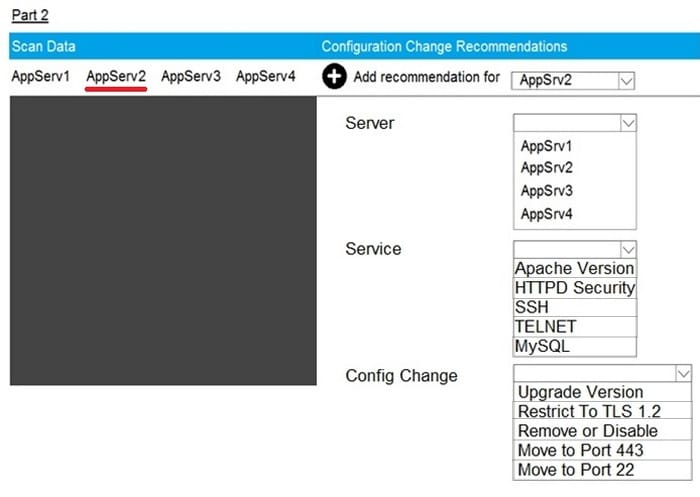
Question 68:
SIMULATION
Part2: AppServ2
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not. The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server. The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
Hot Area:
-
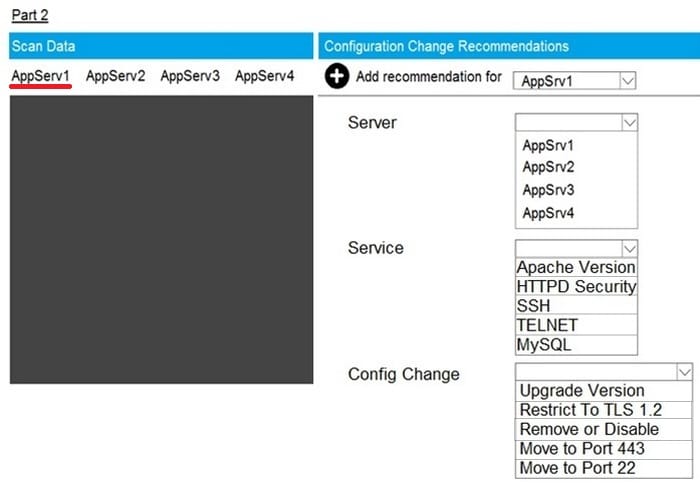
Question 69:
SIMULATION
Part2: AppServ1
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server. The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
Hot Area:
-
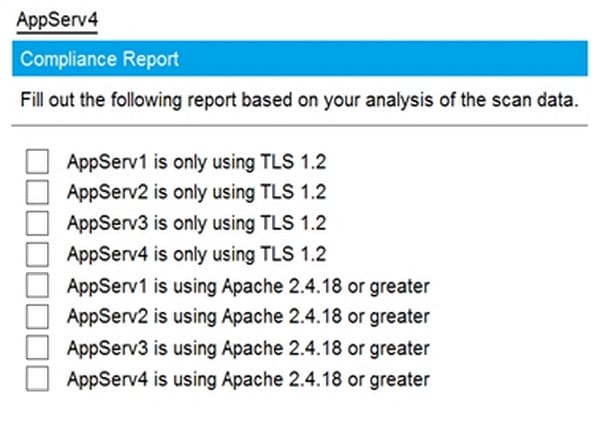
Question 70:
SIMULATION
Part1-AppServ4
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not. The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
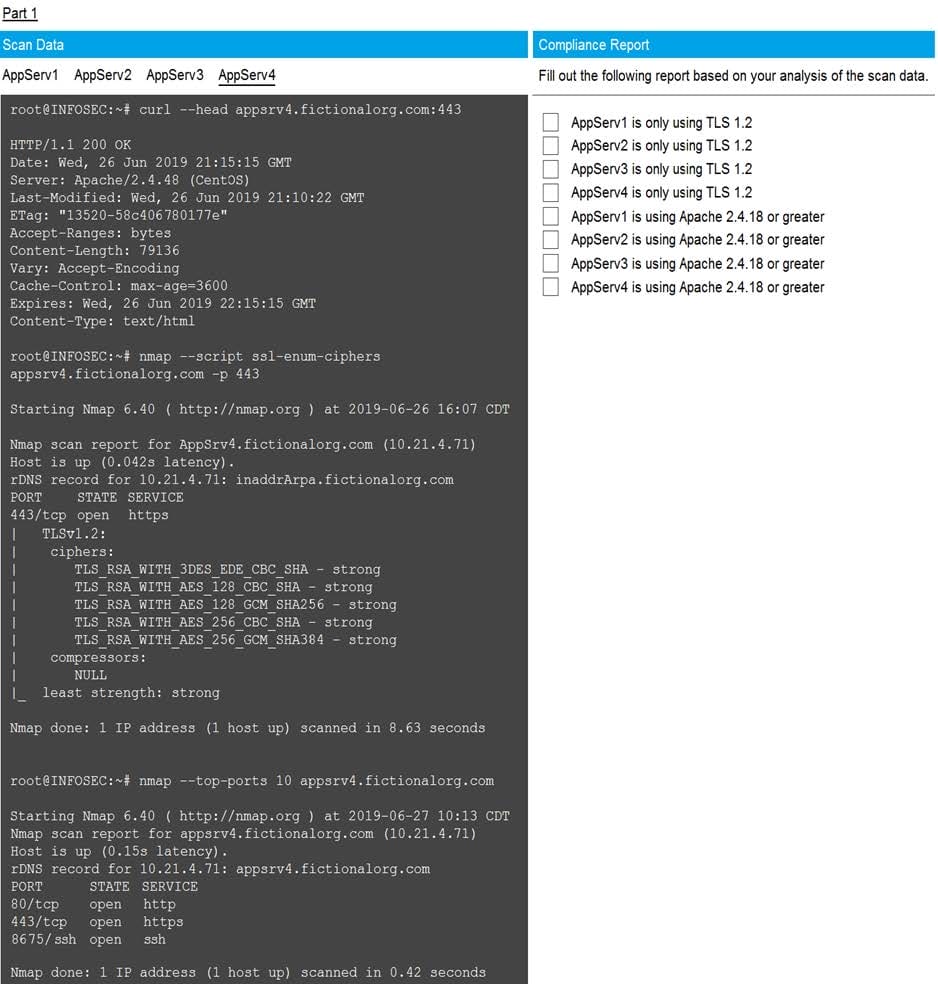
Hot Area:
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.