Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jun 29, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 1031:
A small electronics company decides to use a contractor to assist with the development of a new FPGA- based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
A. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
B. Moving the FPGAs between development sites will lessen the time that is available for security testing.
C. Development phases occurring at multiple sites may produce change management issues.
D. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
-
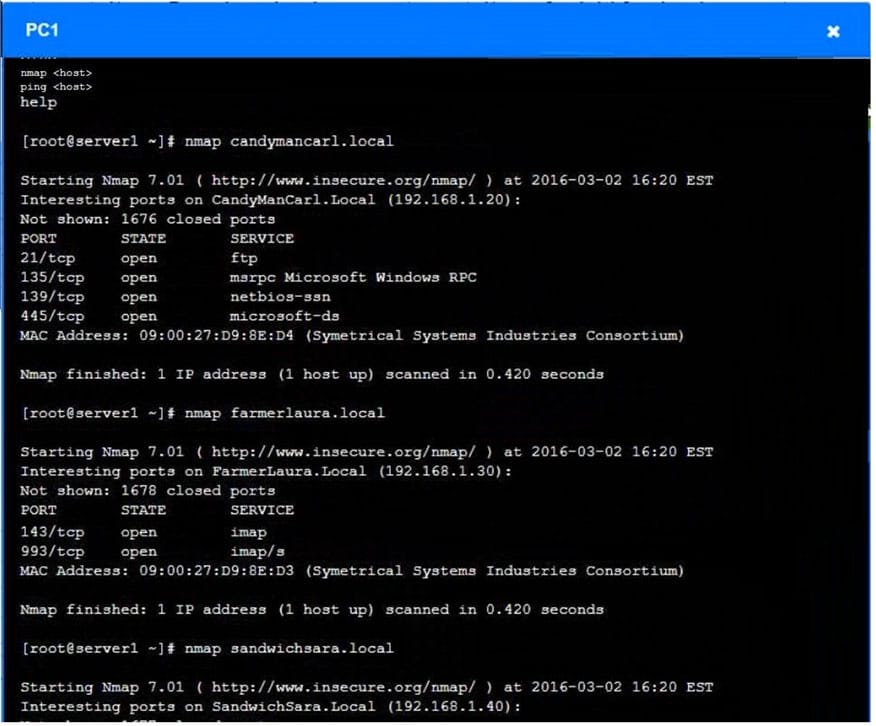
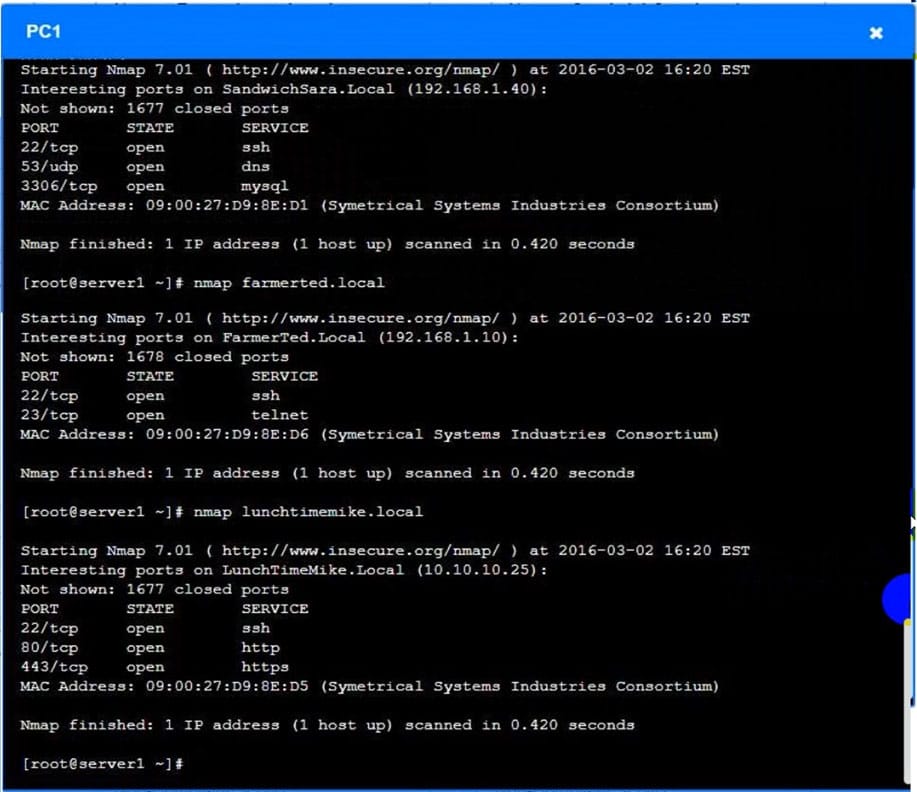
Question 1032:
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following:

The analyst runs the following command next:
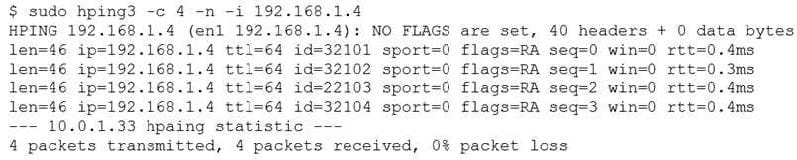
Which of the following would explain the difference in results?
A. ICMP is being blocked by a firewall.
B. The routing tables for ping and hping3 were different.
C. The original ping command needed root permission to execute.
D. hping3 is returning a false positive.
-
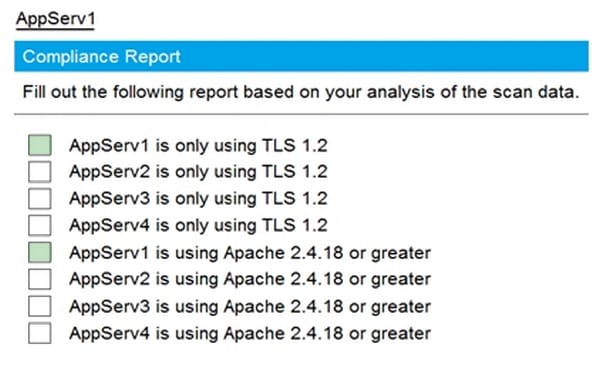
Question 1033:
SIMULATION
Part1-AppServ1
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not. The company's hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
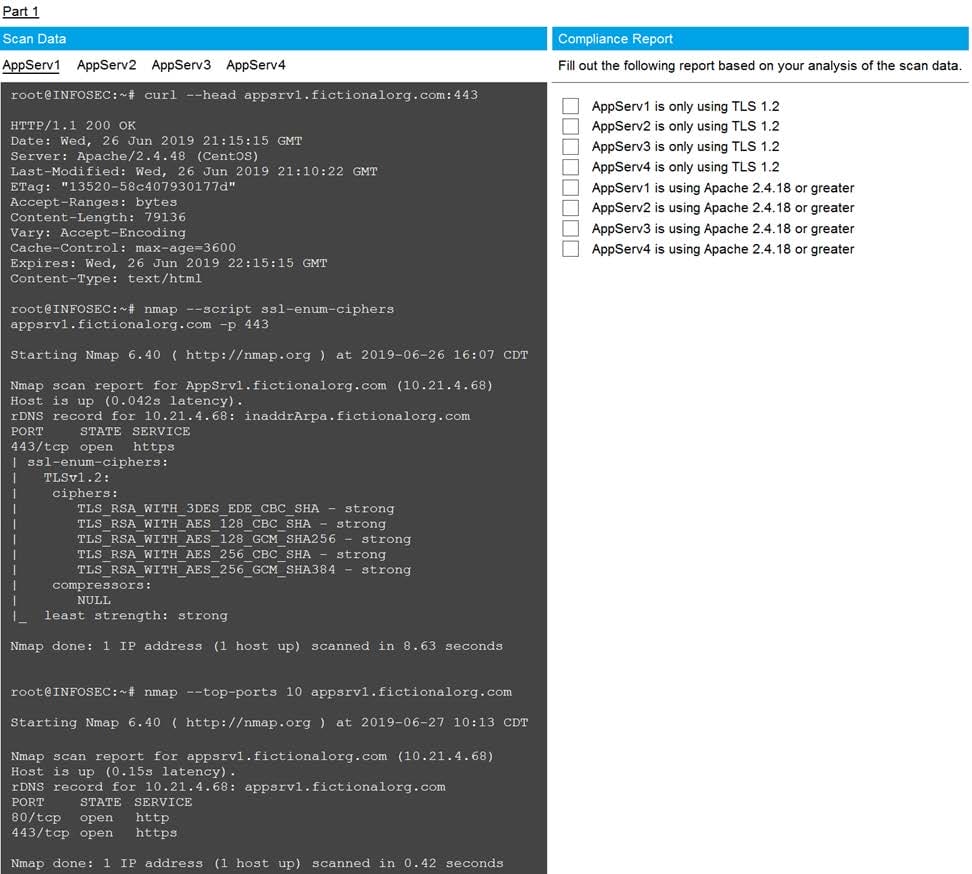
Hot Area:
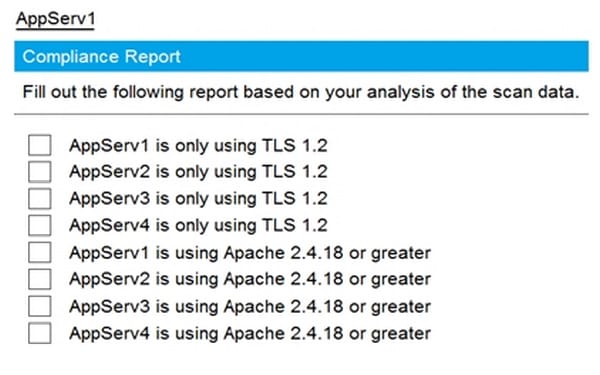
-
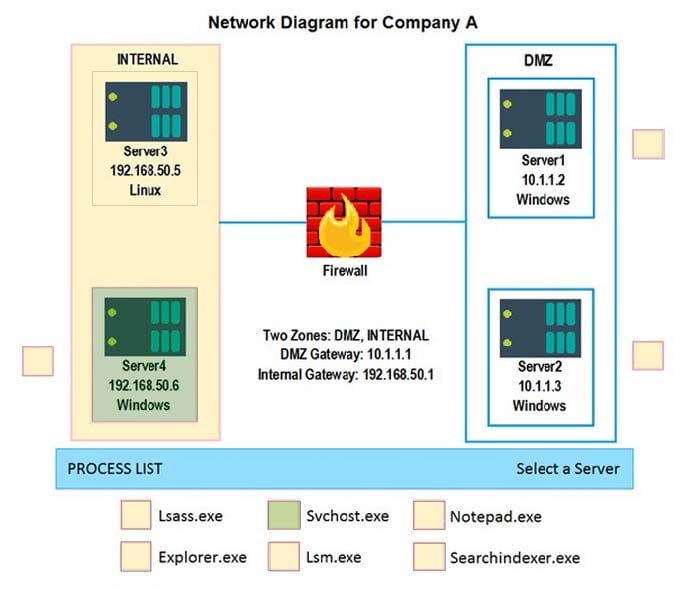
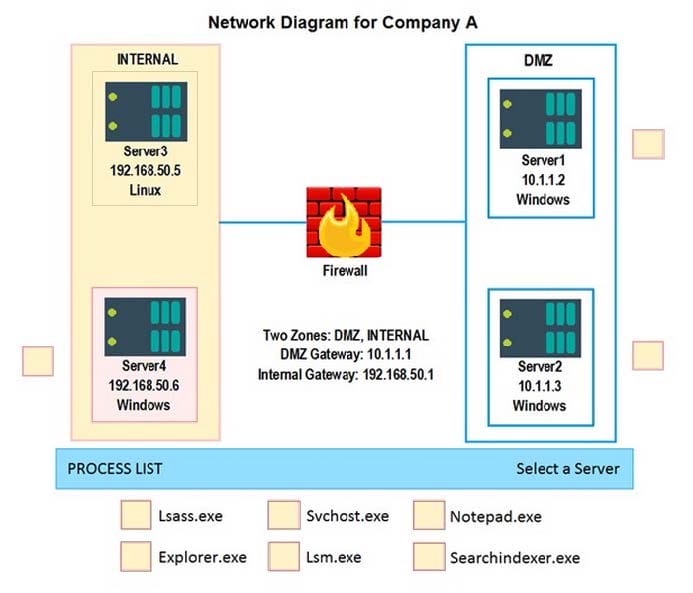
Question 1034:
SIMULATION
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
INSTRUCTIONS
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select
the Next button to continue.
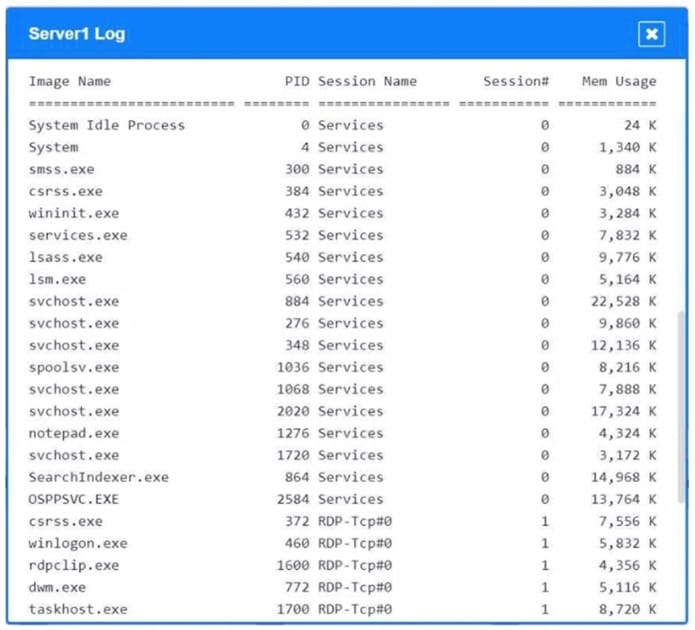
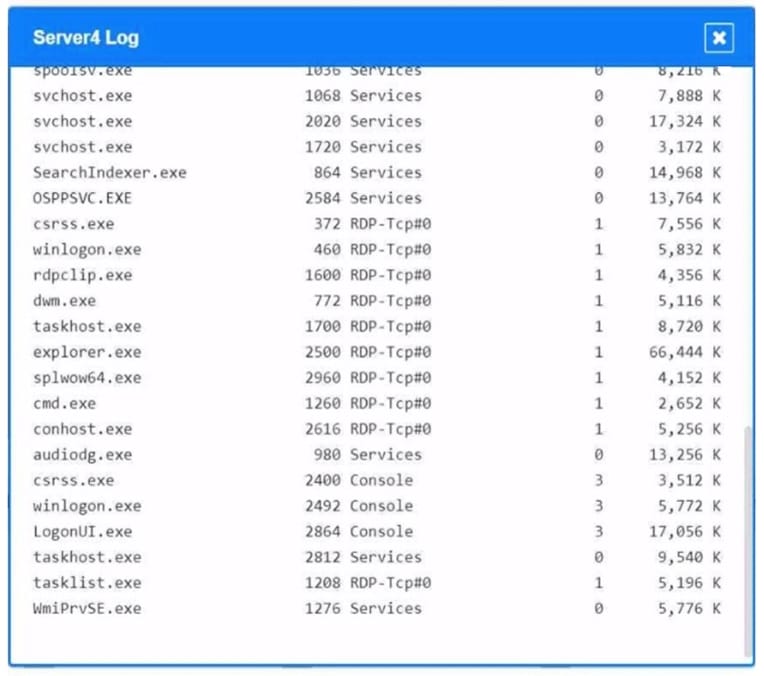
Hot Area:
-
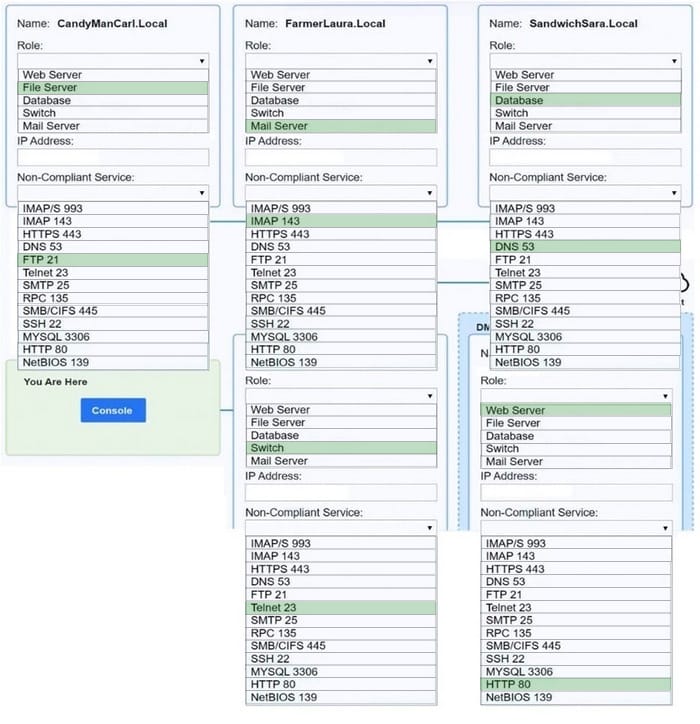
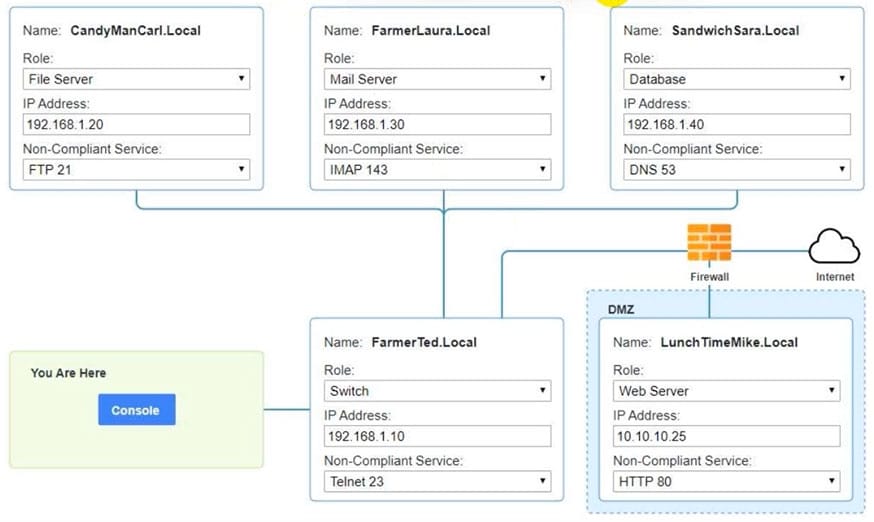
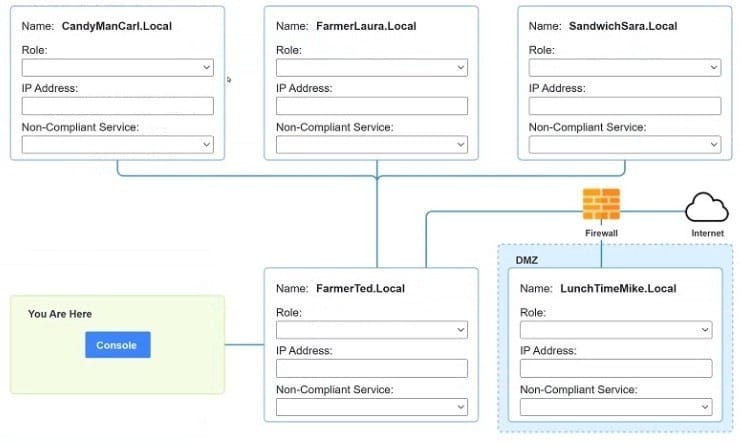
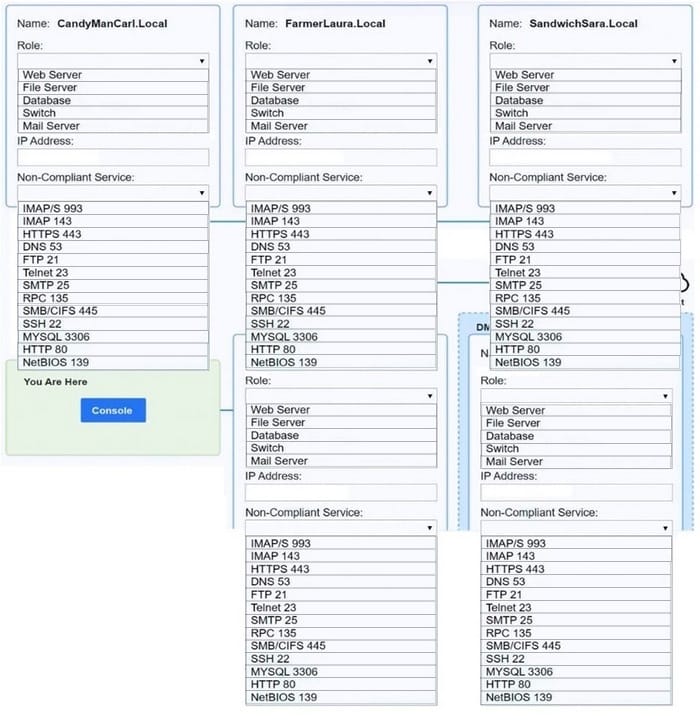
Question 1035:
SIMULATION
You are a penetration tester who is reviewing the system hardening guidelines for a company. Hardening guidelines indicate the following:
1.
There must be one primary server or service per device.
2.
Only default port should be used
3.
Non- secure protocols should be disabled.
The corporate internet presence should be placed in a protected subnet Instructions :
Using the available tools, discover devices on the corporate network and the services running on these devices. You must determine ip address of each device The primary server or service each device The protocols that should be disabled based on the hardening guidelines
Hot Area:
-
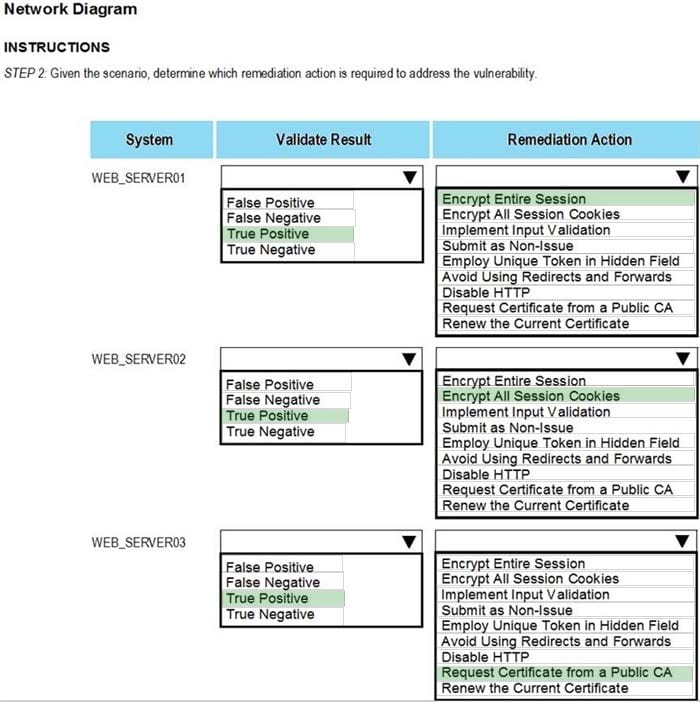
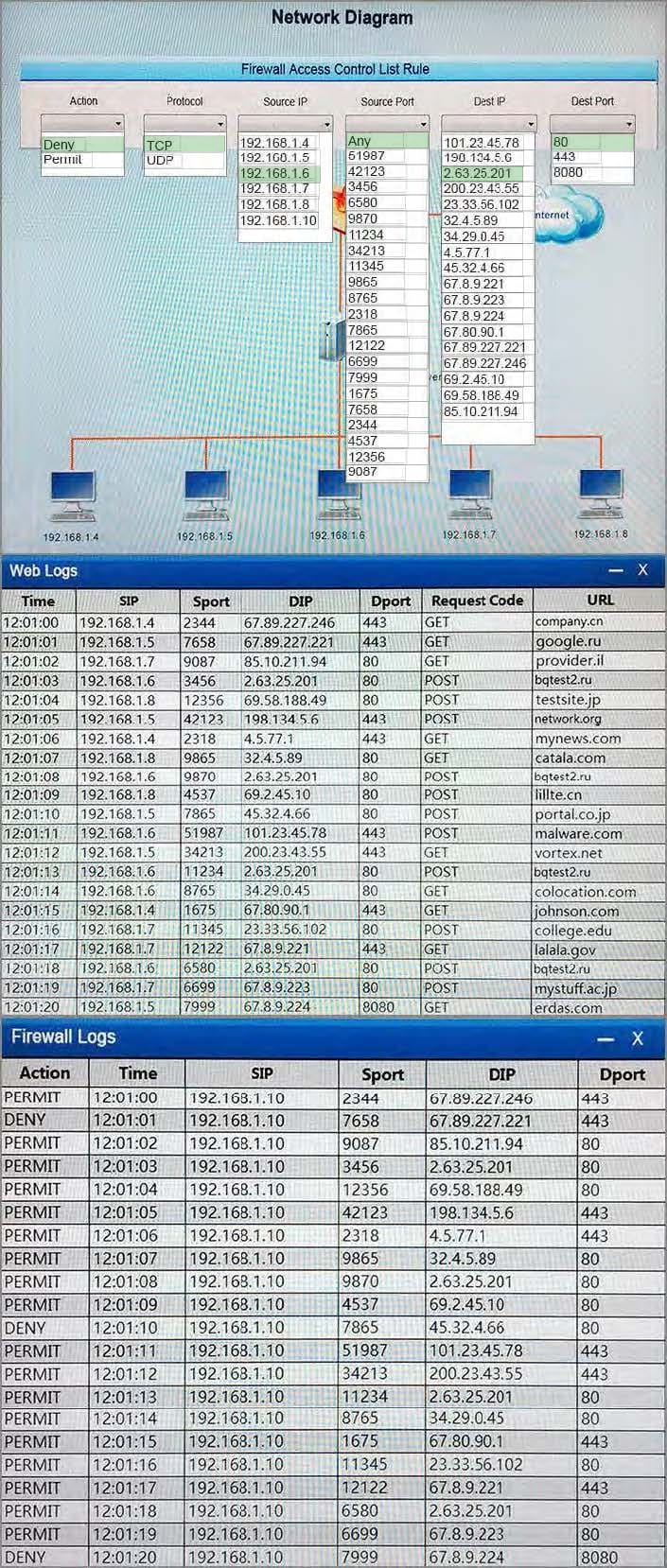
Question 1036:
HOTSPOT
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.
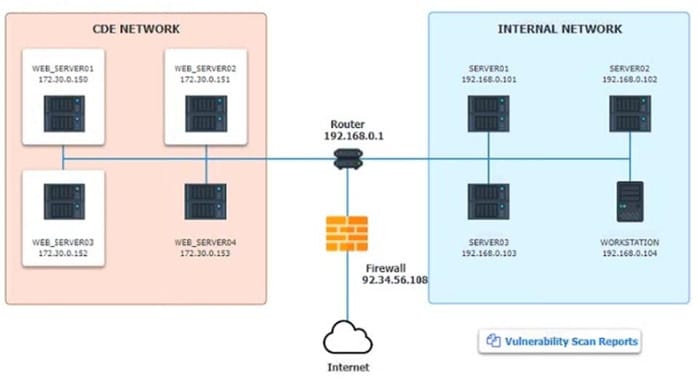
STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.
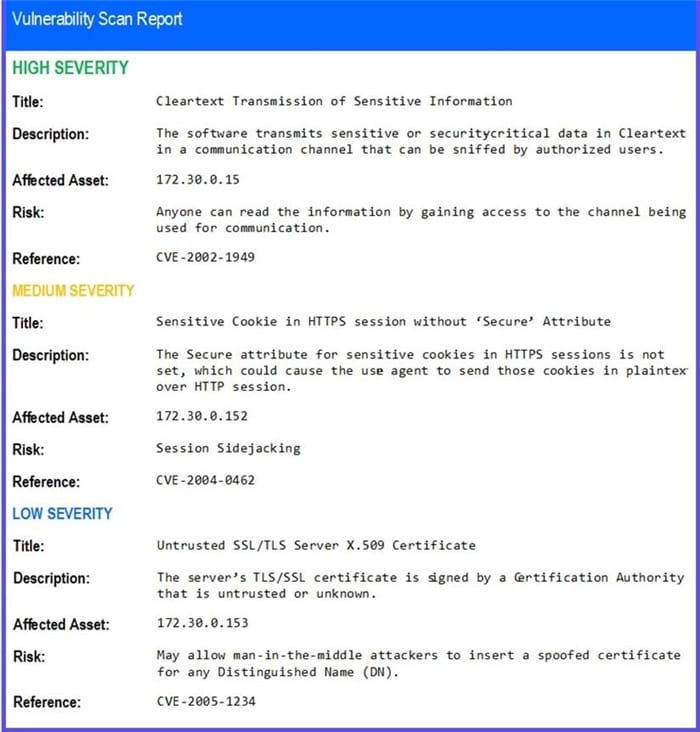
Hot Area:
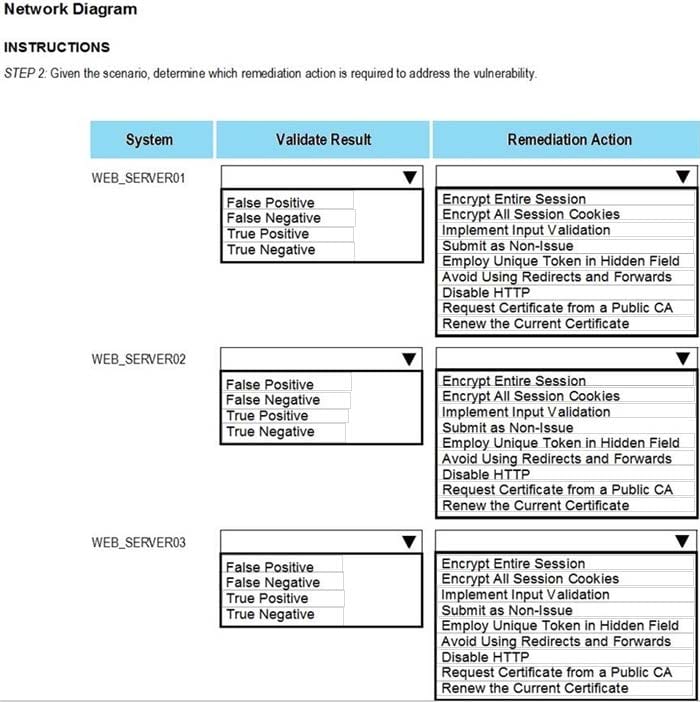
-
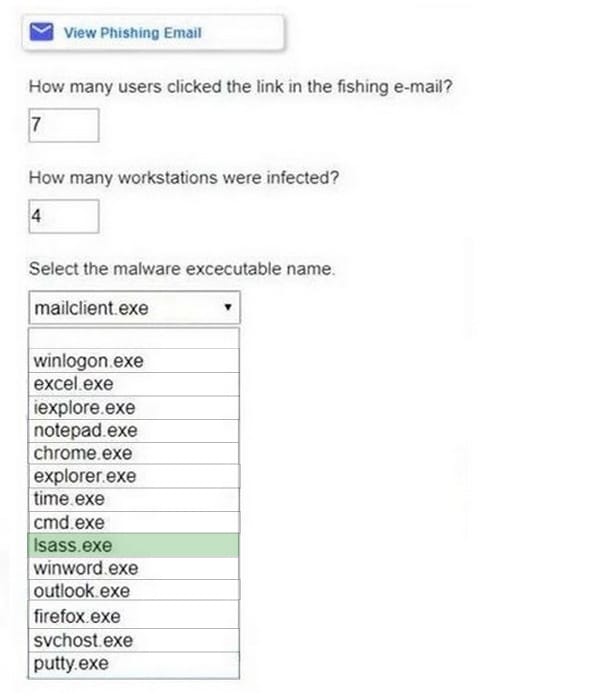
Question 1037:
HOTSPOT
Approximately 100 employees at your company have received a phishing email. As a security analyst you have been tasked with handling this situation.
INSTRUCTIONS
Review the information provided and determine the following:
1.
How many employees clicked on the link in the phishing email?
2.
On how many workstations was the malware installed?
3.
What is the executable file name or the malware?
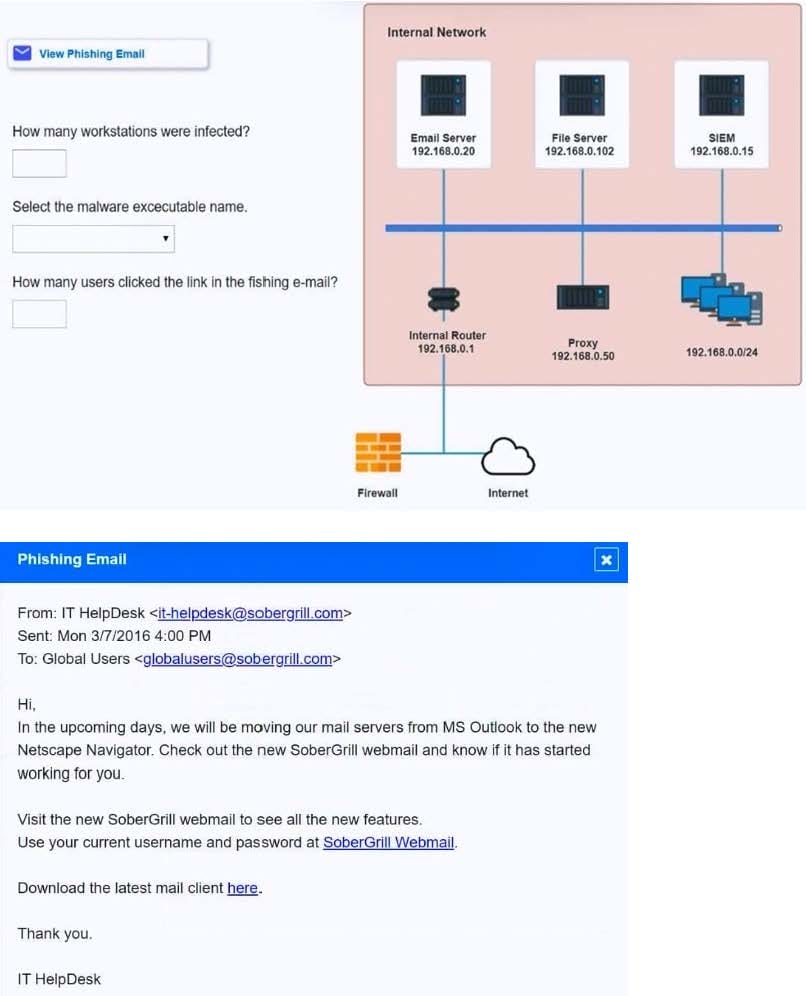
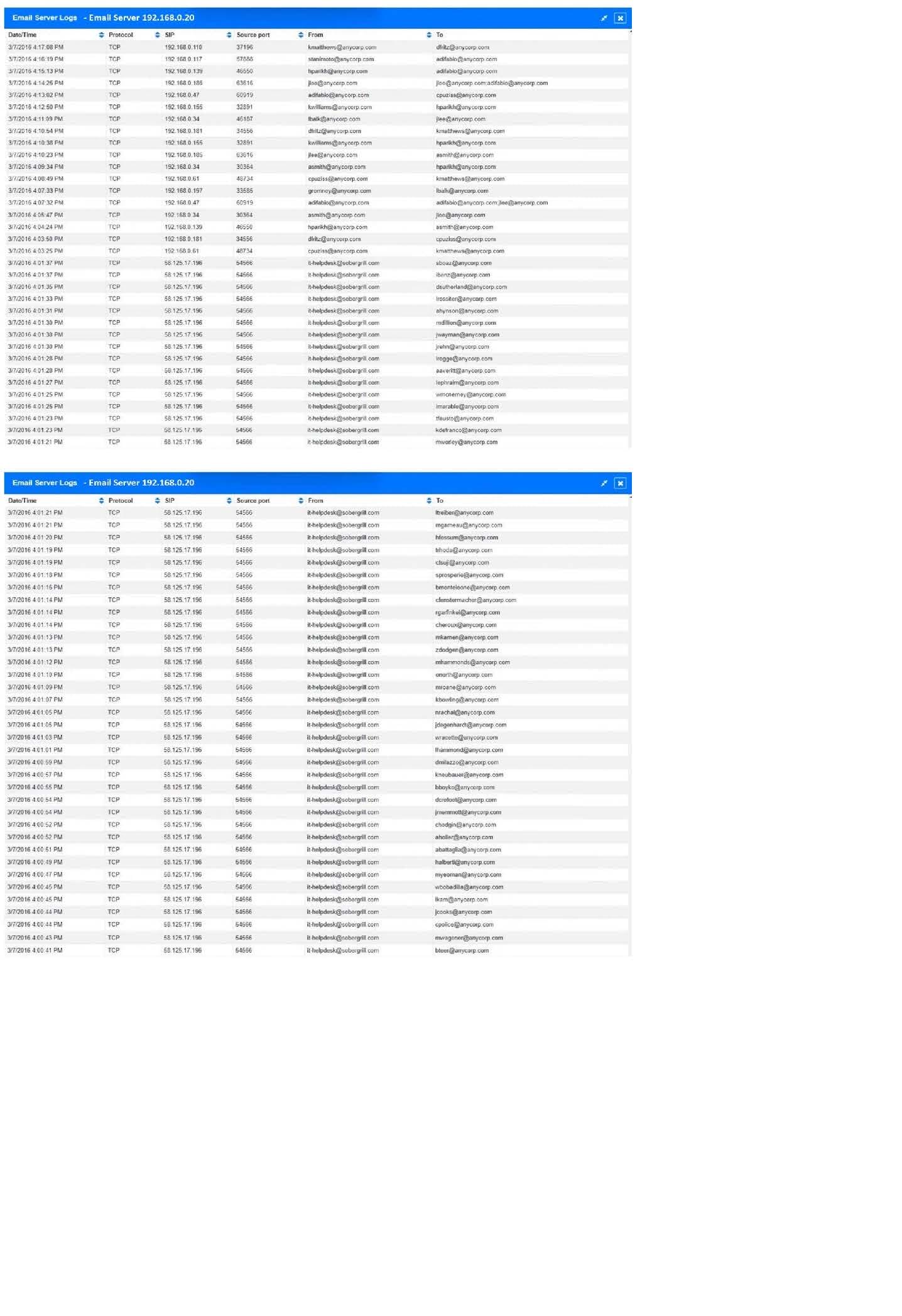
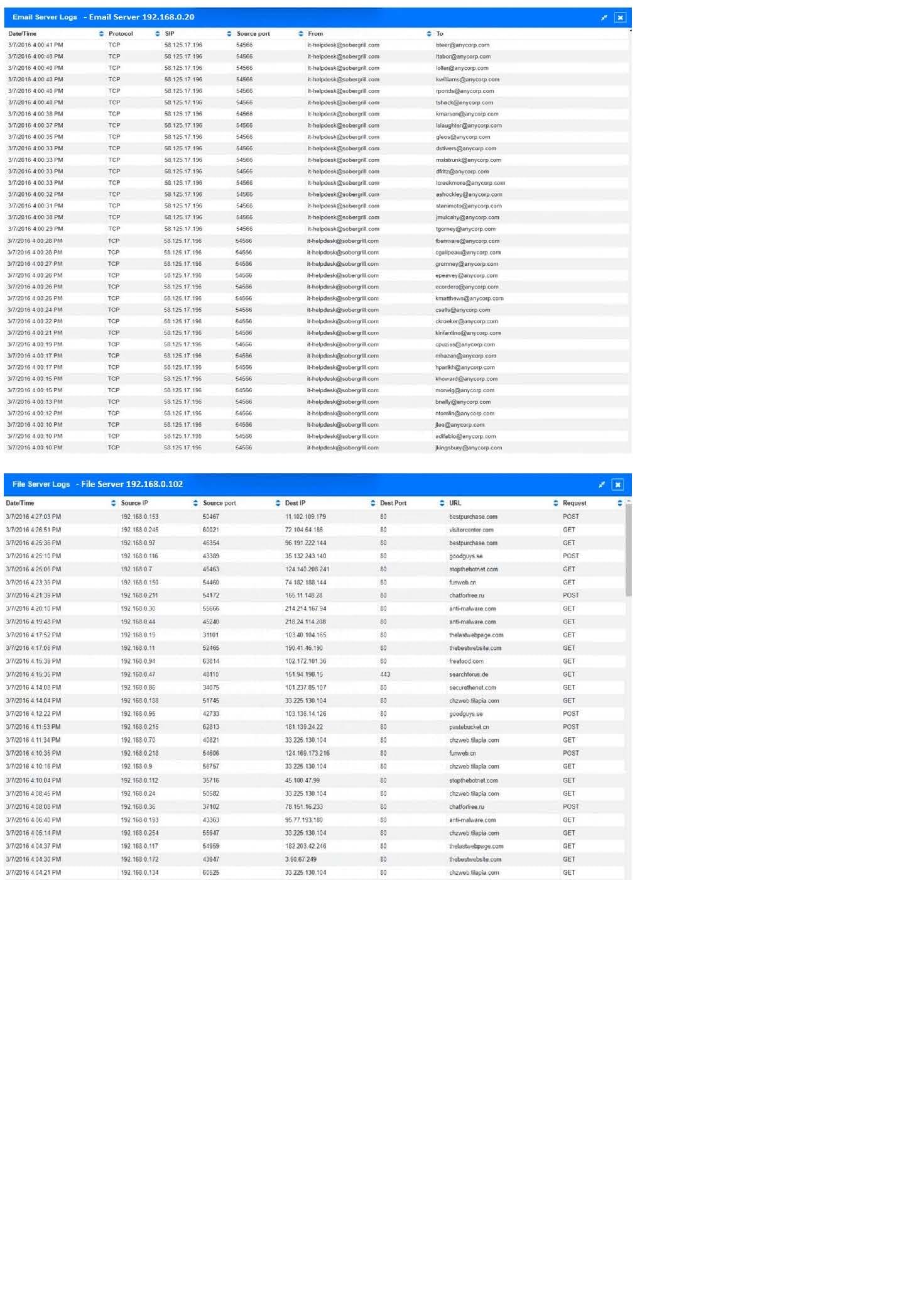
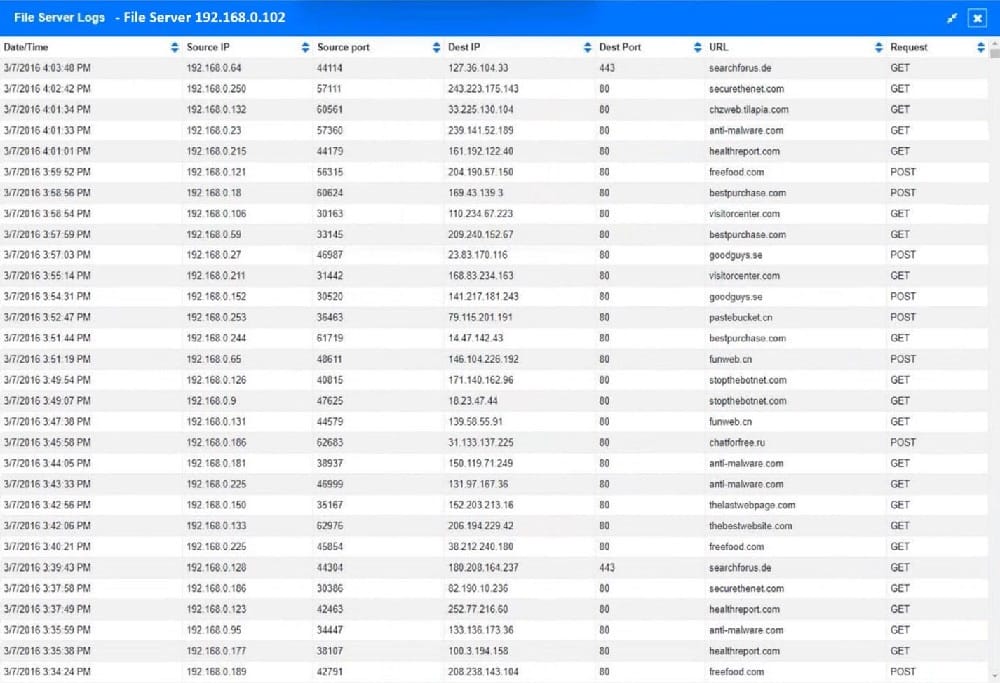
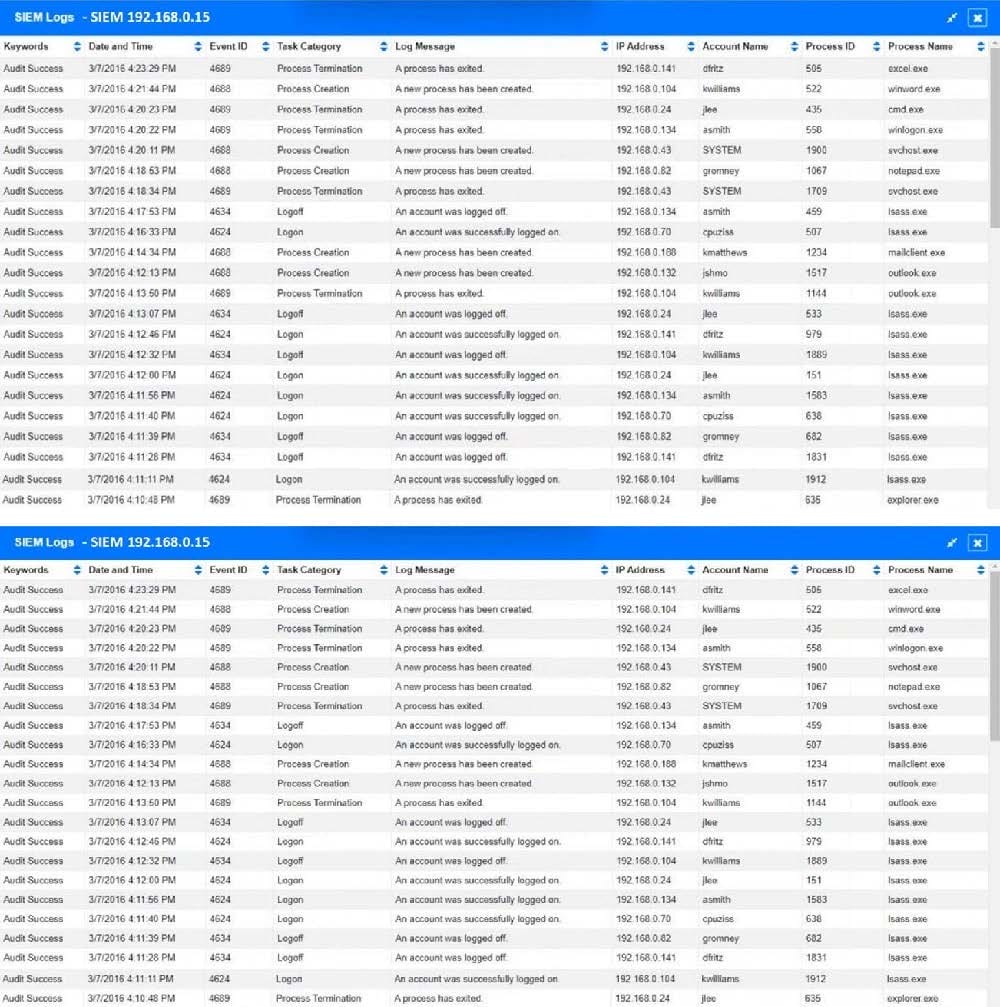
Hot Area:
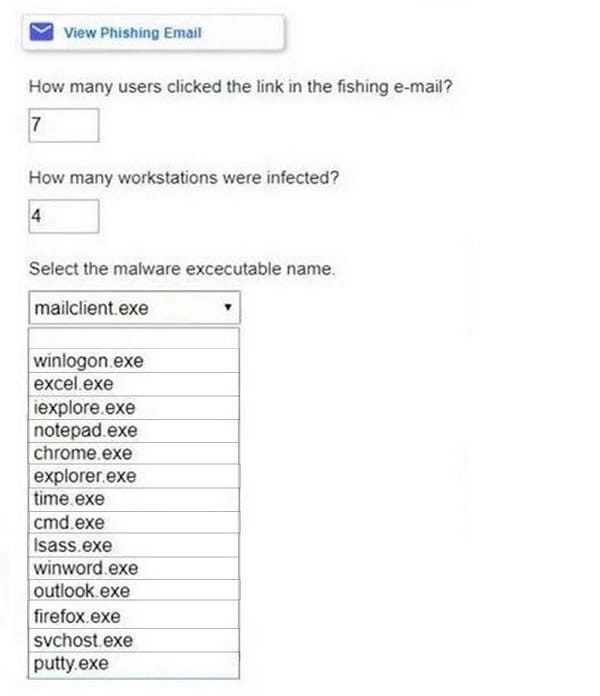
-
Question 1038:
HOTSPOT
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to
neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the
Next button to continue.
Hot Area:
-
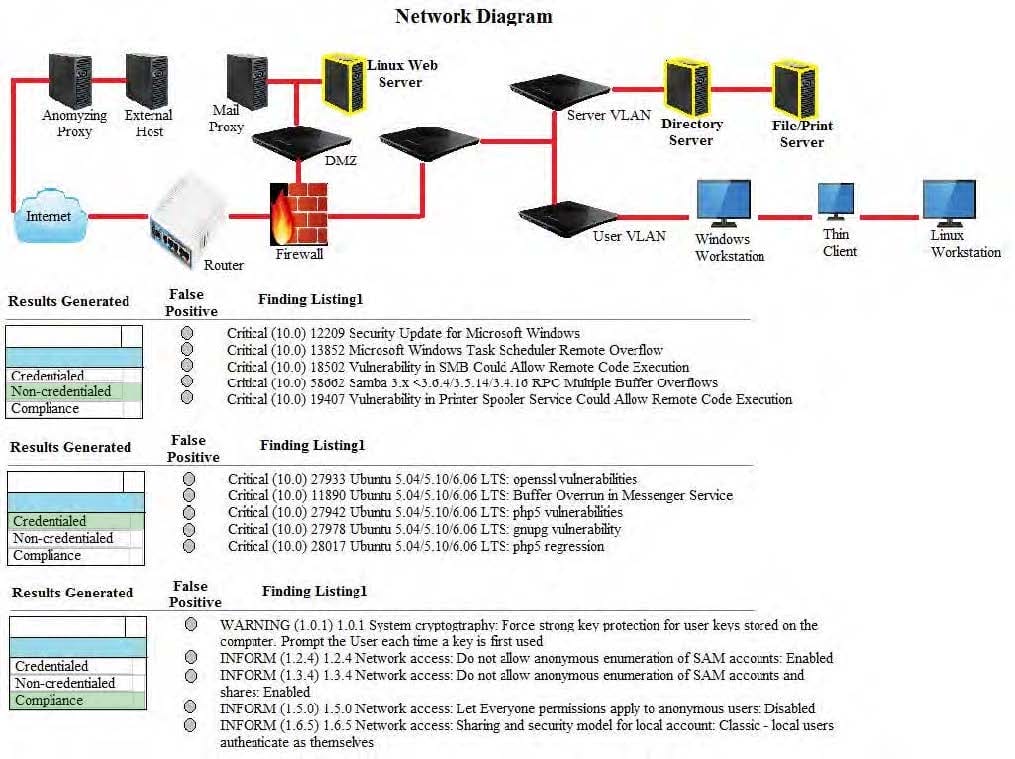
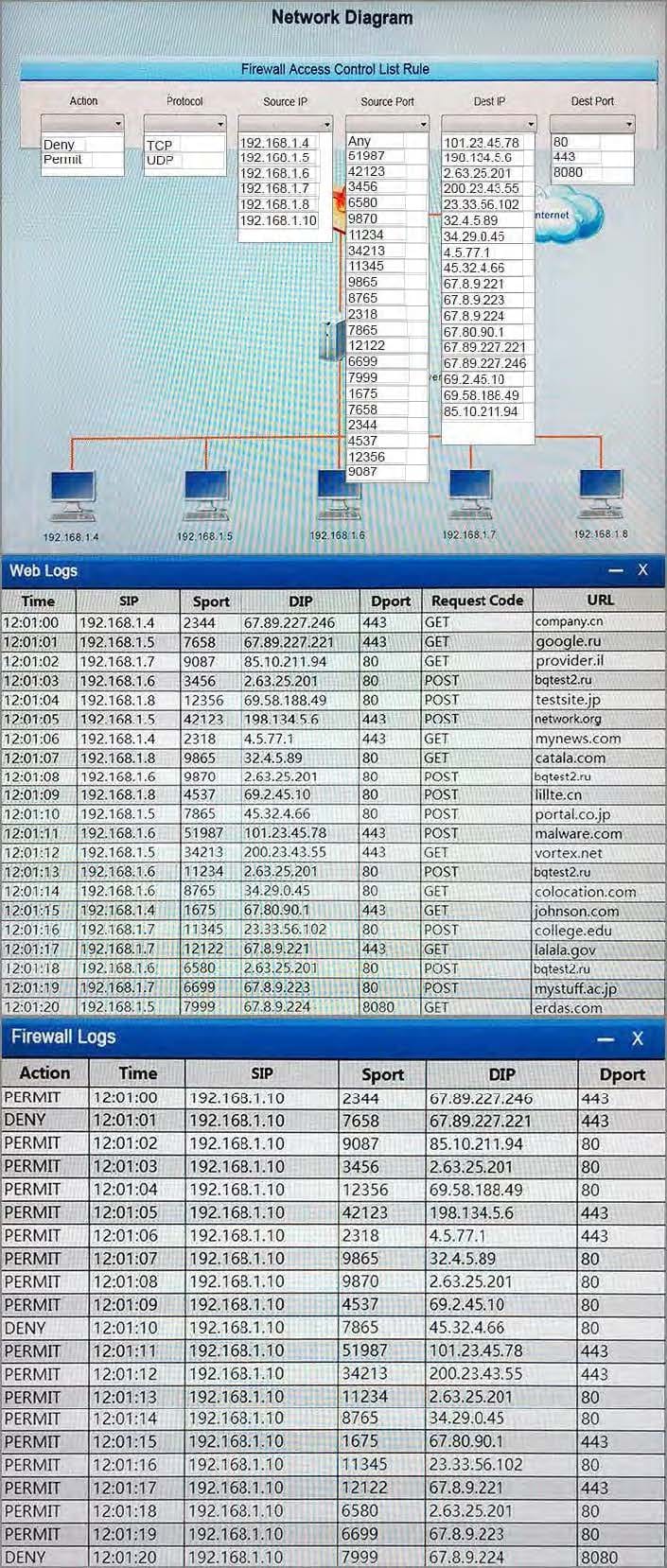
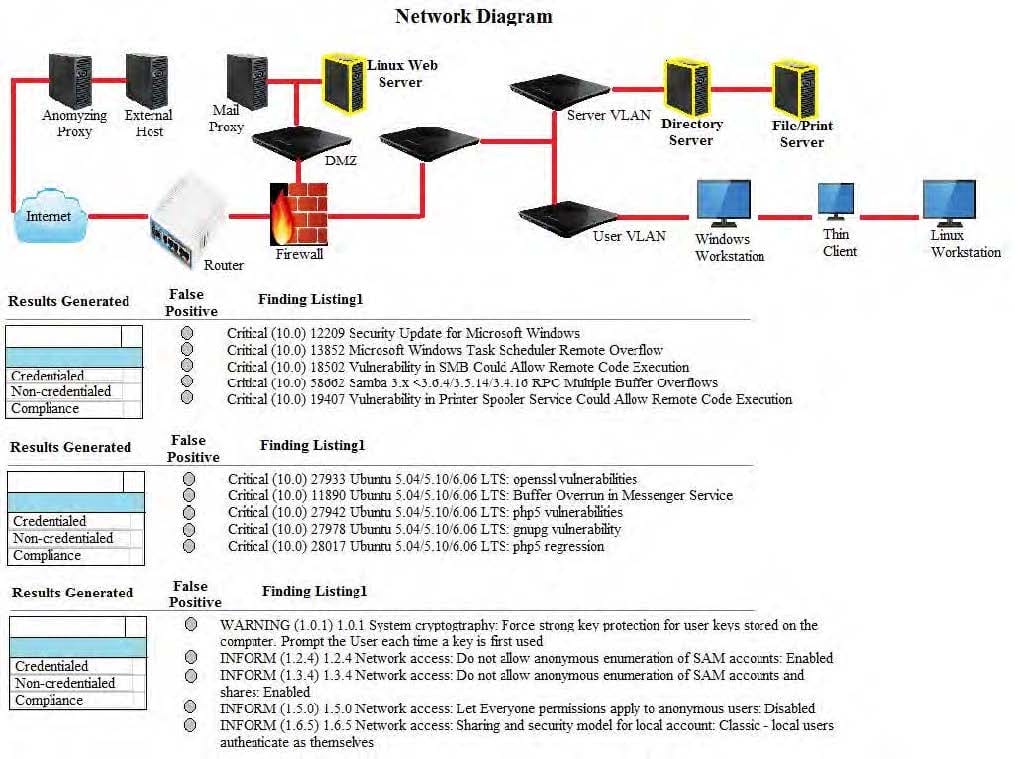
Question 1039:
HOTSPOT
A security analyst performs various types of vulnerability scans.
You must review the vulnerability scan results to determine the type of scan that was executed and determine if a false positive occurred for each device.
Instructions:
Select the drop option for whether the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a
second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the
Next button to continue.
Hot Area:
-
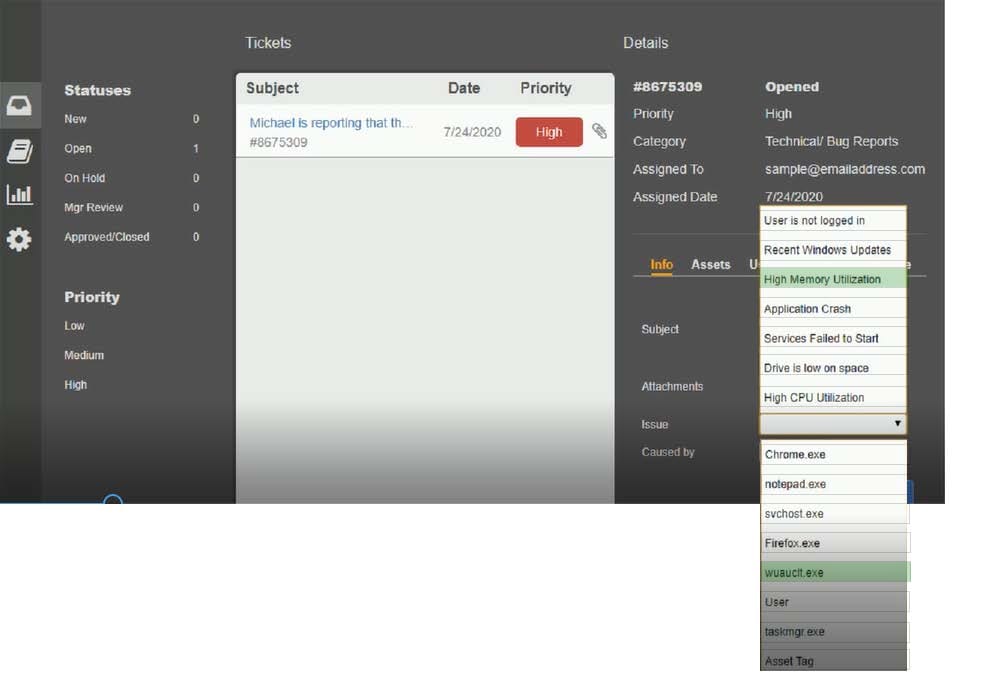
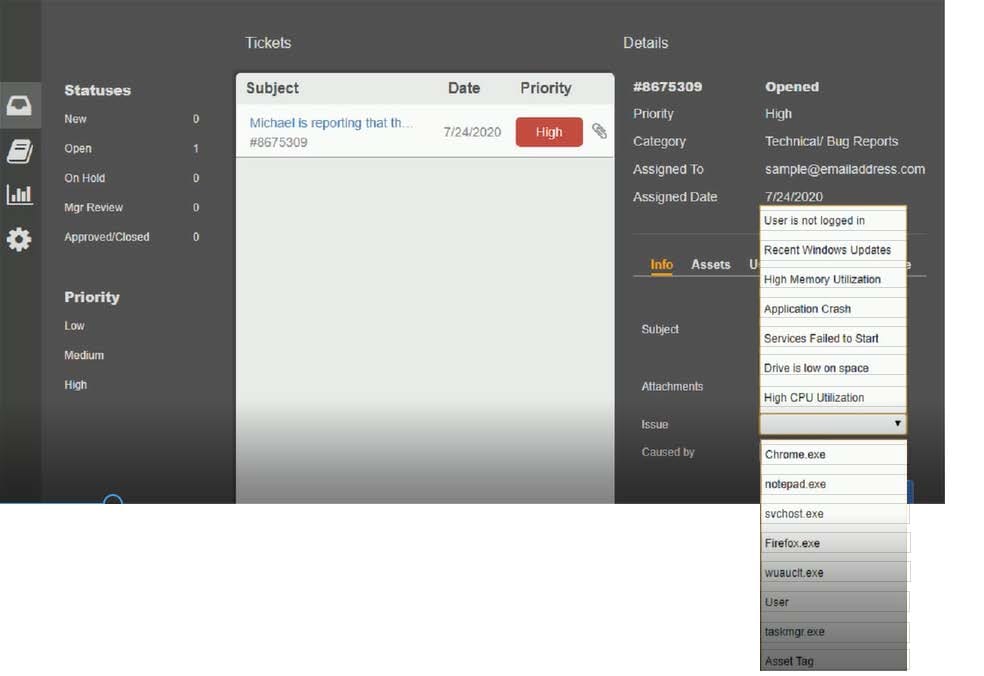
Question 1040:
HOTSPOT
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the help desk ticket queue.
INSTRUCTIONS
Click on the ticket to see the ticket details. Additional content is available on tabs within the ticket.
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
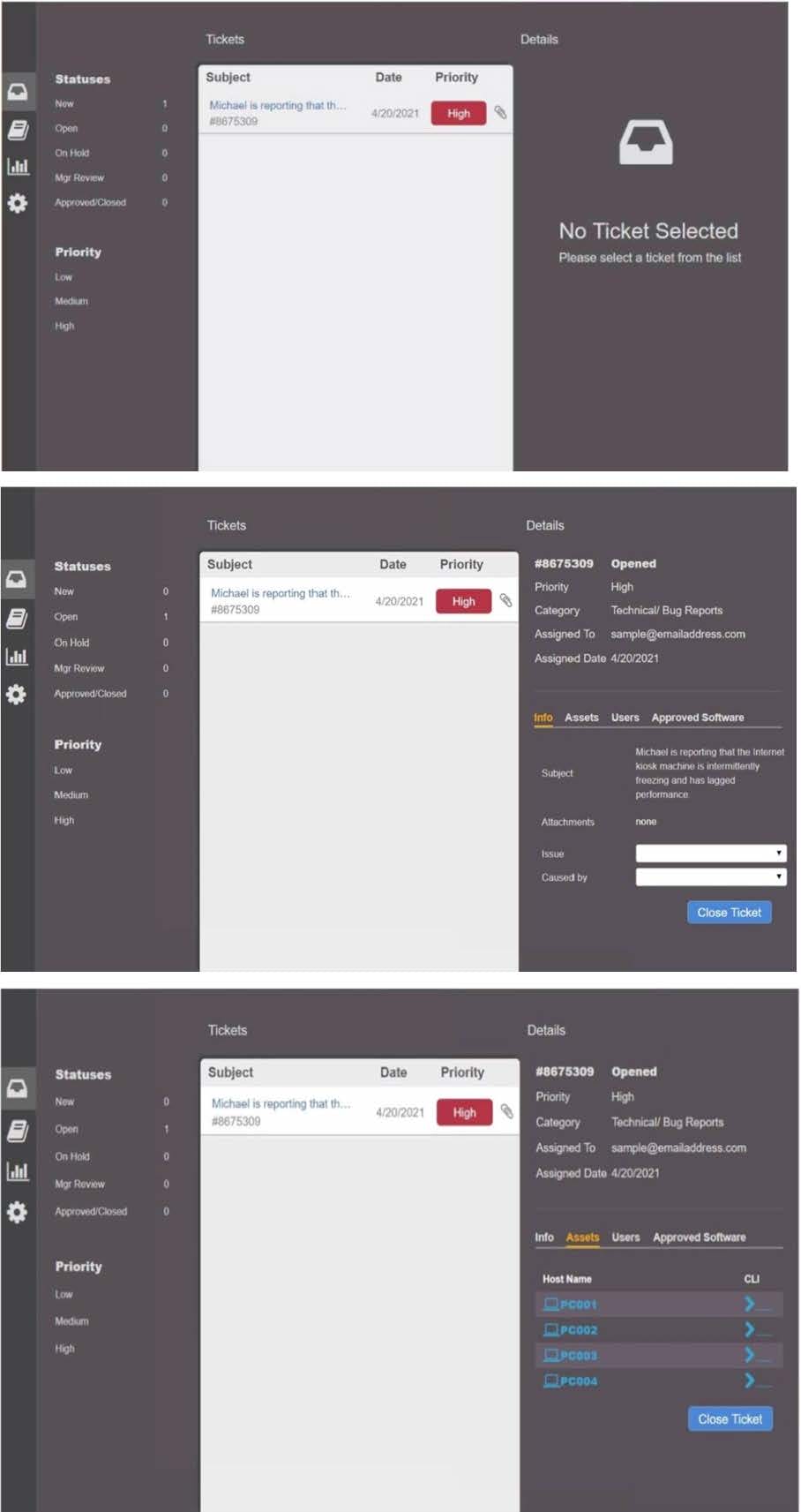
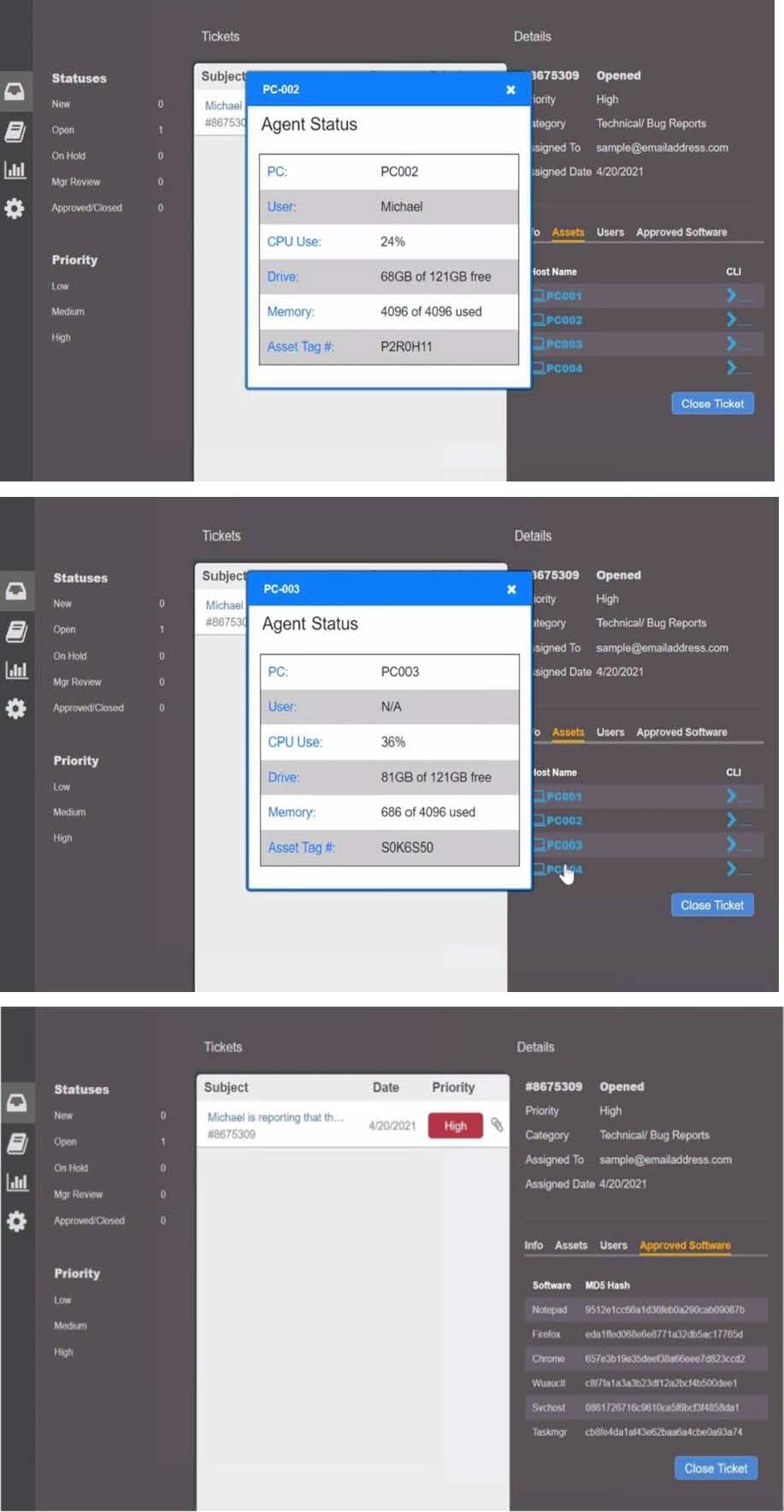
Hot Area:
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.