Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jun 29, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 1001:
A security analyst has received information from a third-party intelligence-sharing resource that indicates employee accounts were breached. Which of the following is the NEXT step the analyst should take to address the issue?
A. Audit access permissions for all employees to ensure least privilege.
B. Force a password reset for the impacted employees and revoke any tokens.
C. Configure SSO to prevent passwords from going outside the local network.
D. Set up privileged access management to ensure auditing is enabled.
-
Question 1002:
A security analyst received an alert from the SIEM indicating numerous login attempts from users outside their usual geographic zones, all of which were initiated through the web-based mail server. The logs indicate all domain accounts experienced two login attempts during the same time frame. Which of the following is the MOST likely cause of this issue?
A. A password-spraying attack was performed against the organization.
B. A DDoS attack was performed against the organization.
C. This was normal shift work activity; the SIEM's AI is learning.
D. A credentialed external vulnerability scan was performed.
-
Question 1003:
During an investigation, a security analyst identified machines that are infected with malware the antivirus was unable to detect. Which of the following is the BEST place to acquire evidence to perform data carving?
A. The system memory
B. The hard drive
C. Network packets
D. The Windows Registry
-
Question 1004:
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking http://
/a.php in a phishing email. To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the __________. A. email server that automatically deletes attached executables.
B. IDS to match the malware sample.
C. proxy to block all connections to
. D. firewall to block connection attempts to dynamic DNS hosts.
-
Question 1005:
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets. Which of the following should be considered FIRST prior to disposing of the electronic data?
A. Sanitization policy
B. Data sovereignty
C. Encryption policy
D. Retention standards
-
Question 1006:
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran
against the same target server.
Tool A reported the following:
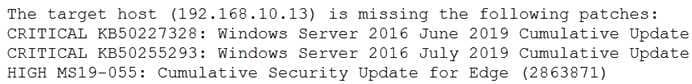
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
A. Tool A is agent based.
B. Tool A used fuzzing logic to test vulnerabilities.
C. Tool A is unauthenticated.
D. Tool B utilized machine learning technology.
E. Tool B is agent based.
F. Tool B is unauthenticated.
-
Question 1007:
Which of the following roles is ultimately responsible for determining the classification levels assigned to specific data sets?
A. Data custodian
B. Data owner
C. Data processor
D. Senior management
-
Question 1008:
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution. Which of the following actions should the technician take to accomplish this task?
A. Add TXT @ "v=spf1 mx include:_spf.comptia.org -all" to the DNS record.
B. Add TXT @ "v=spf1 mx include:_spf.comptia.org -all" to the email server.
C. Add TXT @ "v=spf1 mx include:_spf.comptia.org +all" to the domain controller.
D. Add TXT @ "v=spf1 mx include:_spf.comptia.org +all" to the web server.
-
Question 1009:
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to
create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
A. To create a system baseline
B. To reduce the attack surface
C. To optimize system performance
D. To improve malware detection
-
Question 1010:
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC. Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
A. Gather information from providers, including datacenter specifications and copies of audit reports.
B. Identify SLA requirements for monitoring and logging.
C. Consult with senior management for recommendations.
D. Perform a proof of concept to identify possible solutions.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.