Exam Details
Exam Code
:352-001Exam Name
:CCDE WrittenCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:705 Q&AsLast Updated
:Jul 03, 2023
Cisco Cisco Certifications 352-001 Questions & Answers
-
Question 411:
What are two components of effective change management planning? (Choose two.)
A. a change validation mechanism
B. a what-if analysis for each proposed change
C. an automated change management tracking system
D. a multi-discipline change management team
-
Question 412:
A company would like to distribute a virtual machine (VM) hosting cluster between three data centers with the capability to move VMs between sites. The connectivity between data centers is IP only and the new design should use the existing WAN. Which Layer 2 tunneling technology do you recommend?
A. VPLS
B. L2TPv3
C. OTV
D. AToM
-
Question 413:
What are two valid reasons for aggregating routing information within a network? (Choose two.)
A. to reduce the size of the output of various show commands
B. to reduce the impact of topology changes
C. to reduce the amount of information any specific router within the network must store and process
D. to improve optimal routing within the network
E. to isolate the impact of DDoS attacks
-
Question 414:
The IGP next-hop reachability for a BGP route is lost but a default route is available. Assuming that BGP connectivity is maintained, what will happen to the BGP route?
A. It will be removed from the BGP table.
B. It will be considered invalid for traffic forwarding.
C. It will be considered a valid route.
D. It will be put in a hold-down state by BGP until the next hop has been updated.
-
Question 415:
A Tier-3 Service Provider is evolving into a Tier-2 Service Provider due to the amount of Enterprise business it is receiving. The network engineers are re-evaluating their IP/MPLS design considerations in order to support duplicate/ overlapping IP addressing from their Enterprise customers within each Layer 3 VPN. Which of the following would need to be reviewed to ensure stability in their network?
A. Assigning unique Route Target ID's
B. Assigning unique Route Distinguishers
C. Assigning unique IP address space for the Enterprise NAT/Firewalls
D. Assigning unique VRF ID's to each Layer 3 VPN
-
Question 416:
An IS-IS router is connected to four links and redistributing 75 routes from RIP.
How many LSPs will this router originate?
A. one LSP: containing the router information, internal routes, and external routes
B. two LSPs: one containing router information and internal routes and one containing external routes
C. three LSPs: one containing all links, one containing router information, and one containing external routing information
D. six LSPs: one for each link, one containing router information, and one containing external routing information
-
Question 417:
A company wants to use SSM as the multicast routing protocol inside its network. Some of its multicast applications do not support IGMPv3. In which two ways can the mapping be done when these applications send IGMPv2 join messages? (Choose two.)
A. The Layer 2 switches can send a request to a DNS server.
B. The Layer 3 multicast routers can send a request to a DNS server.
C. The mapping can be done statically at the Layer 2 switches.
D. The mapping can be done statically at the Layer 3 multicast routers.
E. The Layer 2 switches can transform the IGMPv2 join to an IGMPv3lite join.
F. The Layer 3 multicast routers can transform the IGMPv2 join to an IGMPv3lite join.
-
Question 418:
Why should IGP advertisements be disabled on an access link where a host is attached?
A. because hosts do not run routing protocols
B. to prevent the injection of bad routes
C. to reduce router overhead
D. because edge hosts are statically routed
-
Question 419:
Refer to the exhibit.
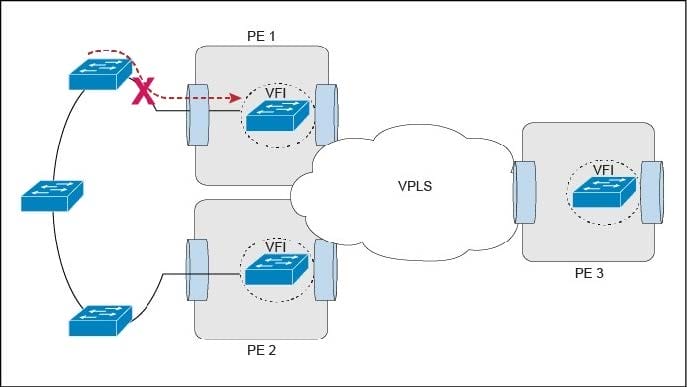
This Layer 2 ring has 10 VLANs with 1000 MAC addresses in each VLAN. Which protocol or mechanism provides the shortest traffic outage if the link marked with "X" fails?
A. PVRST
B. REP
C. MST
D. G.8031
E. BFD
-
Question 420:
Refer to the exhibit.
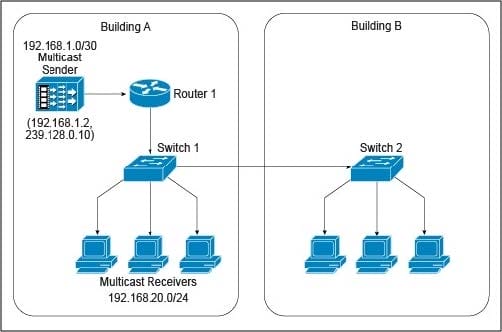
A new IPv4 multicast-based video-streaming service is being provisioned. During the design-validation tests, you realize that the link between the two buildings is carrying multicast traffic even when there are no receivers connected to the switch in Building B and despite IGMP snooping being enabled on both Layer 2 switches and IGMPv2 runs on the hosts. Which design change will prevent the multicast traffic from being unnecessarily flooded throughout the campus network?
A. Enable PIM snooping on both Layer 2 switches.
B. Enable multicast storm control on the link between Switch 1 and Switch 2.
C. Use static Layer 2 MAC forwarding entries on Switch 1.
D. Change the IPv4 multicast group address such that it excludes the usage of link-local MAC addresses.
E. Ensure that Switch 1 is an IGMP querier.
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-001 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.