Exam Details
Exam Code
:350-201Exam Name
:Performing CyberOps Using Cisco Security Technologies (CBRCOR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:139 Q&AsLast Updated
:Aug 06, 2025
Cisco CyberOps Professional 350-201 Questions & Answers
-
Question 41:
A company launched an e-commerce website with multiple points of sale through internal and external e-stores. Customers access the stores from the public website, and employees access the stores from the intranet with an SSO. Which action is needed to comply with PCI standards for hardening the systems?
A. Mask PAN numbers
B. Encrypt personal data
C. Encrypt access
D. Mask sales details
-
Question 42:
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
A. aligning access control policies
B. exfiltration during data transfer
C. attack using default accounts
D. data exposure from backups
-
Question 43:
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site through which the employee downloaded a PDF attachment infected with ransomware. The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server.
Which security solution is needed at this stage to mitigate the attack?
A. web security solution
B. email security solution
C. endpoint security solution
D. network security solution
-
Question 44:
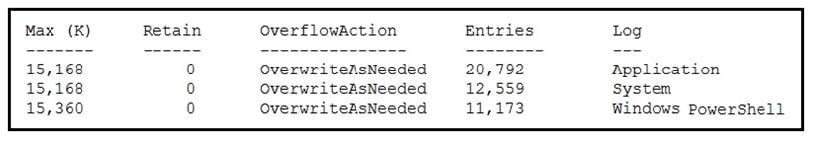
Refer to the exhibit. An employee is a victim of a social engineering phone call and installs remote access software to allow an "MS Support" technician to check his machine for malware. The employee becomes suspicious after the remote technician requests payment in the form of gift cards. The employee has copies of multiple, unencrypted database files, over 400 MB each, on his system and is worried that the scammer copied the files off but has no proof of it. The remote technician was connected sometime between 2:00 pm and 3:00 pm over https.
What should be determined regarding data loss between the employee's laptop and the remote technician's system?
A. No database files were disclosed
B. The database files were disclosed
C. The database files integrity was violated
D. The database files were intentionally corrupted, and encryption is possible
-
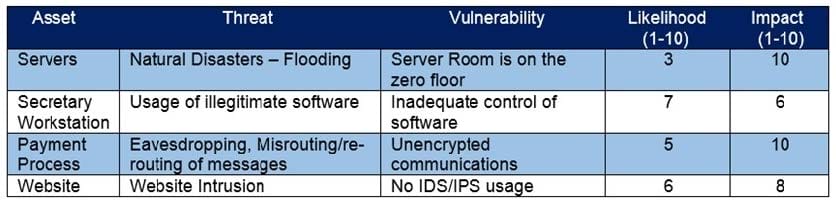
Question 45:
Refer to the exhibit. Which asset has the highest risk value?
A. servers
B. website
C. payment process
D. secretary workstation
-
Question 46:
What is the purpose of hardening systems?
A. to securely configure machines to limit the attack surface
B. to create the logic that triggers alerts when anomalies occur
C. to identify vulnerabilities within an operating system
D. to analyze attacks to identify threat actors and points of entry
-
Question 47:
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled "Invoice RE: 0004489". The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web.
What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
-
Question 48:
A SOC analyst is notified by the network monitoring tool that there are unusual types of internal traffic on IP subnet 103.861.2117.0/24. The analyst discovers unexplained encrypted data files on a computer system that belongs on that specific subnet.
What is the cause of the issue?
A. DDoS attack
B. phishing attack
C. virus outbreak
D. malware outbreak
-
Question 49:
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is communicating over port 80 with an external server and that the file hash is associated with Duqu malware. Which tactics, techniques, and procedures align with this analysis?
A. Command and Control, Application Layer Protocol, Duqu
B. Discovery, Remote Services: SMB/Windows Admin Shares, Duqu
C. Lateral Movement, Remote Services: SMB/Windows Admin Shares, Duqu
D. Discovery, System Network Configuration Discovery, Duqu
-
Question 50:
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high.
Which step should be taken to continue the investigation?
A. Run the sudo sysdiagnose command
B. Run the sh command
C. Run the w command
D. Run the who command
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.