Exam Details
Exam Code
:350-201Exam Name
:Performing CyberOps Using Cisco Security Technologies (CBRCOR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:139 Q&AsLast Updated
:Aug 06, 2025
Cisco CyberOps Professional 350-201 Questions & Answers
-
Question 11:
Refer to the exhibit. Two types of clients are accessing the front ends and the core database that manages transactions, access control, and atomicity. What is the threat model for the SQL database?

A. An attacker can initiate a DoS attack.
B. An attacker can read or change data.
C. An attacker can transfer data to an external server.
D. An attacker can modify the access logs.
-
Question 12:
Which bash command will print all lines from the “colors.txt” file containing the non case-sensitive pattern “Yellow”?
A. grep -i “yellow” colors.txt
B. locate “yellow” colors.txt
C. locate -i “Yellow” colors.txt
D. grep “Yellow” colors.txt
-
Question 13:
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal data. Which type of attack is occurring?
A. Address Resolution Protocol poisoning
B. session hijacking attack
C. teardrop attack
D. Domain Name System poisoning
-
Question 14:
Refer to the exhibit. An engineer is performing static analysis of a file received and reported by a user. Which risk is indicated in this STIX?
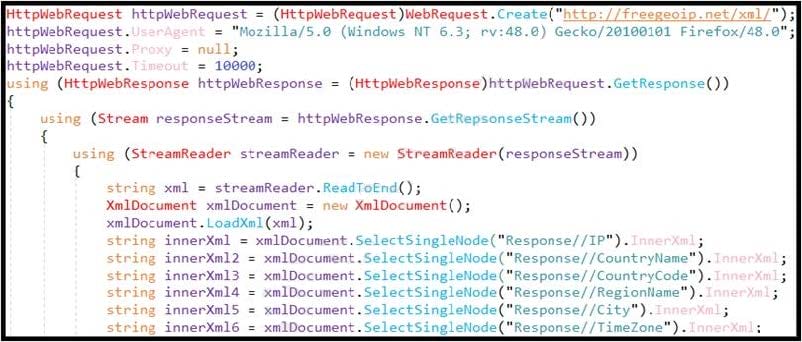
A. The file is redirecting users to a website that requests privilege escalations from the user.
B. The file is redirecting users to the website that is downloading ransomware to encrypt files.
C. The file is redirecting users to a website that harvests cookies and stored account information.
D. The file is redirecting users to a website that is determining users’ geographic location.
-
Question 15:
A security architect in an automotive factory is working on the Cyber Security Management System and is implementing procedures and creating policies to prevent attacks. Which standard must the architect apply?
A. IEC62446
B. IEC62443
C. IEC62439-3
D. IEC62439-2
-
Question 16:
An organization suffered a security breach in which the attacker exploited a Netlogon Remote Protocol vulnerability for further privilege escalation. Which two actions should the incident response team take to prevent this type of attack from reoccurring? (Choose two.)
A. Implement a patch management process.
B. Scan the company server files for known viruses.
C. Apply existing patches to the company servers.
D. Automate antivirus scans of the company servers.
E. Define roles and responsibilities in the incident response playbook.
-
Question 17:
A SOC team is investigating a recent, targeted social engineering attack on multiple employees. Cross-correlated log analysis revealed that two hours before the attack, multiple assets received requests on TCP port 79. Which action should be taken by the SOC team to mitigate this attack?
A. Disable BIND forwarding from the DNS server to avoid reconnaissance.
B. Disable affected assets and isolate them for further investigation.
C. Configure affected devices to disable NETRJS protocol.
D. Configure affected devices to disable the Finger service.
-
Question 18:
What is idempotence?
A. the assurance of system uniformity throughout the whole delivery process
B. the ability to recover from failures while keeping critical services running
C. the necessity of setting maintenance of individual deployment environments
D. the ability to set the target environment configuration regardless of the starting state
-
Question 19:
A SOC engineer discovers that the organization had three DDOS attacks overnight. Four servers are reported offline, even though the hardware seems to be working as expected. One of the offline servers is affecting the pay system reporting times. Three employees, including executive management, have reported ransomware on their laptops. Which steps help the engineer understand a comprehensive overview of the incident?
A. Run and evaluate a full packet capture on the workloads, review SIEM logs, and define a root cause.
B. Run and evaluate a full packet capture on the workloads, review SIEM logs, and plan mitigation steps.
C. Check SOAR to learn what the security systems are reporting about the overnight events, research the attacks, and plan mitigation step.
D. Check SOAR to know what the security systems are reporting about the overnight events, review the threat vectors, and define a root cause.
-
Question 20:
Which action should be taken when the HTTP response code 301 is received from a web application?
A. Update the cached header metadata.
B. Confirm the resource's location.
C. Increase the allowed user limit.
D. Modify the session timeout setting.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.