Exam Details
Exam Code
:350-201Exam Name
:Performing CyberOps Using Cisco Security Technologies (CBRCOR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:139 Q&AsLast Updated
:Aug 06, 2025
Cisco CyberOps Professional 350-201 Questions & Answers
-
Question 31:
The SIEM tool informs a SOC team of a suspicious file. The team initializes the analysis with an automated sandbox tool, sets up a controlled laboratory to examine the malware specimen, and proceeds with behavioral analysis. What is the next step in the malware analysis process?
A. Perform static and dynamic code analysis of the specimen.
B. Unpack the specimen and perform memory forensics.
C. Contain the subnet in which the suspicious file was found.
D. Document findings and clean-up the laboratory.
-
Question 32:
A logistic company must use an outdated application located in a private VLAN during the migration to new technologies. The IPS blocked and reported an unencrypted communication. Which tuning option should be applied to IPS?
A. Allow list only authorized hosts to contact the application's IP at a specific port.
B. Allow list HTTP traffic through the corporate VLANS.
C. Allow list traffic to application's IP from the internal network at a specific port.
D. Allow list only authorized hosts to contact the application's VLAN.
-
Question 33:
Refer to the exhibit. An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?

A. malware break
B. data theft
C. elevation of privileges
D. denial-of-service
-
Question 34:
What is needed to assess risk mitigation effectiveness in an organization?
A. analysis of key performance indicators
B. compliance with security standards
C. cost-effectiveness of control measures
D. updated list of vulnerable systems
-
Question 35:
Refer to the exhibit. Where is the MIME type that should be followed indicated?

A. x-test-debug
B. strict-transport-security
C. x-xss-protection
D. x-content-type-options
-
Question 36:
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
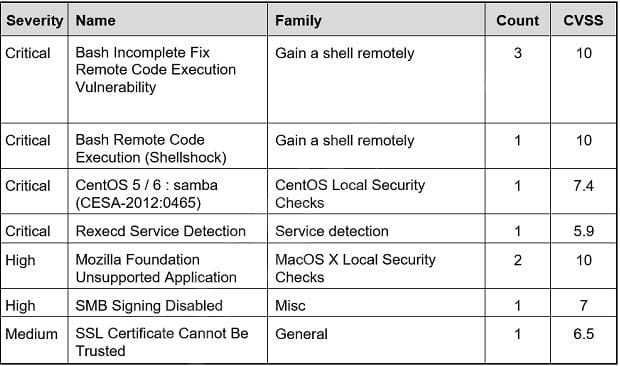
A. Evaluate service disruption and associated risk before prioritizing patches.
B. Perform root cause analysis for all detected vulnerabilities.
C. Remediate all vulnerabilities with descending CVSS score order.
D. Temporarily shut down unnecessary services until patch deployment ends.
-
Question 37:
Refer to the exhibit. For IP 192.168.1.209, what are the risk level, activity, and next step?

A. high risk level, anomalous periodic communication, quarantine with antivirus
B. critical risk level, malicious server IP, run in a sandboxed environment
C. critical risk level, data exfiltration, isolate the device
D. high risk level, malicious host, investigate further
-
Question 38:
Refer to the exhibit. What is the connection status of the ICMP event?

A. blocked by a configured access policy rule
B. allowed by a configured access policy rule
C. blocked by an intrusion policy rule
D. allowed in the default action
-
Question 39:
An analyst wants to upload an infected file containing sensitive information to a hybrid-analysis sandbox. According to the NIST.SP 800-150 guide to cyber threat information sharing, what is the analyst required to do before uploading the file to safeguard privacy?
A. Verify hash integrity.
B. Remove all personally identifiable information.
C. Ensure the online sandbox is GDPR compliant.
D. Lock the file to prevent unauthorized access.
-
Question 40:

Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior.
Which type of compromise is occurring?
A. compromised insider
B. compromised root access
C. compromised database tables
D. compromised network
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.