Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jul 25, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 701:
The follows is an email header. What address is that of the true originator of the message?
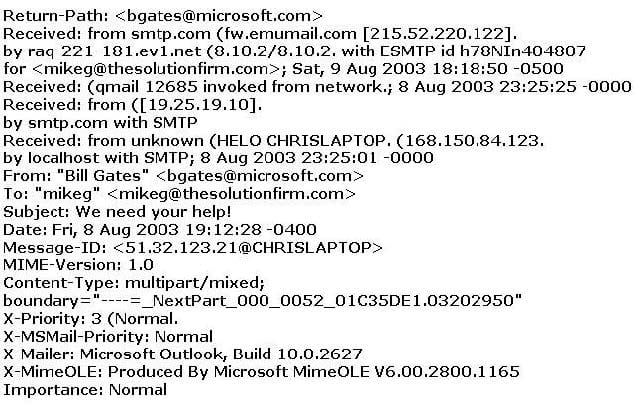
A. 19.25.19.10
B. 51.32.123.21
C. 168.150.84.123
D. 215.52.220.122
E. 8.10.2/8.10.2
-
Question 702:
Bob wants to prevent attackers from sniffing his passwords on the wired network.
Which of the following lists the best options?
A. RSA,LSA,POP
B. SSID,WEP,Kerberos
C. SMB,SMTP,Smart card
D. Kerberos,Smart card,Stanford SRP
-
Question 703:
Ethereal works best on ____________.
A. Switched networks
B. Linux platforms
C. Networks using hubs
D. Windows platforms
E. LAN's
-
Question 704:
Samantha was hired to perform an internal security test of XYZ. She quickly realized that all networks are making use of switches instead of traditional hubs. This greatly limits her ability to gather information through network sniffing.
Which of the following techniques can she use to gather information from the switched network or to disable some of the traffic isolation features of the switch? (Choose two)
A. Ethernet Zapping
B. MAC Flooding
C. Sniffing in promiscuous mode
D. ARP Spoofing
-
Question 705:
A POP3 client contacts the POP3 server:
A. To send mail
B. To receive mail
C. to send and receive mail
D. to get the address to send mail to
E. initiate a UDP SMTP connection to read mail
-
Question 706:
A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password.
Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
A. Invalid Username
B. Invalid Password
C. Authentication Failure
D. Login Attempt Failed
E. Access Denied
-
Question 707:
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in "Ettercap"?
A. This command will provide you the entire list of hosts in the LAN
B. This command will check if someone is poisoning you and will report its IP.
C. This command will detach from console and log all the collected passwords from the network to a file.
D. This command broadcasts ping to scan the LAN instead of ARP request of all the subnet IPs.
-
Question 708:
Erik notices a big increase in UDP packets sent to port 1026 and 1027 occasionally. He enters the
following at the command prompt.
$ nc -l -p 1026 -u -v
In response, he sees the following message.
cell(?(c)????STOPALERT77STOP! WINDOWS REQUIRES IMMEDIATE ATTENTION.
Windows has found 47 Critical Errors.
To fix the errors please do the following:
1.
Download Registry Repair from: www.reg-patch.com
2.
Install Registry Repair
3.
Run Registry Repair
4.
Reboot your computer
FAILURE TO ACT NOW MAY LEAD TO DATA LOSS AND CORRUPTION!
What would you infer from this alert?
A. The machine is redirecting traffic to www.reg-patch.com using adware
B. It is a genuine fault of windows registry and the registry needs to be backed up
C. An attacker has compromised the machine and backdoored ports 1026 and 1027
D. It is a messenger spam. Windows creates a listener on one of the low dynamic ports from 1026 to 1029 and the message usually promotes malware disguised as legitimate utilities
-
Question 709:
A file integrity program such as Tripwire protects against Trojan horse attacks by:
A. Automatically deleting Trojan horse programs
B. Rejecting packets generated by Trojan horse programs
C. Using programming hooks to inform the kernel of Trojan horse behavior
D. Helping you catch unexpected changes to a system utility file that might indicate it had been replaced by a Trojan horse
-
Question 710:
Sniffing is considered an active attack.
A. True
B. False
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.