Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jul 25, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 691:
Global deployment of RFC 2827 would help mitigate what classification of attack?
A. Sniffing attack
B. Denial of service attack
C. Spoofing attack
D. Reconnaissance attack
E. Prot Scan attack
-
Question 692:
Which one of the following instigates a SYN flood attack?
A. Generating excessive broadcast packets.
B. Creating a high number of half-open connections.
C. Inserting repetitive Internet Relay Chat (IRC) messages.
D. A large number of Internet Control Message Protocol (ICMP) traces.
-
Question 693:
Tess King, the evil hacker, is purposely sending fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65, 536 bytes. From the information given, what type of attack is Tess King attempting to perform?
A. Syn flood
B. Smurf
C. Ping of death
D. Fraggle
-
Question 694:
Exhibit:
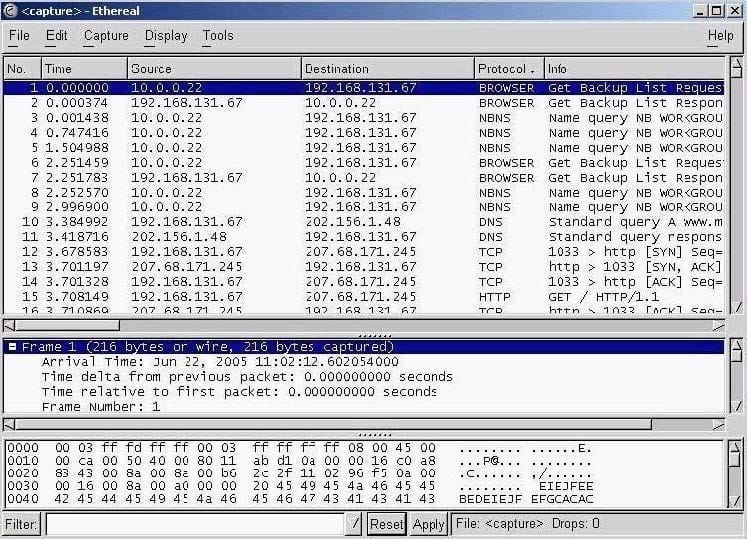
You have captured some packets in Ethereal. You want to view only packets sent from 10.0.0.22. What filter will you apply?
A. ip = 10.0.0.22
B. ip.src == 10.0.0.22
C. ip.equals 10.0.0.22
D. ip.address = 10.0.0.22
-
Question 695:
Which of the following is not considered to be a part of active sniffing?
A. MAC Flooding
B. ARP Spoofing
C. SMAC Fueling
D. MAC Duplicating
-
Question 696:
ARP poisoning is achieved in _____ steps
A. 1
B. 2
C. 3
D. 4
-
Question 697:
How would you describe a simple yet very effective mechanism for sending and receiving unauthorized information or data between machines without alerting any firewalls and IDS's on a network?
A. Covert Channel
B. Crafted Channel
C. Bounce Channel
D. Deceptive Channel
-
Question 698:
Which of the following display filters will you enable in Ethereal to view the three-way handshake for a connection from host 192.168.0.1?
A. ip == 192.168.0.1 and tcp.syn
B. ip.addr = 192.168.0.1 and syn = 1
C. ip.addr==192.168.0.1 and tcp.flags.syn
D. ip.equals 192.168.0.1 and syn.equals on
-
Question 699:
When Jason moves a file via NFS over the company's network, you want to grab a copy of it by sniffing. Which of the following tool accomplishes this?
A. macof
B. webspy
C. filesnarf
D. nfscopy
-
Question 700:
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
A. Snort
B. argus
C. TCPflow
D. Tcpdump
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.