Exam Details
Exam Code
:312-50V7Exam Name
:Ethical Hacking and Countermeasures (CEHv7)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:514 Q&AsLast Updated
:Jun 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V7 Questions & Answers
-
Question 311:
NTP allows you to set the clocks on your systems very accurately, to within 100ms and sometimes- even 10ms. Knowing the exact time is extremely important for enterprise security. Various security protocols depend on an accurate source of time information in order to prevent "playback" attacks. These protocols tag their communications with the current time, to prevent attackers from replaying the same communications, e.g., a login/password interaction or even an entire communication, at a later date. One can circumvent this tagging, if the clock can be set back to the time the communication was recorded. An attacker attempts to try corrupting the clocks on devices on your network. You run Wireshark to detect the NTP traffic to see if there are any irregularities on the network. What port number you should enable in Wireshark display filter to view NTP packets?
A. TCP Port 124
B. UDP Port 125
C. UDP Port 123
D. TCP Port 126
-
Question 312:
Jane wishes to forward X-Windows traffic to a remote host as well as POP3 traffic. She is worried that adversaries might be monitoring the communication link and could inspect captured traffic. She would like to tunnel the information to the remote end but does not have VPN capabilities to do so. Which of the following tools can she use to protect the link?
A. MD5
B. PGP
C. RSA
D. SSH
-
Question 313:
John runs a Web server, IDS and firewall on his network. Recently his Web server has been under constant hacking attacks. He looks up the IDS log files and sees no intrusion attempts but the Web server constantly locks up and needs rebooting due to various brute force and buffer overflow attacks but still the IDS alerts no intrusion whatsoever. John becomes suspicious and views the Firewall logs and he notices huge SSL connections constantly hitting his Web server. Hackers have been using the encrypted HTTPS protocol to send exploits to the Web server and that was the reason the IDS did not detect the intrusions. How would John protect his network from these types of attacks?
A. Install a proxy server and terminate SSL at the proxy
B. Enable the IDS to filter encrypted HTTPS traffic
C. Install a hardware SSL "accelerator" and terminate SSL at this layer
D. Enable the Firewall to filter encrypted HTTPS traffic
-
Question 314:
To see how some of the hosts on your network react, Winston sends out SYN packets to an IP range. A number of IPs respond with a SYN/ACK response. Before the connection is established he sends RST packets to those hosts to stop the session. Winston has done this to see how his intrusion detection system will log the traffic. What type of scan is Winston attempting here?
A. Winston is attempting to find live hosts on your company's network by using an XMAS scan.
B. He is utilizing a SYN scan to find live hosts that are listening on your network.
C. This type of scan he is using is called a NULL scan.
D. He is using a half-open scan to find live hosts on your network.
-
Question 315:
What is the correct order of steps in CEH System Hacking Cycle?
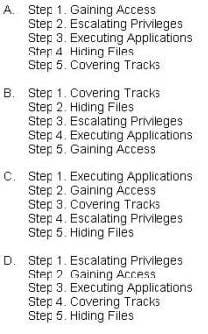
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 316:
Identify SQL injection attack from the HTTP requests shown below:
A. http://www.myserver.c0m/search.asp?lname=smith%27%3bupdate%20usertable%20set%20passwd %3d%27hAx0r%27%3b--%00
B. http://www.myserver.c0m/script.php?mydata=%3cscript%20src=%22
C. http%3a%2f%2fwww.yourserver.c0m%2fbadscript.js%22%3e%3c%2fscript%3e
D. http://www.victim.com/example accountnumber=67891andcreditamount=999999999
-
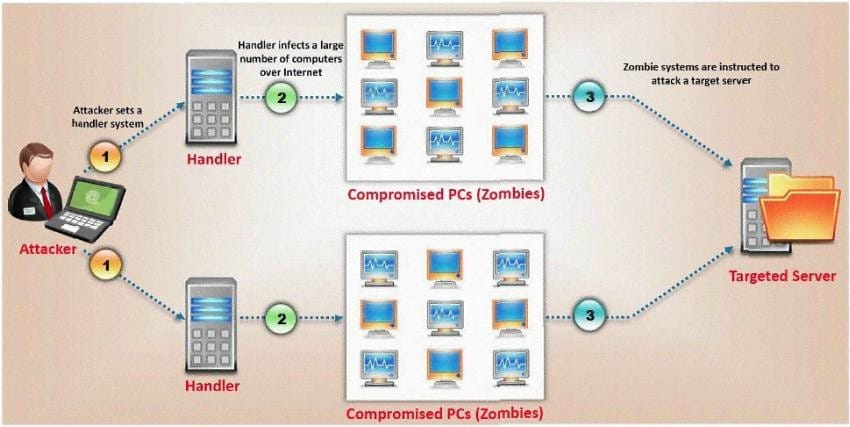
Question 317:
What type of attack is shown here?
A. Bandwidth exhaust Attack
B. Denial of Service Attack
C. Cluster Service Attack
D. Distributed Denial of Service Attack
-
Question 318:
Joseph has just been hired on to a contractor company of the Department of Defense as their Senior Security Analyst. Joseph has been instructed on the company's strict security policies that have been implemented, and the policies that have yet to be put in place. Per the Department of Defense, all DoD users and the users of their contractors must use two-factor authentication to access their networks. Joseph has been delegated the task of researching and implementing the best two-factor authentication method for his company. Joseph's supervisor has told him that they would like to use some type of hardware device in tandem with a security or identifying pin number. Joseph's company has already researched using smart cards and all the resources needed to implement them, but found the smart cards to not be cost effective. What type of device should Joseph use for two-factor authentication?
A. Biometric device
B. OTP
C. Proximity cards
D. Security token
-
Question 319:
In which step Steganography fits in CEH System Hacking Cycle (SHC)
A. Step 2: Crack the password
B. Step 1: Enumerate users
C. Step 3: Escalate privileges
D. Step 4: Execute applications
E. Step 5: Hide files
F. Step 6: Cover your tracks
-
Question 320:
Which definition below best describes a covert channel?
A. A server program using a port that is not well known
B. Making use of a protocol in a way it was not intended to be used
C. It is the multiplexing taking place on a communication link
D. It is one of the weak channels used by WEP that makes it insecure
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V7 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.