312-50V7 Exam Details
-
Exam Code
:312-50V7 -
Exam Name
:Ethical Hacking and Countermeasures (CEHv7) -
Certification
:EC-COUNCIL Certifications -
Vendor
:EC-COUNCIL -
Total Questions
:514 Q&As -
Last Updated
:Jan 21, 2026
EC-COUNCIL 312-50V7 Online Questions & Answers
-
Question 1:
Botnets are networks of compromised computers that are controlled remotely and surreptitiously by one or more cyber criminals. How do cyber criminals infect a victim's computer with bots? (Select 4 answers)
A. Attackers physically visit every victim's computer to infect them with malicious software
B. Home computers that have security vulnerabilities are prime targets for botnets
C. Spammers scan the Internet looking for computers that are unprotected and use these "open-doors" to install malicious software
D. Attackers use phishing or spam emails that contain links or attachments
E. Attackers use websites to host the bots utilizing Web Browser vulnerabilities -
Question 2:
Which Windows system tool checks integrity of critical files that has been digitally signed by Microsoft?
A. signverif.exe
B. sigverif.exe
C. msverif.exe
D. verifier.exe -
Question 3:
Harold is the senior security analyst for a small state agency in New York. He has no other security professionals that work under him, so he has to do all the security-related tasks for the agency. Coming from a computer hardware background, Harold does not have a lot of experience with security methodologies and technologies, but he was the only one who applied for the position. Harold is currently trying to run a Sniffer on the agency's network to get an idea of what kind of traffic is being passed around, but the program he is using does not seem to be capturing anything. He pours through the Sniffer's manual, but cannot find anything that directly relates to his problem. Harold decides to ask the network administrator if he has any thoughts on the problem. Harold is told that the Sniffer was not working because the agency's network is a switched network, which cannot be sniffed by some programs without some tweaking. What technique could Harold use to sniff his agency's switched network?
A. ARP spoof the default gateway
B. Conduct MiTM against the switch
C. Launch smurf attack against the switch
D. Flood the switch with ICMP packets -
Question 4:
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
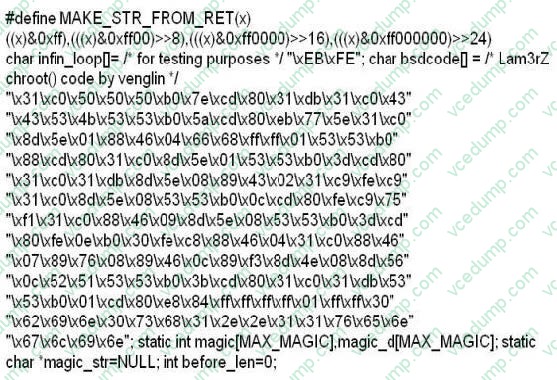
What can he infer from this file?
A. A picture that has been renamed with a .txt extension
B. An encrypted file
C. An encoded file
D. A buffer overflow -
Question 5:
Which of the following LM hashes represents a password of less than 8 characters?
A. 0182BD0BD4444BF836077A718CCDF409
B. 44EFCE164AB921CQAAD3B435B51404EE
C. BA810DBA98995F1817306D272A9441BB
D. CEC52EB9C8E3455DC2265B23734E0DAC
E. B757BF5C0D87772FAAD3B435B51404EE
F. E52CAC67419A9A224A3B108F3FA6CB6D -
Question 6:
What two things will happen if a router receives an ICMP packet, which has a TTL value of 1, and the destination host is several hops away? (Select 2 answers)
A. The router will discard the packet
B. The router will decrement the TTL value and forward the packet to the next router on the path to the destination host
C. The router will send a time exceeded message to the source host
D. The router will increment the TTL value and forward the packet to the next router on the path to the destination host.
E. The router will send an ICMP Redirect Message to the source host -
Question 7:
Paul has just finished setting up his wireless network. He has enabled numerous security features such as changing the default SSID, enabling WPA encryption, and enabling MAC filtering on his wireless router. Paul notices that when he uses his wireless connection, the speed is sometimes 54 Mbps and sometimes it is only 24Mbps or less. Paul connects to his wireless router's management utility and notices that a machine with an unfamiliar name is connected through his wireless connection. Paul checks the router's logs and notices that the unfamiliar machine has the same MAC address as his laptop. What is Paul seeing here?
A. MAC spoofing
B. Macof
C. ARP spoofing
D. DNS spoofing -
Question 8:
A company is legally liable for the content of email that is sent from its systems, regardless of whether the message was sent for private or business-related purposes. This could lead to prosecution for the sender and for the company's directors if, for example, outgoing email was found to contain material that was pornographic, racist, or likely to incite someone to commit an act of terrorism. You can always defend yourself by "ignorance of the law" clause.
A. true
B. false -
Question 9:
__________ is found in all versions of NTFS and is described as the ability to fork file data into existing files without affecting their functionality, size, or display to traditional file browsing utilities like dir or Windows Explorer
A. Alternate Data Streams
B. Merge Streams
C. Steganography
D. NetBIOS vulnerability -
Question 10:
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
A. IP Security (IPSEC)
B. Multipurpose Internet Mail Extensions (MIME)
C. Pretty Good Privacy (PGP)
D. Hyper Text Transfer Protocol with Secure Socket Layer (HTTPS)
Related Exams:
-
112-51
EC-Council Certified Network Defense Essentials (NDE) -
212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0 -
212-77
EC-Council Certified Linux Security -
212-81
EC-Council Certified Encryption Specialist (ECES) -
212-82
EC-Council Certified Cybersecurity Technician (C|CT) -
212-89
EC Council Certified Incident Handler (ECIH v3) -
312-38
EC-Council Certified Network Defender (CND) -
312-39
EC-Council Certified SOC Analyst (CSA) -
312-40
EC-Council Certified Cloud Security Engineer (CCSE) -
312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V7 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.