Exam Details
Exam Code
:312-50V7Exam Name
:Ethical Hacking and Countermeasures (CEHv7)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:514 Q&AsLast Updated
:Jun 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V7 Questions & Answers
-
Question 301:
WWW wanderers or spiders are programs that traverse many pages in the World Wide Web by recursively retrieving linked pages. Search engines like Google, frequently spider web pages for indexing. How will you stop web spiders from crawling certain directories on your website?
A. Place robots.txt file in the root of your website with listing of directories that you don't want to be crawled
B. Place authentication on root directories that will prevent crawling from these spiders
C. Enable SSL on the restricted directories which will block these spiders from crawling
D. Place "HTTP:NO CRAWL" on the html pages that you don't want the crawlers to index
-
Question 302:
Bank of Timbuktu is a medium-sized, regional financial institution in Timbuktu. The bank has deployed a new Internet-accessible Web application recently. Customers can access their account balances, transfer money between accounts, pay bills and conduct online financial business using a Web browser.
John Stevens is in charge of information security at Bank of Timbuktu. After one month in production, several customers have complained about the Internet enabled banking application. Strangely, the account balances of many of the bank's customers had been changed! However, money hasn't been removed from the bank; instead, money was transferred between accounts. Given this attack profile, John Stevens reviewed the Web application's logs and found the following entries:
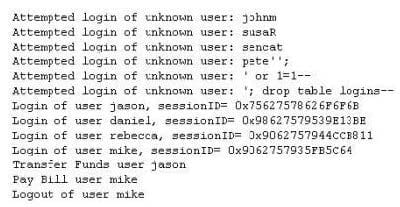
What kind of attack did the Hacker attempt to carry out at the bank?
A. Brute force attack in which the Hacker attempted guessing login ID and password from password cracking tools.
B. The Hacker attempted Session hijacking, in which the Hacker opened an account with the bank, then logged in to receive a session ID, guessed the next ID and took over Jason's session.
C. The Hacker used a generator module to pass results to the Web server and exploited Web application CGI vulnerability.
D. The Hacker first attempted logins with suspected user names, then used SQL Injection to gain access to valid bank login IDs.
-
Question 303:
You are writing security policy that hardens and prevents Footprinting attempt by Hackers. Which of the following countermeasures will NOT be effective against this attack?
A. Configure routers to restrict the responses to Footprinting requests
B. Configure Web Servers to avoid information leakage and disable unwanted protocols
C. Lock the ports with suitable Firewall configuration
D. Use an IDS that can be configured to refuse suspicious traffic and pick up Footprinting patterns
E. Evaluate the information before publishing it on the Website/Intranet
F. Monitor every employee computer with Spy cameras, keyloggers and spy on them
G. Perform Footprinting techniques and remove any sensitive information found on DMZ sites
H. Prevent search engines from caching a Webpage and use anonymous registration services
I. Disable directory and use split-DNS
-
Question 304:
Why attackers use proxy servers?
A. To ensure the exploits used in the attacks always flip reverse vectors
B. Faster bandwidth performance and increase in attack speed
C. Interrupt the remote victim's network traffic and reroute the packets to attackers machine
D. To hide the source IP address so that an attacker can hack without any legal corollary
-
Question 305:
The SNMP Read-Only Community String is like a password. The string is sent along with each SNMP Get-Request and allows (or denies) access to a device. Most network vendors ship their equipment with a default password of "public". This is the so-called "default public community string". How would you keep
intruders from getting sensitive information regarding the network devices using SNMP? (Select 2 answers)
A. Enable SNMPv3 which encrypts username/password authentication
B. Use your company name as the public community string replacing the default 'public'
C. Enable IP filtering to limit access to SNMP device
D. The default configuration provided by device vendors is highly secure and you don't need to change anything
-
Question 306:
What command would you type to OS fingerprint a server using the command line?
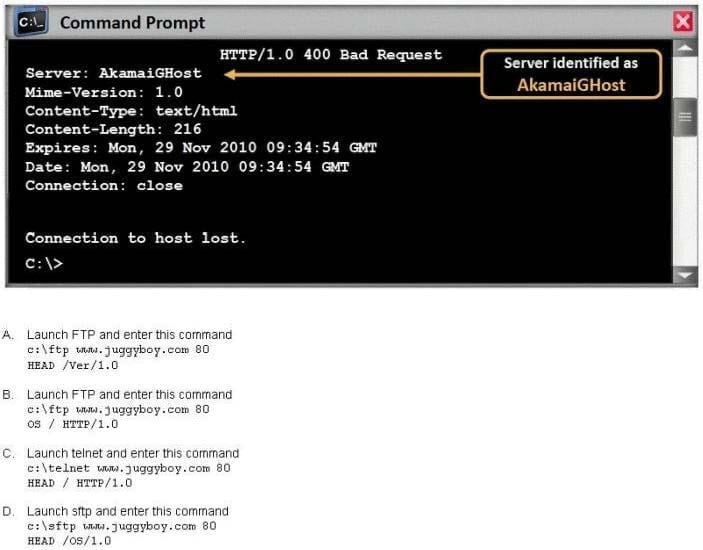
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 307:
What do you call a pre-computed hash?
A. Sun tables
B. Apple tables
C. Rainbow tables
D. Moon tables
-
Question 308:
Which type of password cracking technique works like dictionary attack but adds some numbers and symbols to the words from the dictionary and tries to crack the password?
A. Dictionary attack
B. Brute forcing attack
C. Hybrid attack
D. Syllable attack
E. Rule-based attack
-
Question 309:
You generate MD5 128-bit hash on all files and folders on your computer to keep a baseline check for security reasons?
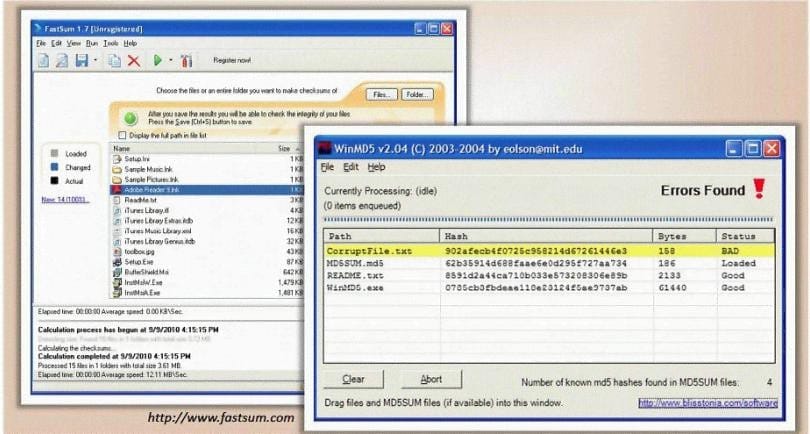
What is the length of the MD5 hash?
A. 32 character B. 64 byte
C. 48 char
D. 128 kb
-
Question 310:
Bill is a security analyst for his company. All the switches used in the company's office are Cisco switches. Bill wants to make sure all switches are safe from ARP poisoning. How can Bill accomplish this?
A. Bill can use the command: ip dhcp snooping.
B. Bill can use the command: no ip snoop.
C. Bill could use the command: ip arp no flood.
D. He could use the command: ip arp no snoop.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V7 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.