312-49V10 Exam Details
-
Exam Code
:312-49V10 -
Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10) -
Certification
:EC-COUNCIL Certifications -
Vendor
:EC-COUNCIL -
Total Questions
:1028 Q&As -
Last Updated
:Jan 23, 2026
EC-COUNCIL 312-49V10 Online Questions & Answers
-
Question 1:
To reach a bank web site, the traffic from workstations must pass through a firewall. You have been asked to review the firewall configuration to ensure that workstations in network 10.10.10.0/24 can only reach the bank web site 10.20.20.1 using https.
Which of the following firewall rules meets this requirement?
A. If (source matches 10.10.10.0/24 and destination matches 10.20.20.1 and port matches 443) then permit
B. If (source matches 10.10.10.0/24 and destination matches 10.20.20.1 and port matches 80 or 443) then permit
C. If (source matches 10.20.20.1 and destination matches 10.10.10.0/24 and port matches 443) then permit
D. If (source matches 10.10.10.0 and destination matches 10.20.20.1 and port matches 443) then permit -
Question 2:
Which of the following is found within the unique instance ID key and helps investigators to map the entry from USBSTOR key to the MountedDevices key?
A. ParentIDPrefix
B. LastWrite
C. UserAssist key
D. MRUListEx key -
Question 3:
You are a Penetration Tester and are assigned to scan a server. You need to use a scanning technique wherein the TCP Header is split into many packets so that it becomes difficult to detect what the packets are meant for. Which of the below scanning technique will you use?
A. Inverse TCP flag scanning
B. ACK flag scanning
C. TCP Scanning
D. IP Fragment Scanning -
Question 4:
CompanyXYZ has asked you to assess the security of their perimeter email gateway. From your office in New York, you craft a specially formatted email message and send it across the Internet to an employee of CompanyXYZ. The employee of CompanyXYZ is aware of your test. Your email message looks like this:
From: jim_miller@companyxyz.com To: michelle_saunders@companyxyz.com Subject: Test message Date: 4/3/2017 14:37
The employee of CompanyXYZ receives your email message.
This proves that CompanyXYZ's email gateway doesn't prevent what?
A. Source code review
B. Reviewing the firewalls configuration
C. Data items and vulnerability scanning
D. Interviewing employees and network engineers -
Question 5:
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?
A. A user with username bad_guy has logged into the WordPress web application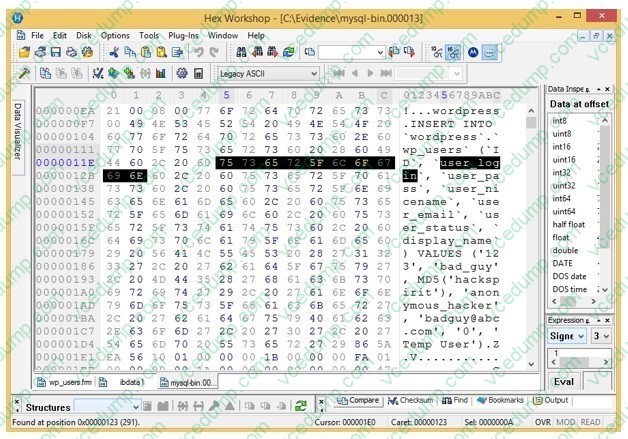
B. A WordPress user has been created with the username anonymous_hacker
C. An attacker with name anonymous_hacker has replaced a user bad_guy in the WordPress database
D. A WordPress user has been created with the username bad_guy -
Question 6:
As part of extracting the system data, Jenifer has used the netstat command. What does this tool reveal?
A. Status of users connected to the internet
B. Net status of computer usage
C. Information about network connections
D. Status of network hardware -
Question 7:
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing. What document describes the specifics of the testing, the associated violations, and essentially protects both the organization's interest and your liabilities as a tester?
A. Project Scope
B. Rules of Engagement
C. Non-Disclosure Agreement
D. Service Level Agreement -
Question 8:
Jim's company regularly performs backups of their critical servers. But the company cannot afford to send backup tapes to an off-site vendor for long-term storage and archiving. Instead, Jim's company keeps the backup tapes in a safe in the office. Jim's company is audited each year, and the results from this year's audit show a risk because backup tapes are not stored off-site.
The Manager of Information Technology has a plan to take the backup tapes home with him and wants to know what two things he can do to secure the backup tapes while in transit?
A. Encrypt the backup tapes and use a courier to transport them.
B. Encrypt the backup tapes and transport them in a lock box
C. Degauss the backup tapes and transport them in a lock box.
D. Hash the backup tapes and transport them in a lock box. -
Question 9:
Which of the following does Microsoft Exchange E-mail Server use for collaboration of various e-mail applications?
A. Simple Mail Transfer Protocol (SMTP)
B. Messaging Application Programming Interface (MAPI)
C. Internet Message Access Protocol (IMAP)
D. Post Office Protocol version 3 (POP3) -
Question 10:
You need to deploy a new web-based software package for your organization. The package requires three separate servers and needs to be available on the Internet.
What is the recommended architecture in terms of server placement?
A. All three servers need to be placed internally
B. A web server and the database server facing the Internet, an application server on the internal network
C. A web server facing the Internet, an application server on the internal network, a database server on the internal network
D. All three servers need to face the Internet so that they can communicate between themselves
Related Exams:
-
112-51
EC-Council Certified Network Defense Essentials (NDE) -
212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0 -
212-77
EC-Council Certified Linux Security -
212-81
EC-Council Certified Encryption Specialist (ECES) -
212-82
EC-Council Certified Cybersecurity Technician (C|CT) -
212-89
EC Council Certified Incident Handler (ECIH v3) -
312-38
EC-Council Certified Network Defender (CND) -
312-39
EC-Council Certified SOC Analyst (CSA) -
312-40
EC-Council Certified Cloud Security Engineer (CCSE) -
312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.