300-715 Exam Details
-
Exam Code
:300-715 -
Exam Name
:Implementing and Configuring Cisco Identity Services Engine (SISE) -
Certification
:CCNP Security -
Vendor
:Cisco -
Total Questions
:420 Q&As -
Last Updated
:Jan 06, 2026
Cisco 300-715 Online Questions & Answers
-
Question 1:
DRAG DROP
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco ISE. Drag and drop the commands from the left into sequence on the right. Not all options are used.
Select and Place:

-
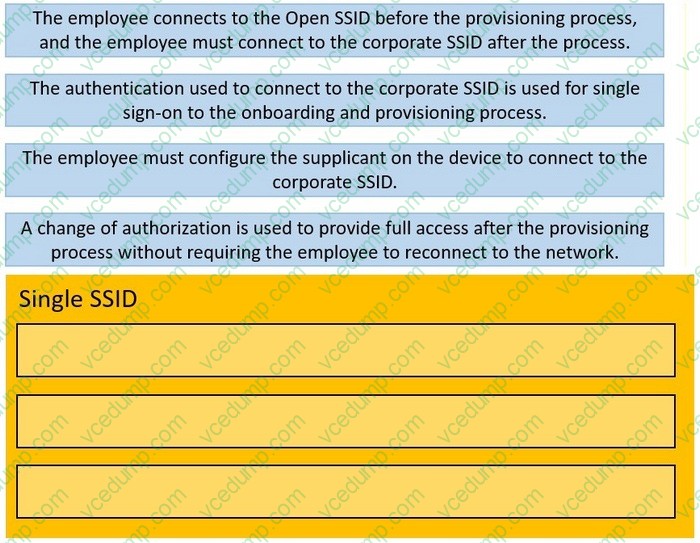
Question 2:
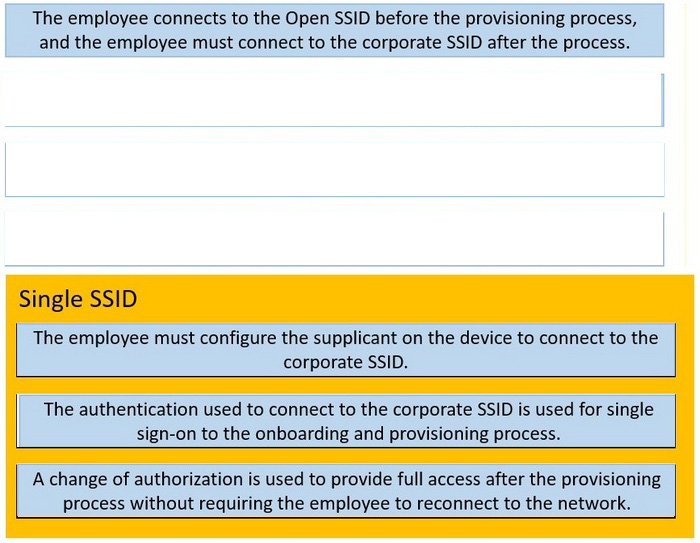
DRAG DROP
Drag and drop the steps of the onboarding process from the left into the order they authenticate on the right. Not all options are used.
Select and Place:
-
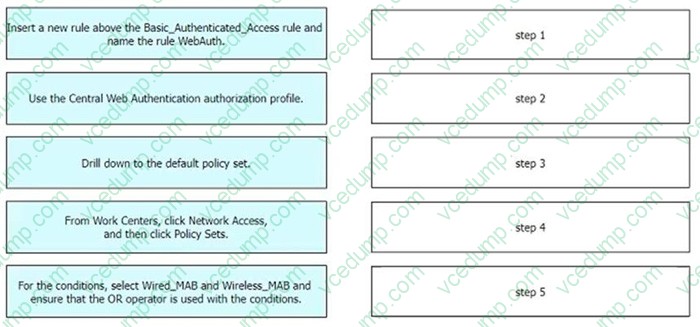
Question 3:
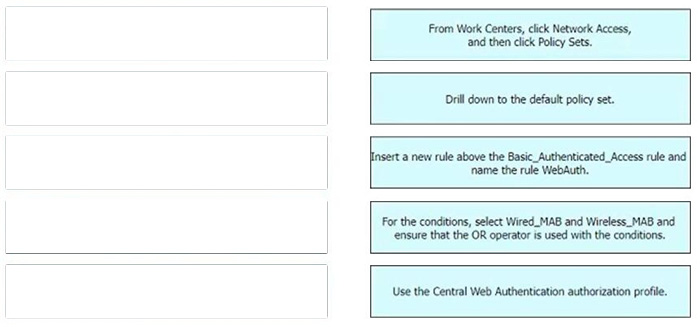
DRAG DROP
Refer to the exhibit.

An engineer must create a web authentication access policy in Cisco ISE that matches the exhibit. Drag and drop the configuration steps from the left into sequence on the right to accomplish this task.
Select and Place:
-
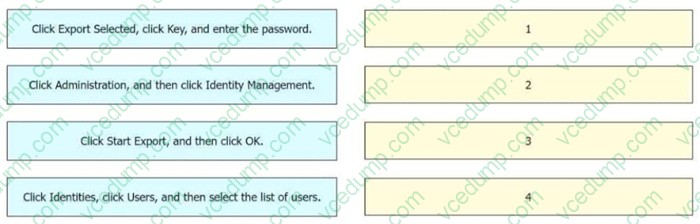
Question 4:
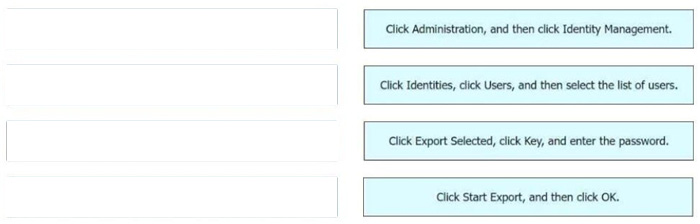
DRAG DROP
An engineer needs to export a file in CSV format, encrypted with the password C1$c0438563935, and contains users currently configured in Cisco ISE. Drag and drop the steps from the left into the sequence on the right to complete this task.
Select and Place:
-
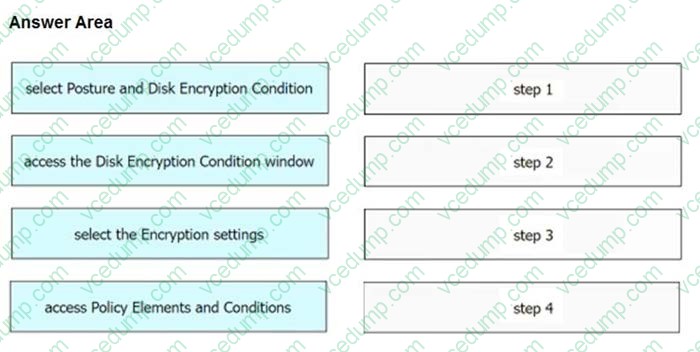
Question 5:
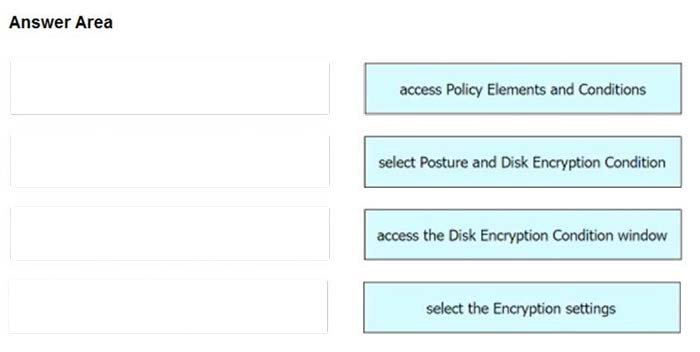
DRAG DROP
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
Select and Place:
-
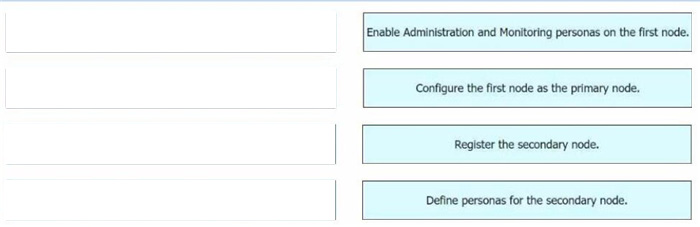
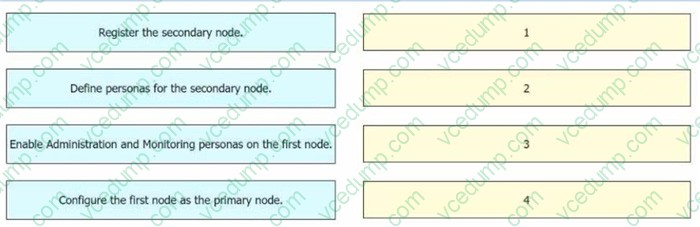
Question 6:
DRAG DROP
Drag and drop the configuration steps from the left into the sequence on the right to install two Cisco ISE nodes in a distributed deployment.
Select and Place:
-
Question 7:
What is a difference between RADIUS versus TACACS+ with regards to packet encryption?
A. TACACS+ encrypts the entire body of the packet, and RADIUS encrypts the username and password in the access-request packet.
B. RADIUS encrypts the entire body of the packet, and TACACS+ encrypts the username and password in the access-request packet.
C. RADIUS encrypts the entire body of the packet, and TACACS+ encrypts only the password in the access-request packet.
D. TACACS+ encrypts the entire body of the packet, and RADIUS encrypts only the password in the access-request packet. -
Question 8:
The Cisco Wireless LAN Controller and guest portal must be set up in Cisco ISE. These configurations were performed:
configured all the required Cisco Wireless LAN Controller configurations added the wireless controller to Cisco ISE network devices created an endpoint identity group configured credentials to be sent by email configured the SMTP server configured an authorization profile with redirection to the guest portal and redirected the access control list configured an authentication policy for MAB users created an authorization policy
Which two components must be created to complete the configuration? (Choose two.)
A. sponsor group
B. hotspot guest portal
C. sponsor portal
D. self-registered guest portal
E. guest type -
Question 9:
An administrator must provide wired network access to unidentified Cisco devices that fail 802.1X authentication. Cisco ISE profiling services must be configured to gather Cisco Discovery Protocol and LLDP endpoint information from a Cisco switch. These configurations were performed:
configured switches to accept SNMP queries from Cisco ISE enabled Cisco Discovery Protocol and LLDP on the switches added the switch as a NAD to Cisco ISE
What must be enabled to complete the configuration?
A. SNMP traps on the switch
B. SNMP MIBs in Cisco ISE
C. SNMP Trap probe in Cisco ISE
D. SNMP Query probe in Cisco ISE -
Question 10:
An administrator is editing a csv list of endpoints and wants to reprofile some of the devices indefinitely before importing the list into Cisco ISE. Which field and Boolean value must be changed for the devices before the list is reimported?
A. Identity Group Assignment field and Static Assignment field set to the value FALSE
B. Policy Assignment field and Static Assignment field set to the value TRUE
C. Policy Assignment field and Static Assignment field set to the value FALSE
D. Identity Group Assignment field and Static Assignment field set to the value TRUE
Related Exams:
-
300-710
Securing Networks with Cisco Firepower (SNCF) -
300-715
Implementing and Configuring Cisco Identity Services Engine (SISE) -
300-720
Securing Email with Cisco Email Security Appliance (SESA) -
300-725
Securing the Web with Cisco Web Security Appliance (SWSA) -
300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN) -
300-735
Automating and Programming Cisco Security Solutions (SAUTO) -
300-740
Designing and Implementing Secure Cloud Access for Users and Endpoints -
350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-715 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.