Exam Details
Exam Code
:210-255Exam Name
:Cisco Cybersecurity OperationsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:224 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-255 Questions & Answers
-
Question 31:
You have identified a malicious file in a sandbox analysis tool. Which piece of file information from the analysis is needed to search for additional downloads of this file by other hosts?
A. file name
B. file hash value
C. file type
D. file size
-
Question 32:
Refer to the exhibit.
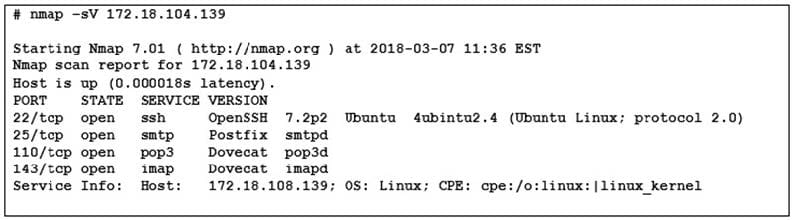
What does the output indicate about the server with IP address 172.18.104.139?
A. open port of an FTP server
B. open ports of a web server
C. running processes of the server
D. open ports of an email server
-
Question 33:
Which option is missing a malware variety per VERIS enumerations?
A. backdoor, command and control, denial or service attack
B. adware, brute force, client-side attack
C. packet sniffer, password dumper, scan network
D. abuse of functionality, cache poisoning, remote file inclusion
-
Question 34:
How do you verify that one of your hosts is potentially compromised based on their communication destinations?
A. Search the communication destinations of the host in the Talos IP and Domain Reputation Center.
B. Analyze how much traffic the host sent and received from each IP address or domain.
C. See if any Stealthwatch alarms were triggered for the host communicating with internal hosts.
D. Check the Firepower appliance to see if malicious files were downloaded.
-
Question 35:
Refer to the exhibit. Which item is depicted in this output?
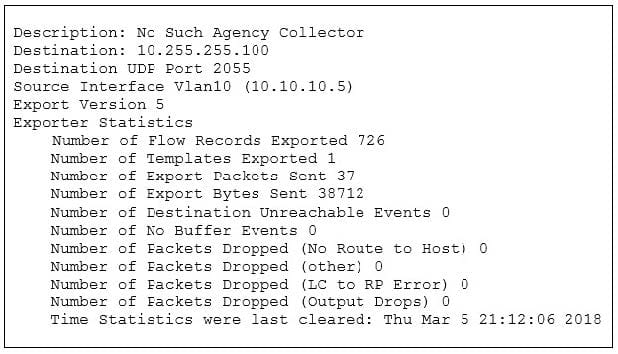
A. Windows Security audit log
B. NetFlow data
C. packet capture exported text
D. VLAN 10 traffic
-
Question 36:
Which concept is used to understand instances of the same cybersecurity event occurring over the course of a few weeks that could be linked together through multiple illustrations and then linked back to the same adversary?
A. threat model
B. intrusion threat intelligence model
C. compliance and Intrusion model
D. diamond model of intrusion
-
Question 37:
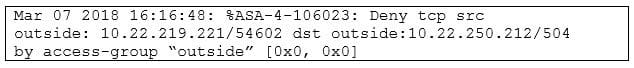
Refer to the exhibit. What device is this taken from?
A. web proxy
B. IDS
C. firewall
D. NetFlow
-
Question 38:
Which CVSS Attach Vector metric value means that the vulnerable component is not bound to the network stack and the path of the attacker is via read/write/execute capabilities?
A. network
B. physical
C. local
D. adjacent
-
Question 39:

Refer to the exhibit. Which event is represented by this configuration?
A. The ext3-test.img is being converted from read-only to read-write for analysis.
B. A drive is being mounted using ext3-test.img file as a source.
C. A /mnt/test directory is being created in the ext3-test.img file.
D. The ext3-test.img file was found on the ext4 filesystem in the /mnt/test directory.
-
Question 40:
Which incident handling phase contains evidence gathering and handling?
A. containment, eradication, and recovery
B. identification
C. post incident
D. preparation
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-255 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.