210-255 Exam Details
-
Exam Code
:210-255 -
Exam Name
:Cisco Cybersecurity Operations -
Certification
:Cisco Certifications -
Vendor
:Cisco -
Total Questions
:224 Q&As -
Last Updated
:Dec 07, 2025
Cisco 210-255 Online Questions & Answers
-
Question 1:
When evidence is collected, what does NIST SP800-86 specify as a guideline to follow for the order of collection?
A. order of volatility
B. order of importance
C. most difficult to access first
D. least difficult to access first -
Question 2:
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise. Which kind of evidence is this IP address?
A. indirect evidence
B. best evidence
C. forensic evidence
D. corroborative evidence -
Question 3:
What does 5-typle refer to?
A. set of five different values that comprise a SSL connection
B. set of five different values that comprise a HTTPS connection
C. set of five different values that comprise a UDP connection
D. set of five different values that comprise a TCP/IP connection -
Question 4:
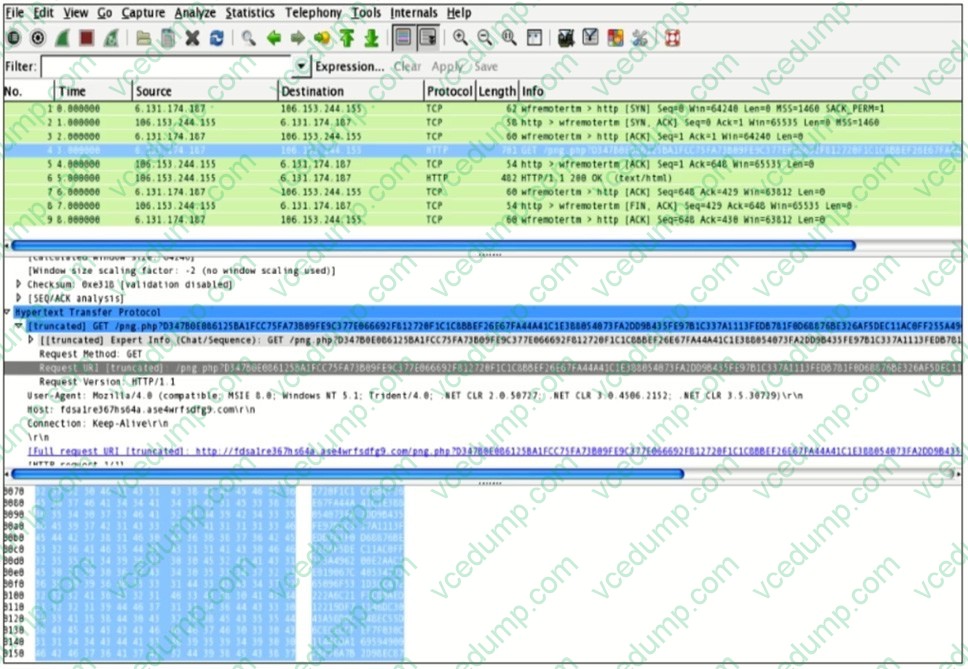
Refer to the exhibit. Which information is interesting about the HTTP GET shown?
A. The User-Agent is Mozilla/4.0
B. The HTTP GET is encoded
C. timestamps
D. The protocol is TCP -
Question 5:
Why do SOC analysts use 5-tuple?
A. to identify the requirements for creating a functional network connection between two laptops
B. to identify the requirements for creating a wireless network connection between an access point and a host
C. to identify the requirements for creating a data center using best practices
D. to identify the requirements for creating a secure network connection between two or more remote and local machines -
Question 6:
In which type of analysis is all data used for the analysis known beforehand?
A. dynamic
B. statistical
C. probabilistic
D. deterministic -
Question 7:
Which component of the Linux ext4 file system records the intentions of changes made to the main part of the file system?
A. MBR
B. swap
C. journal
D. checksum -
Question 8:
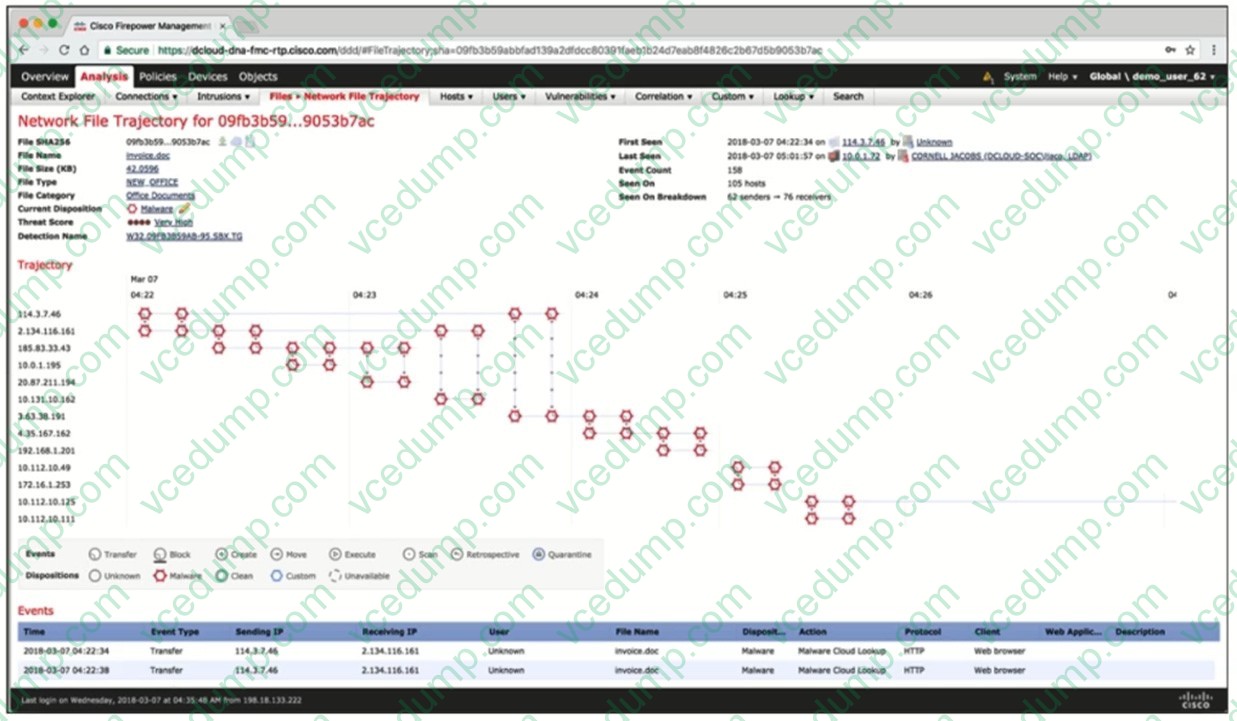
Refer to the exhibit. Which description of the IP addresses under the Trajectory section is true?
A. victim systems running Microsoft Word
B. spoofed IP addresses
C. victim systems running Adobe Acrobat
D. attackers -
Question 9:
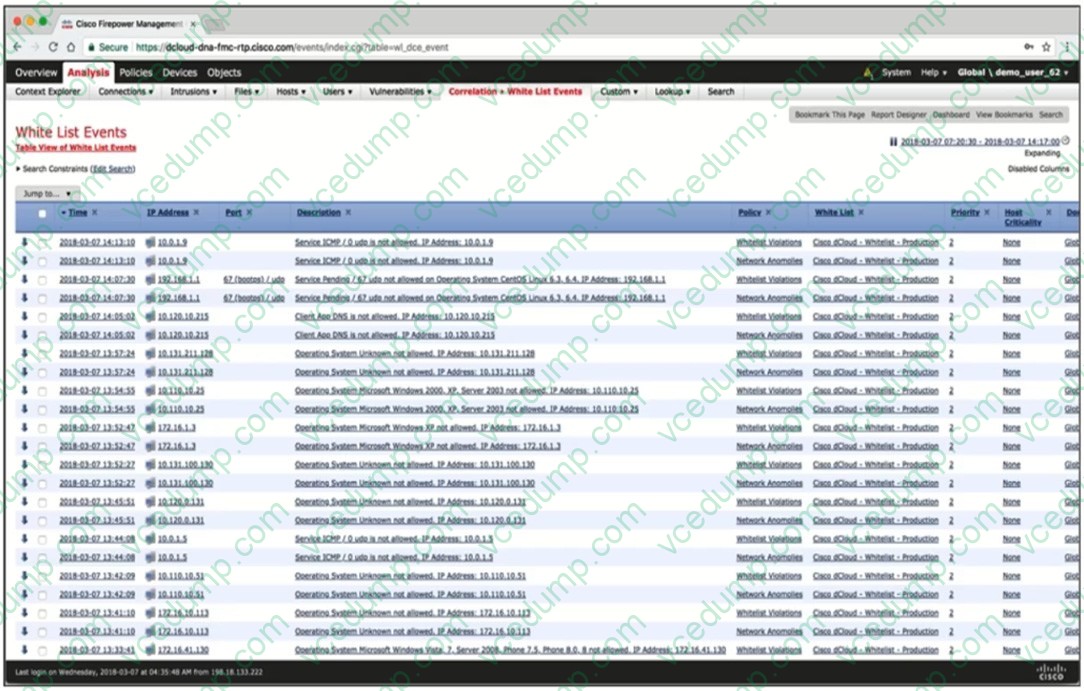
Refer to the exhibit. Which function of the Cisco Firepower Management Console correlation rules does the screenshot demonstrate?
A. operating system whitelist events
B. whitelisted true positive events
C. whitelisted false positive events
D. whitelisted command and control communication events -
Question 10:
What is missing from the data correlated by using security intelligence?
A. security intelligence categories
B. time stamps of data transmission at the frame level
C. ports
D. time stamps of data transmission at the packet level
Related Exams:
-
352-011
Cisco Certified Design Expert Practical -
500-052
Cisco Unified Contact Center Express -
500-173
Designing the FlexPod Solution (FPDESIGN) -
500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions -
500-210
SP Optical Technology Field Engineer Representative -
500-220
Engineering Cisco Meraki Solutions (ECMS) v2.2 -
500-230
Cisco Service Provider Routing Field Engineer -
500-240
Cisco Mobile Backhaul for Field Engineers -
500-275
Securing Cisco Networks with Sourcefire FireAMP Endpoints (SSFAMP) -
500-285
Securing Cisco Networks with Sourcefire Intrusion Prevention System
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-255 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.