Exam Details
Exam Code
:210-255Exam Name
:Cisco Cybersecurity OperationsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:224 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-255 Questions & Answers
-
Question 11:
Which tool helps security administrators identify threats in their network?
A. Cisco Cloudlock
B. Cisco Email Security
C. Cisco Umbrella
D. Security Threat Intelligence
-
Question 12:
Which evidence is considered to be the most volatile?
A. disk
B. registers and cache
C. removable media
D. logging
-
Question 13:
Which technology generates events utilizing proxy logs?
A. Firepower
B. Email Security Appliance
C. Stealthwatch
D. Web Security Appliance
-
Question 14:
Which file system has share and file permissions?
A. NTFS
B. FAT
C. TMPFS
D. Streams
-
Question 15:
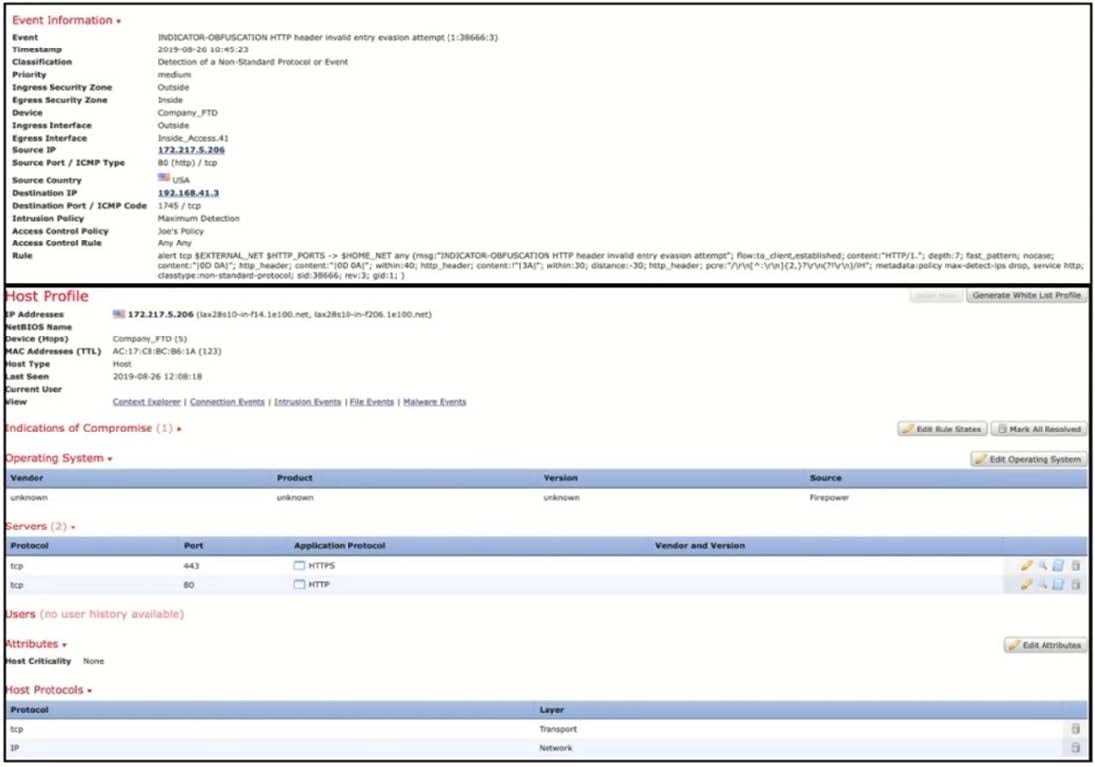
Refer to the exhibit. Which impact flag is generated by the Cisco Firepower Management Center for this event?
A. 1, red
B. 5, gray
C. 2, orange
D. 3, yellow
-
Question 16:
What can be addressed when using retrospective security techniques?
A. why the malware is still in our network
B. if the affected host needs a software update
C. origin of the malware
D. if the affected system needs replacement
-
Question 17:
Which description of probabilistic analysis is true?
A. probable proof of a user's identity
B. lack of proof of a user's identity
C. definitive proof of a user's identity
D. false proof of a user's identity
-
Question 18:
Which two goals of data normalization are true? (Choose two.)
A. Eliminate update anomalies.
B. Eliminate redundant data.
C. Increase integrity of data.
D. Increase redundancy of data.
E. Increase data availability.
-
Question 19:
Refer to the exhibit.
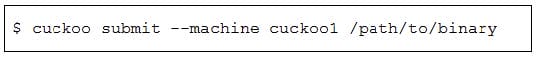
Which event is occurring?
A. A URL is being evaluated to see if it has a malicious binary.
B. A binary on device cuckoo1 is being submitted for evaluation.
C. A binary named “submit” is running on cuckoo1.
D. A binary is being submitted to run on device cuckoo1.
-
Question 20:
Which command filters a port?
A. tcp.port equals 25
B. tcp.port is 25
C. tcp.port != 25
D. !tcp.port==25
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-255 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.