Exam Details
Exam Code
:210-255Exam Name
:Cisco Cybersecurity OperationsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:224 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-255 Questions & Answers
-
Question 191:
Refer to the exhibit. Which application protocol is in this PCAP file?
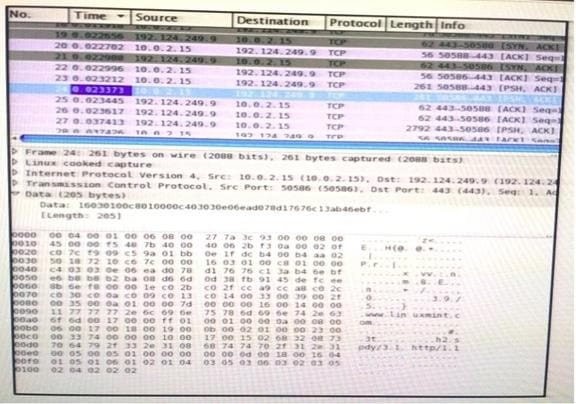
A. TCP
B. SSH
C. HTTP
D. SSL
-
Question 192:
You see confidential data being exfiltrated to an IP address that is attributed to a known Advanced Persistent Threat group. Assume that this is part of a real attach and not a network misconfiguration. Which category does this event fall under as defined in the Diamond Model of Intrusion?
A. reconnaissance
B. weaponization
C. delivery
D. action on objectives
-
Question 193:
Which network device creates and sends the initial packet of a session?
A. source
B. origination
C. destination
D. network
-
Question 194:
When performing threat hunting against a DNS server, which traffic toward the affected domain is considered a starting point?
A. HTTPS traffic
B. TCP traffic
C. HTTP traffic
D. UDP traffic
-
Question 195:
Which type of analysis allows you to see how likely an exploit could affect your network?
A. descriptive
B. casual
C. probabilistic
D. inferential
-
Question 196:
You have run a suspicious file in a sandbox analysis tool to see what the file does. The analysis report shows that outbound callouts were made post infection. Which two pieces of information from the analysis report are needed or required to investigate the callouts? (Choose two.)
A. file size
B. domain names
C. dropped files
D. signatures
E. host IP addresses
-
Question 197:
Which option filters a LibPCAP capture that used a host as a gateway?
A. tcp|udp] [src|dst] port
B. [src|dst] net
[{mask }|{len }] C. ether [src|dst] host
D. gateway host
-
Question 198:
What information from HTTP logs can be used to find a threat actor?
A. referer
B. IP address
C. user-agent
D. URL
-
Question 199:
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. Which term defines the initial event in the NIST SP800- 61 r2?
A. instigator
B. precursor
C. online assault
D. trigger
-
Question 200:
Which element is part of an incident response plan?
A. organizational approach to incident response
B. organizational approach to security
C. disaster recovery
D. backups
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-255 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.